When developers code, some security issues can go unnoticed. If this happens, other programs that are made with the flawed code, can inherit the same issues.
GitHub is a code-hosting website popular among developers for open-source projects. And here, it is rolling out a security feature named 'Code Scanning' for all users, on both paid and free accounts.
The feature that GitHub said has been made generally available to all, can help prevent vulnerabilities from ever reaching production by analyzing every pull request, commit, and merge—recognizing vulnerable code as soon as it's created.
Once a flaw in a code is detected, Code Scanning will prompt the developers so they can revise their code.
The feature is launched after GitHub introduced it in public beta back in May 2020.
Since that time, GitHub said that the feature has been used to perform more than 1.4 million scans on more than 12,000 repositories, and has identified over 20,000 vulnerabilities, including remote code execution (RCE), SQL injection, and cross-site scripting (XSS) vulnerabilities.
According to its Docs page, Code Scanning allows developers to find, triage, and prioritize fixes for existing problems in their code.
Code Scanning also prevents developers from introducing new problems.
Developers can even schedule scans for specific days and times, or trigger scans when a specific event occurs in the repository, such as a push.
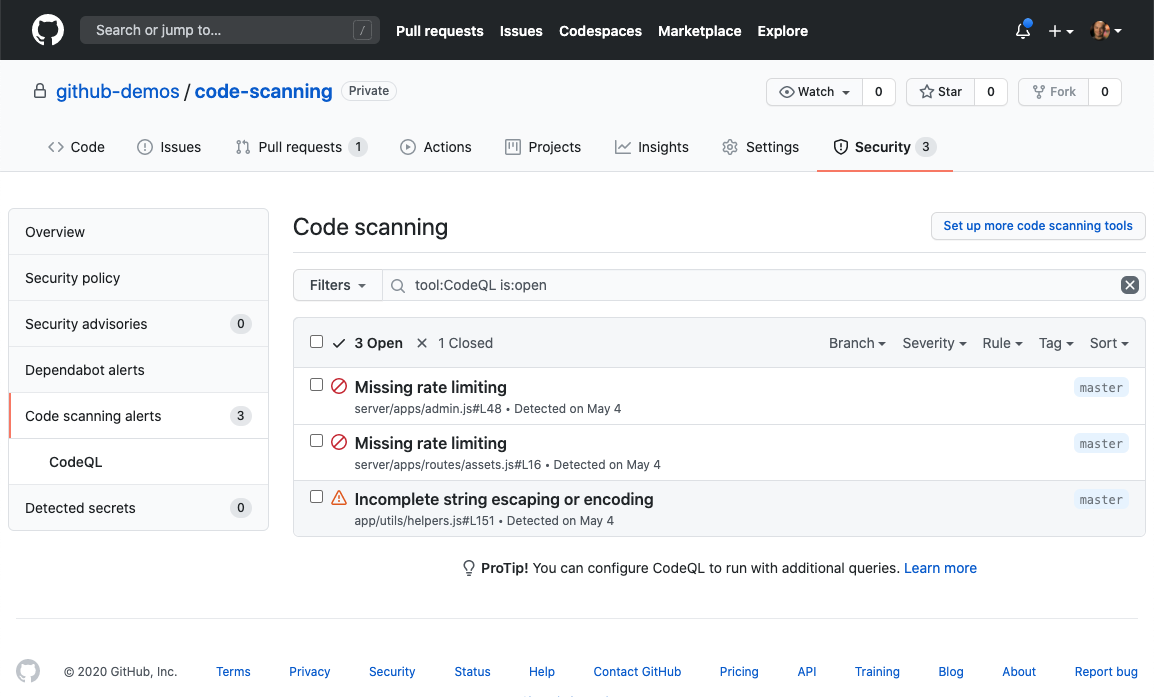
If the feature finds a potential vulnerability or error in users' code, GitHub will display an alert in the repository.
GitHub will show the alert persistently until the developers can solve the issue.

To make this happen, the feature runs top of CodeQL, a technology that GitHub integrated into its platform after it acquired code-analysis platform Semmle in September 2019.
CodeQL stands for "code query language", and is a generic language that allows developers to write rules to detect different versions of the same security flaw across large codebases.
Powering Code Scanning, it can find vulnerabilities and errors in code that is written in the following supported languages:
- C/C++.
- C#.
- Go.
- Java.
- JavaScript/TypeScript.
- Python.
In addition, Code Scanning can also be extended via custom CodeQL templates written by repository owners or by plugging in third-party open-source or commercial static application security testing (SAST) solutions.
To configure Code Scanning, users must visit the 'Security' tab of each of the repositories they want the feature to be enabled.
Here, developers will be prompted to enable the CodeQL queries they want GitHub to use to scan their source code.
To get users started on using Code Scanning, Gitub said that its security team has put together more than 2,000 predefined CodeQL queries that developers can enable for their repositories and automatically check for the most basic security flaws when submitting new code.
"For those interested in helping to secure the open source ecosystem, we also invite you to contribute to the growing list of CodeQL queries and become part of our growing security community," said GitHub.