
Websites on the internet gather information from browsers visitors use, with many of them creating a "fingerprint" to track users.
This is called browser fingerprinting. And when that method is enhanced a bit, researchers at Cambridge University’s Computer Laboratory developed an insidious fingerprinting attack that allows iOS and Android devices to be tracked across the internet.
The method is so simple to execute, but virtually impossible to stop without direct intervention from Apple or Google.
The researchers call the method as 'SensorID', and what it does, is creating fingerprint using data gathered from the sensors of a smartphone.
Presenting their finding at the IEEE Symposium on Security and Privacy 2019 (IEEE S&P'19) on May 21th, 2019, the researchers said that all iPhones, Pixel 2 or 3, are vulnerable.
And according to their full research paper and their non-technical explanation, high-end Android devices can also be vulnerable as well.
How SensorID works, is by utilizing sensors available on most smartphones.
From accelerometers, gyroscopes and magnetometers, smartphones can detect many things from their surroundings. While these sensors record a lot of data, they may not be as accurate as dedicated sensors.
This can be caused by imperfections on the sensors or when they are put together on the assembly lines.
For this particular reason, device manufacturers calibrate their devices by measuring and correcting the errors for each device and encoding the calibration data in the device's firmware.
In most cases, the calibration data can uniquely identify the smartphone, hence the name 'fingerprint'.
And with this SensorID, the researcher said that the calibration data is what gave them the fingerprint for the phone.
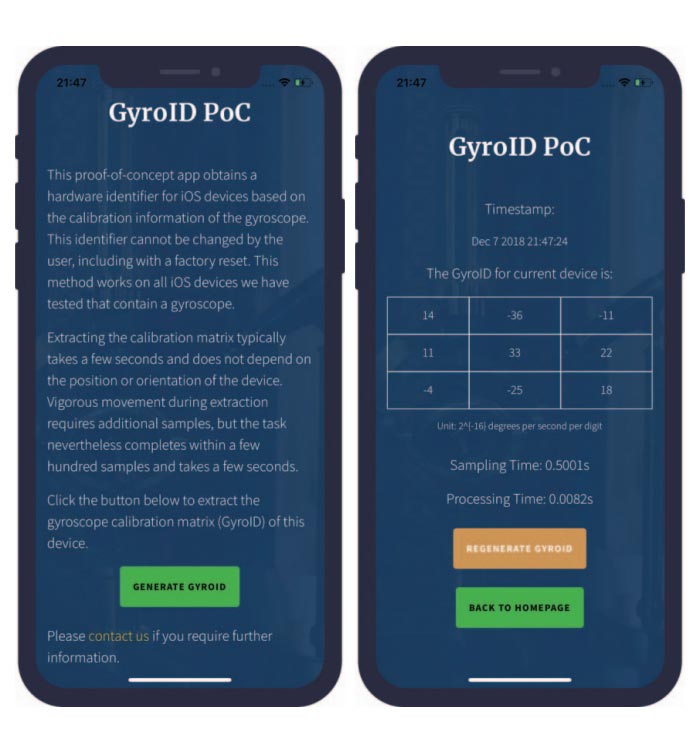
The attack can be impossible to stop, due to the fact that the data needed to create the fingerprint is already available for free on every website or app, with the researchers pointing out that the sensor data that’s the basis for the attack is known to be gathered by at least 2,653 of Alexa’s top 100,000 websites.
It’s completely unprotected, and anyone can generate fingerprints without doing any action other than visiting a website or using an app.
In most cases, it takes from less than a second to a a few seconds at most, to create the fingerprint after a website is visited or an app is opened.
The fingerprint that’s created is also very robust.
Typical device fingerprints are based on data gathered from the browser, and can be defeated by just switching to a different browser. But as for SensorID, it is based on data from the sensors which remains unchanged no matter which browser is used at any given time and cannot be changed even with a factory reset.
As a result, the researchers determined that Safari, Chrome, Firefox, Opera, Brave and Firefox Focus are all vulnerable to their attack.
Read: Cookies, Browser Fingerprinting, And How You Can Delay The Death Of Online Privacy
According to the researchers, iPhones are more susceptible than Android phones to SensorID, because Apple products are high-end on the market, and all of their phones contain calibrated accelerometers and magnetometers.
What this means, virtually every iPhone has a unique SensorID that can be used to track every website visited and every app used on the device.
Fortunately, Apple issued a patch to this flaw with iOS 12.2.
As for Android phones. the good news is that the phones are generally less susceptible to attack because Android has so many variations with most are low-end smartphones.
The researchers were only able to test a small number of Android phones and, with a notable exception, were unable to create a fingerprint from the phones they tested.
However, the researchers demonstrated that a fingerprint can be created from the accelerometer in a Pixel 2 or 3.
They informed Google in December 2018 and as of May 2019, Google is still “investigating the issue” and hasn’t released a patch.