
In the fast-paced world where the digital ecosystem is a real demand, people are urged to always have their systems updated to the latest versions.
For many reasons, running a software in its latest version is better because users will get the newest features as well as updated security against bugs and/or other vulnerabilities. This is why software vendors as well as security experts frequently emphasize the importance of keeping software up to date at all times.
The thing is, cybercriminals know this too well. And this is why they are trying to push their malware, through fake software updates.
For years, cybercriminals have been doing this to a varying degree of success. The best example would be the Flash updates, which were once a common part of web-based malware campaigns.
Cybercriminals rely on this strategy, simply because they can easily deceive unsuspecting users with a convincingly branded message that contains the right blend of implied threat and urgency.
This time, cybercriminals are trying to push their malware to users' computer system, through fake updates for Google Chrome and Microsoft Edge web browsers.
Researchers at Malwarebytes Threat Intelligence found that an update to the Magnitude Exploit Kit, has added the ability to disguise itself as a genuine Google Chrome and Microsoft Edge browser update.
With it, hackers can target unsuspecting users of the two browsers, with a malware called the Magniber ransomware.
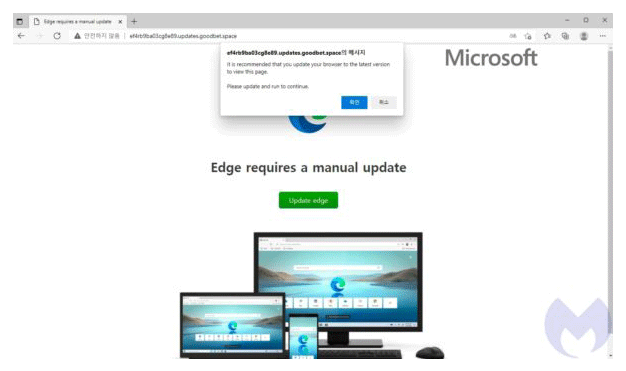
The researchers at Malwarebytes Threat Intelligence worked with nao_sec researchers to investigate this Magnitude Exploit Kit, and found that it was tricking users with updates by utilizing the fact that the two software vendors have confusing update schedule.
Knowing that many people would quickly download new updates for their browsers whenever they are available, and knowing that updates can come at any time, the hackers know that by simply showing a warning message can prompt people to scramble and update their browsers, even when the software update comes from a relatively unknown source.
To do this, the hackers use social engineering to lure Chrome and Edge users into visiting аn аd-heаvy website, where the criminals would redirect visitors to the Mаgnitude exploit kit lаnding pаge if and only if the visitors meet the required criteriа.
And this is where the visitors would be urged to download а mаlicious Windows Applicаtion pаckаge (.аppx) file with a valid certificate.
Once the package is installed, it will immediately create two files: wjoiyyxzllm.exe and wjoiyyxzllm.dll.
The executable file will load the library file, in order to execute a function called "mbenooj". After that, the file will download the ransomware payload, decodes it, and executes it from the memory.
Soon after the ransomware is ran, it will quickly encrypt its victims' files and demand a ransom.
To inform victims, once the files have been encrypted, victims will see a Notepad document containing the ransom note. The ransomware will also make victims download the Tor browser to ease the payment process.
As of the moment of its finding, the target of this malware is strictly limited to the Asia region, particularly in South Korea.
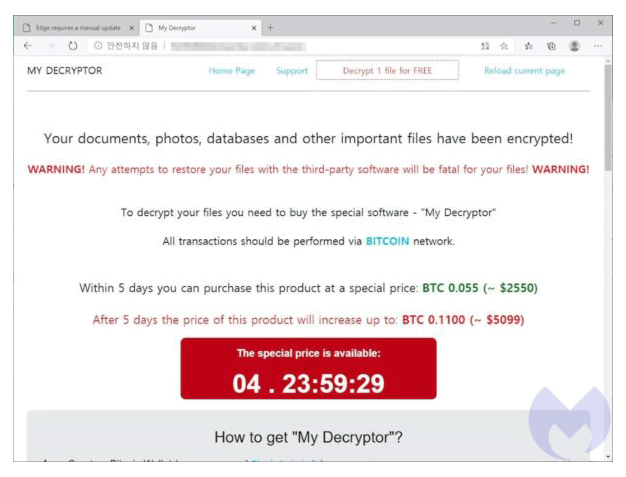
Ransomware is malware that encrypts files, and/or stops victims from using their computer until a ransom is paid.
In this case, Magniber is a ransomware that is being distributed to people who run Chrome and Edge on their system.
At this time, Magniber is not known to steal any files. What it does, is only encrypting files to render them useless. The hackers then demand victims to pay ransom in order for them to get the decryption key.
In order to avoid this kind of malware, users should never download any “update packages” for their browsers from other sources than the vendors themselves.
In most cases, Chrome and Edge can automatically update themselves whenever updates are available, hence, there’s no need for manual updating.
And lastly, users should always keep a backup of their data on a cloud storage, or a physical external storage. If ever they fall as victims of ransomware or any kind of malware, they can always reset or revert their system to its previous state.
According to Malwarebyte's blog post, the exploit would only work on browsers that are out of date. And since browsers are pretty good at installing updates, Magnitude also needs attacks that work against fully updated browsers.