
Apple often put its pride above anything else. For reasons, Apple is more matured than most of its direct competitors.
This makes it kind of shy when disclosing its weaknesses, or when bugs were found on its products. When three zero-day bugs were found recently for example, it was a rare admission by Apple to properly explain the weaknesses.
And this pride is often extended even when concerning fixes to its products.
In this case, in iOS 14, Apple added a 'BlastDoor sandbox security system to iPhones and iPads to prevent attacks carried out with the iMessages messaging app.
Apple didn't share information on this new security addition. It was made public by Samuel Groß, a security researcher from Google's Project Zero, a Google security team tasked with finding vulnerabilities in commonly-used software.
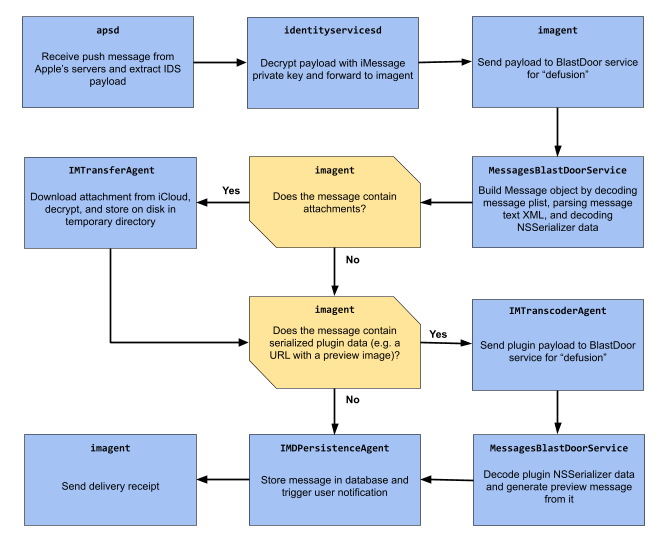
According to Groß in a blog post, this BlastDoor is like a tightly sandboxed service that's responsible for parsing all of the untrusted data in iMessages.
In software development, a sandbox is an environment that isolates codes away from the main program, or the production environment or repository. In this case, BlastDoor is a security service that executes code separately from the operating system.
While iOS has multiple sandbox mechanisms, BlastDoor is a new addition that operates only at the level of the iMessage app.
What BlastDoor does, is examining all incoming messages.
If code is present on the message, BlastDoor will unpack the content, and run the code in a secure and isolated environment.
This way, if there is a malicious code hidden inside a message, the code cannot interact or harm the underlying operating system, and cannot retrieve any user data.
The need for a service like BlastDoor is crucial, especially after several security researchers had pointed out in the past that Apple was doing a poor job in sanitizing messages in iMessage.
With BlastDoor service, Apple starting iOS 14 has moved the majority of the processing of complex and untrusted data to the sandbox.
BlastDoor with its other involved services can fine-grain sandboxing rules to be applied, like for example, to only the IMTransferAgent and apsd processes. With all services are properly sandboxed, Apple can ensure that it can thwart specific attack types, including those that are used by hackers to launch brute force attacks.
Groß found this BlastDoor service when investigating a message hacking campaign that targeted Al Jazeera staffers and journalists.
Groß was particularly curious about the sentence by Citizenlab, which said: "We do not believe that [the exploit] works against iOS 14 and above, which includes new security protections."
He wondered why the attack didn't work on iOS 14, and his investigation led to this discovery.
According to Groß, Apple's BlastDoor changes are "close to the best that could've been done given the need for backwards compatibility," and should certianly make the iMessage platform significantly more secure.
"It's great to see Apple putting aside the resources for these kinds of large refactorings to improve end users' security."
Groß said that the sandbox profile can be found in System/Library/Sandbox/Profiles/blastdoor.sb, and appears to be identical on iOS and macOS.