Being an app developer is fun, but it isn't an easy job. Dealing with codes, developers need to race against time.
This is why any solution that can cut down the development time, and costs, is welcome. One of which, is the SDK (software development kit) from Mintegral, a Chinese-based advertising platform.
What it does, is allowing developers to embed ads inside their apps with just a few lines of codes.
But things seemed to be more than just that.
In a report from security firm Snyk, it was revealed that a malicious code exists inside the popular iOS SDK used by more than 1,200 iOS applications.
Mobile apps that show ads, regularly use multiple advertising SDK's to diversify their ads and monetization strategies. And the malicious code inside Mintegral's iOS SDK contains malicious features that wait for a tap on any ad that's not its own
According to Snyk,when an ad tap happens, the SDK will hijack the click referral process, making it appear to iOS that the user clicked on one of its ads, instead of a competitor's.
In other words, Mintegral can effectively rob revenue of others.
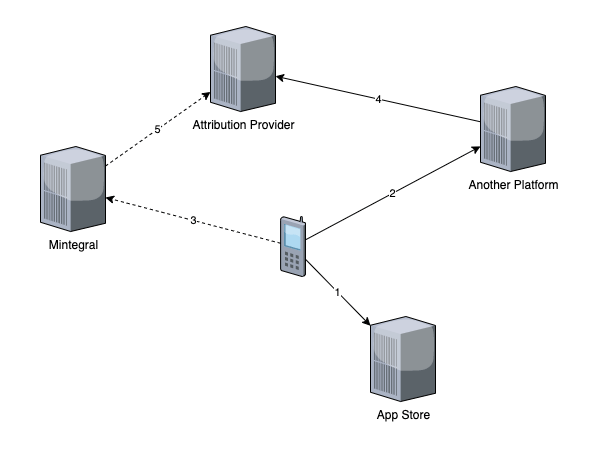
The malicious process works like this:
- Users click on a link from an in-app advertisement served by a non-Mintegral ad network.
- The ad network's SDK will send the click information to its backend platform.
- The SDK intercept the clock via a code injected into the iOS event handler, using a method called 'swizzling'. Mintegral logs the click data to its server.
- The ad network registers a click notification with the attribution provider.
- Mintegral registers a click notification with the attribution provider as well.
Mintegral uses "many interesting techniques" to hide the above malicious bahavior of the SDK.
"As we can see, they activate hooks only on specific applications in specific regions which helped the malicious code stay there for more than one year without any attention."
Snyk did not mention any iOS apps using the Mintegral SDK. However, the company did say that the first version of the SDK that was malicious, was v5.51, released on July 17, 2019.
Things get worse after that.
According to Snyk, while it appears that Mintegral is engaging in ad fraud, the SDK also contains some other malicious functions:
- Grabbing the URL that was requested, which could potentially include identifiers or other sensitive information.
- The headers of the request that was made could include authentication tokens and other sensitive information.
- The app code can see where requests are originated, which could then be used to identify user patterns.
- The ability to collect device's Identifier for Advertisers (IDFA), which can be then be used to identify users' IMEI.
This information is logged and then sent to a remote server.
"The attempts by Mintegral to conceal the nature of the data being captured, both through anti-tampering controls and a custom proprietary encoding technique, are reminiscent of similar functionality reported by researchers that analyzed the Tik Tok app," said Alyssa Miller, Application Security Advocate at Snyk.
"In the case of SourMint [codename given by Snyk to the Mintegral iOS SDK), the scope of data being collected is greater than would be necessary for legitimate click attribution."