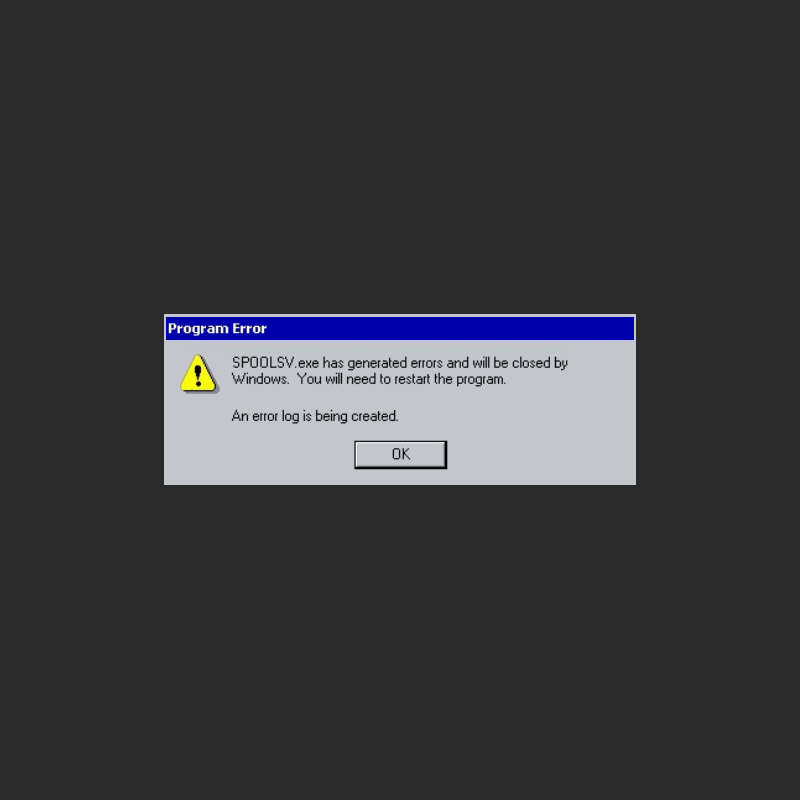
As an operating system, Microsoft Windows needs to support a lot of peripheral devices, to also allow users manage things through them as easy as possible.
And here, every versions of Windows has a particular file that manages commands to print documents. That file has past unnoticed by security researchers, before security firm SafeBreach Labs took a closer look at the file. And after diving in deeper, the file also has a fatal bug.
The file that is called 'Print Spooler Service', is two decades old.
First, the researchers found that the file has a denial of service vulnerability the researchers reported earlier this 2020. When exploited, the file can crash the spooler service.
The bug was found on the Print Spooler Service on Windows 10, and all the way back to the business-oriented Windows 2000, which was first released in the year 2000.
"We got intrigued, so we continued to dive in,” said Peleg Hadar, senior security researcher at SafeBreach Labs.
And this was when the researchers found the second flaw, which could allow hackers to gain system privileges on a PC.
Print spooler is essentially an executable file that manages the printing process inside Windows. The primary component of the printing interface in Windows, is this print spooler.
According to Hadar and Bar on their whitepaper, management of printing in Windows involves retrieving the location of the correct printer driver, loading that driver, spooling high-level function calls into a print job, scheduling the print job for printing, and so forth. The spooler is loaded at system startup and continues to run until the operating system is shut down.
“The Print Spooler code is at least 20 years old. In general, older code tends to contain old bugs and might be more risky because of security flaws but, in fact, there were only few discovered vulnerabilities in the spooler service during the last 20+ years,” Hadar said.
After Microsoft patched the issue in May (CVE-2020-1048), Hadar and his colleague, Tomer Bar, reverse-engineered the patch and found a way to bypass the patch and re-exploit the vulnerability.
Microsoft assigned this vulnerability a new identification number (CVE-2020-1337), and is working to deliver the patch on its August 2020 Patch Tuesday.
Hadar and Bar present the findings at the 2020 Black Hat hacking conference. The two researchers also release a proof-of-concept code on GitHub, which is designed to help detect attacks on the spooler service.
"We wanted to get people to think of a wider approach on how these kinds of issues can be mitigated," Hadar said.
The most famous malware that has abused Windows' print spoiler service, was Stuxnet.
The computer worm made headlines all around the world after hackers managed to use it to sabotage centrifuges at an Iranian nuclear facility in 2010.
It's believed that the malware was developed jointly by the U.S. and Israel as a cyberweapon to cripple enemies' computer network, primarily developed to cause substantial damage to Iran's nuclear facility.
It was reported that Stuxnet was the two countries' method to at least delay Iran's nuclear programs. The two fear that the facility could eventually help Iran develop its own nuclear weapons.
As a malware, Stuxnet is extremely sophisticated, and capable of exploiting previous unknown zero-day vulnerabilities to infect computers and to spread.
Stuxnet reportedly ruined almost one fifth of Iran's nuclear centrifuges, and when spread to the internet, the malware has targeted industrial control systems, and infected some 200,000 computers and caused 1,000 machines to physically degrade.
Liam O’Murchu, a security specialist who investigated Stuxnet, was surprised at the longevity of his spooler service issue.
“It is amazing that the print spooler code appears to have survived untouched from when Stuxnet was discovered over 10 years ago through to today, and may in fact date back 20 years,” said O’Murchu, director of the security technology and response group at Symantec.