
There is hardly any way to stay a 100 percent safe on the internet-connected world. Hackers can come in many forms, and one the worst is when it's backed by the government.
Researchers from Electronic Frontier Foundation (EFF) and security firm Lookout have discovered a mobile espionage that has been around from at least 2012. Dubbed the 'Dark Caracal', it has claimed to have stolen hundreds of gigabytes of data, including personally identifiable information and intellectual property, from thousands of victims.
And here, the campaign has accidentally revealed itself, thanks to the open internet.
When some of its files were leaked to the World Wide Web, the researchers were able to trace them back to a building in Beirut owned by the Lebanese General Directorate of General Security (GDGS), one of the country's intelligence agencies.
"Based on the available evidence, it's likely that the GDGS is associated with or directly supporting the actors behind Dark Caracal," the report reads.
The researchers have also identified at least four other different personas that are associated with Dark Caracal. They are: Nancy Razzouk, Hassan Ward, Hadi Mazeh, and Rami Jabbour.

"During July 2017, Dark Caracal’s internet service provider took the adobeair[.]net command and control server offline. Within a matter of days, we observed it being re-registered to the email address op13@mail[.]com with the name Nancy Razzouk. This allowed us to identify several other domains listed under the same WHOIS email address information, running similar server components. "
Here, the Dark Caracal has been conducting multi-platform and worldwide cyber-espionage campaigns.
But since 2012, the group has run tens of hacking campaigns that were mainly targeting Android users in at least 21 countries.
The data stolen include documents, call records, text messages, audio recordings, secure messaging client content, browsing history, contact information, photos, location data, and other information that allows the APT group to identify their targets and have a look at their personal lives.
The Dark Caracal relied on social engineering on social media networks, especially on Facebook groups and WhatsApp messages. On those platforms, the hackers encouraged users to visit websites they control.
"One of the interesting things about this ongoing attack is that it doesn’t require a sophisticated or expensive exploit. Instead, all Dark Caracal needed was application permissions that users themselves granted when they downloaded the apps, not realizing that they contained malware," said Cooper Quintin, an EFF Staff Technologist. "This research shows it’s not difficult to create a strategy allowing people and governments to spy on targets around the world."
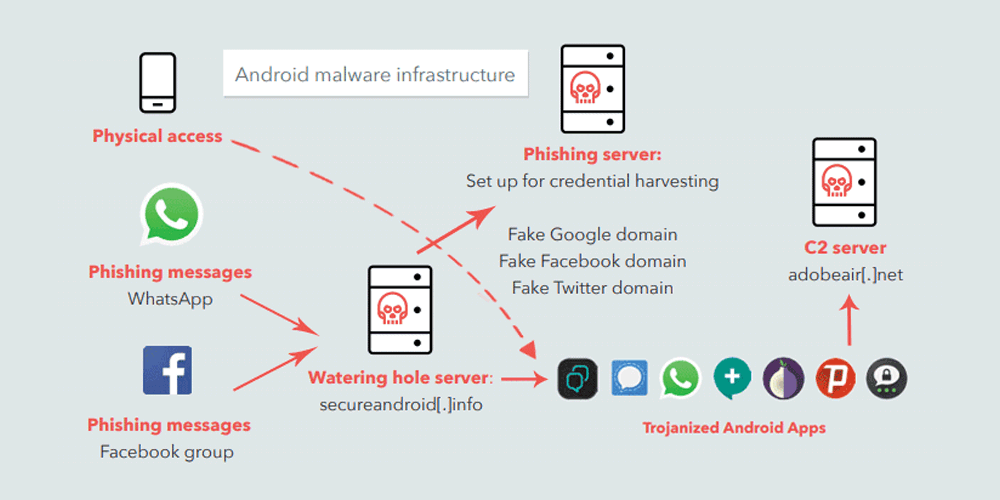
And once a person fell as victim by landing on the malicious websites, the victim were shown fake updates to secure messenger apps, including WhatsApp, Signal, Telegram, and Orbot.
Downloading those updates, will automatically download the Dark Caracal's malware, dubbed 'Pallas'.
The malware is then capable of taking pictures using the camera, stealing data, spy on running apps, recording video and audio, get location data, stealing text messages, and even steal two-factor authentication codes, from the victims' devices.
"Pallas samples primarily rely on the permissions granted at the installation in order to access sensitive user data. However, there is functionality that allows an attacker to instruct an infected device to download and install additional applications or updates." report says. "Theoretically, this means it’s possible for the operators behind Pallas to push specific exploit modules to compromised devices in order to gain complete access."
Dark Caracal also used FinFisher, which is a secret surveillance tool that is often marketed to law enforcement and government agencies, and a newly discovered desktop spyware tool, dubbed CrossRAT, which can infect Windows, Linux, and OS X operating systems.
As a precaution, the best way for users to protect themselves from this type of attacks, is to never download apps from places other than Google's Play Store.
Related: Researchers Discovered 'Skygofree', A Malware That Could Do Anything To Infected Devices