
Taylor Swift is an American singer and a songwriter. Best known for her narrative songs about her personal life, Swift has received widespread media coverage.
She started her debut at a very young age, and since then, her career escalated. It didn't take that long for Swift to become one of the best known singer worldwide. As "America's Sweetheart", and a "sex symbol" as mentioned by Bloomberg L.P., there is no doubt that images of her can attract a massive audience.
And this fact apparently, was leveraged by hackers.
According to a report from UK-based cybersecurity firm Sophos, a cryptocurrency-mining botnet is infecting computers with an image of Taylor Swift to spread its malware as widely as possible.
MyKingz, which is the operator, or also known as Smominru, DarkCloud, or Hexmen, leverages steganography in this Swift-inspired malware. This technique is a method to hide malicious files inside legitimate ones, obscuring their purposes.
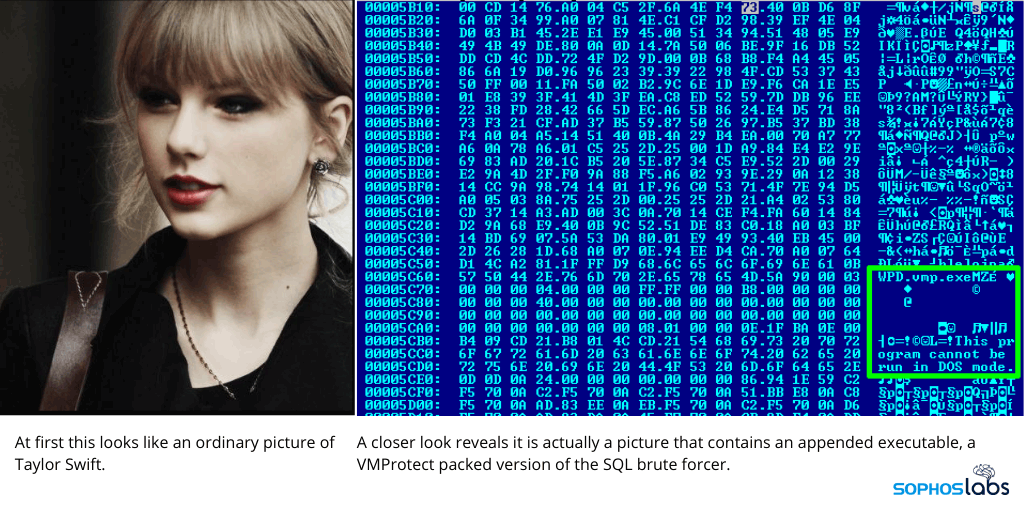
In this case, the hackers hide malicious executable file inside a legitimate JPEG image of Swift.
The malware uses the EternalBlue exploit and other exploits leaked by the Shadow Brokers.
Sophos warned that:
First gaining media coverage in 2017, MyKingz has been known to be the people behind some of the largest cryptocurrency-mining campaigns.
Using one of the most sophisticated scanning and infection mechanism ever observed in botnets, MyKingz targets MySQL, MS-SQL, Telnet, ssh, IPC, WMI, Remote Desktop (RDP), and also servers that run CCTV camera storage.
During its first months, MyKingz has infected more than 525,000 Windows systems, and earned at least $2.3 million worth of Monero (XMR), with victims coming from people in China, Taiwan, Russia, Brazil, USA, India, and Japan.
It’s estimated that MyKingz infects approximately 4,700 new systems every day.
"The infected endpoints we observed totaled about 43900 unique IP addresses," said Sophos.
Fortunately, attacks by MyKingz botnets follow a predictable pattern, and they are somehow redundant. For example, components of MyKingz botnets have similar self-update procedure. Everything repeats itself several times over, but using a variety of command combinations.
"MyKingz also redundantly employs a number of methods of establishing persistence on the infected host: It uses a bootkit, which launches the botnet immediately upon reboot; sets Registry run keys; and creates a number of Scheduled Tasks and WMI listeners," continued Sophos.
And here, the malware hidden inside Taylor Swift image is part of of MyKingz's constant refinement.
By hiding malware payload in plain sight, the hackers aim to spread its malware as vast and as fast as possible.