
Google the tech giant, is the backer of Android. For many reasons, its app should be on top of the most download apps on Android.
With more than 5 billion downloads, the Google app unleashes the power of Google Search, right into mobile devices. It allows users to search and browse anything, get personalized updates and more. The Google app is the app that should be available on all Android phones shipped from the factory.
While the app itself packs a punch and powerful, unfortunately, it has had a vulnerability that could have allowed hackers to quietly steal personal data from victims' devices.
In a blog post by Sergey Toshin, founder of mobile app security startup Oversecured:
"For example: in the Google app."
Almost every Android app dynamically loads code from native .so libraries or .dex files. There are also some special libraries like Google Play Core to simplify this process.
Among a number of reasons, this allows developers to reduce the download size of their apps, allowing the apps to be installed in a lower storage space requirement.
But according to Toshin, dynamic code loading can be very dangerous.
In Google's case, the vulnerability in the Google app was present because the app relied on code that is not bundled with the app itself, but on libraries that are already installed on Android phones.
The flaw here is that, the Google app could be tricked into pulling a code library from a malicious app on the same device instead of the legitimate code library.
This allowed a malicious app to inherit the Google app’s permissions and granting it near-complete access to users' data.
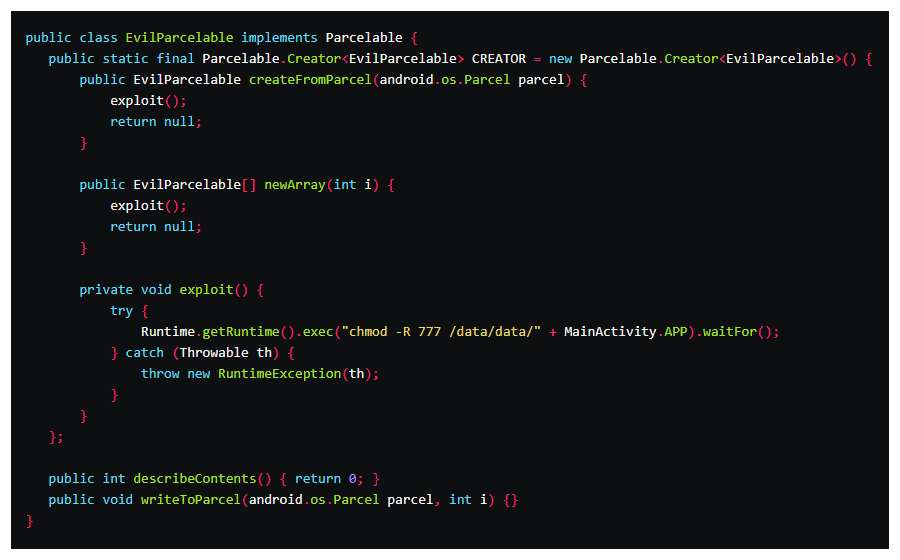
EvilParcelable.java made to infect MainActivity.java. (Credit: Oversecured)Another way of saying this, the flaw on the Google app could have allowed malicious app to gain access to users' Google accounts, search history, email, text messages, contacts and call history, as well as being able to trigger the microphone and camera, and access the user’s location.
And all the malicious app needed to do, is to be launched only once, Toshin said, and that the attack can happen without the victim’s knowledge or consent.
Making things worse, victims who wish to remove the threat by deleting the malicious app wouldn't be able to remove the malicious component, simply because the malicious components are already tied to the Google app.
A Google spokesperson said that the company has fixed the vulnerability, and said that it has seen no evidence that the flaw has been exploited by hackers.
Google fixed the issue in May 2021, Toshin said.
Toshin also said that the same flaw was also found on the TikTok app, which if exploited, could have allowed hackers to steal a TikTok user’s session tokens to take control of their account.
Oversecured has found several other similar vulnerabilities, including Android’s Google Play app and also on apps pre-installed on Samsung phones.
