
Mozilla released updates to its Firefox browser to patch a security hole that was already being exploited by hackers in the wild.
First flagged by security researchers Francisco Alonso and Javier Marcos, the two vulnerabilities patched were released as critical security updates.
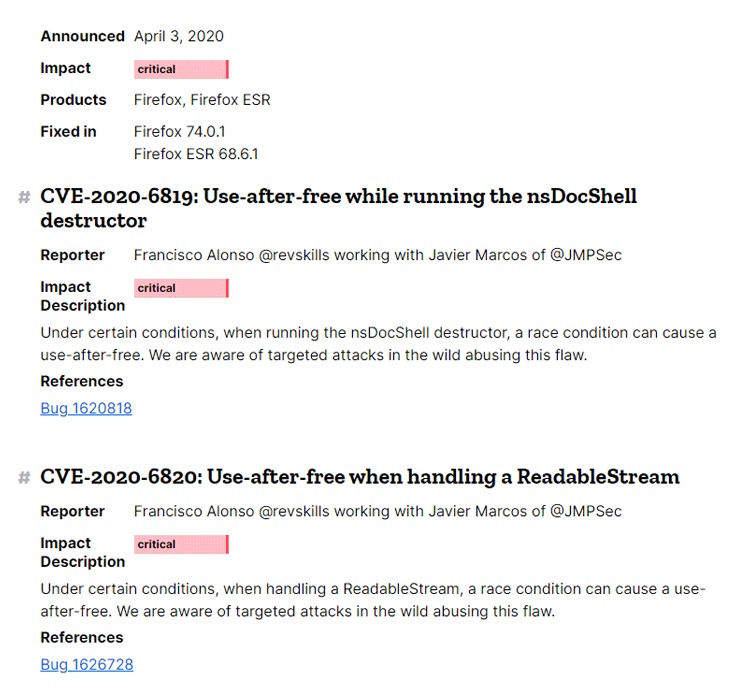
Users of the regular version of Firefox, should update from 74.0 to 74.0.1, and for users of Firefox Extended Support Release (ESR), they need to update from ESR 68.6.0 to ESR 68.6.1.
In its security advisory web page, Mozilla as the creator of Firefox, said that:
CVE-2020-6820: Use-after-free when handling a ReadableStream. Under certain conditions, when handling a ReadableStream, a race condition can cause a use-after-free. We are aware of targeted attacks in the wild abusing this flaw.
A use-after-free is a class of vulnerability caused by incautious use of memory space by a program.
Usually, a program returns blocks of memory to the operating system after it has finished using them. This allows the operating system to use the freed memory for something else. This is crucial, since any program that keeps running in the memory can hog other programs.
The longer it runs can cause the whole system to slow down.
In this case, the vulnerabilities made Firefox to store data inside device's memory, despite it didn't need them anymore. Not all use-after-free bugs are exploitable. The impact and reach of such code usually varies, but in Firefox's case, it allowed hackers to place a code inside Firefox's memory and have it executed in the browser's context.
Hackers can also exploit the vulnerabilities to change the flow of control inside installed programs, including diverting the CPU to run untrusted code that hackers just inserted into the memory.
This essentially sidestepped any of the browser’s usual security checks.
There is still lots of work to do and more details to be published (including other browsers). Stay tuned.
— Francisco Alonso (@revskills) April 3, 2020
The two vulnerabilities have been rated “critical”, meaning that hackers could have exploited them for remote code execution.
Given that the bug patched were found on both the latest and the ESR versions, it could be assumed that the vulnerabilities had been in the Firefox codebase at least since version 68 first appeared, which can be dated back to July 2019.
Or, the vulnerabilities could have been introduced as a side effect of security fixes that came out after version 68.0 was launched.
The bugs' details in Mozilla’s bug database aren’t initially open for public viewing, because Mozilla knows that discussing in details in such an early time would allow additional exploits very much easier to create.
Users and enterprise administrators are advised to implement the provided updates as soon as possible. They should also make sure that Firefox can update itself every time a new update is made available, as recommended by Mozilla.
Mozilla credited Francisco Alonso and Javier Marcos with discovering the two zero-days.
In a tweet, Alonso suggested that the bugs discovered might also impact other browsers, although it is unclear if those browsers have been exploited as well.