
Dealing with even one of the common diseases can be very difficult if that disease spreads fast.
The same goes to this Android malware that spreads extremely fast with the aim of stealing passwords, bank details and other sensitive information. Once installed, the malware also gains access to the victim's address book, allowing it to send text message to all their contacts, further spreading the malware.
Called the 'FluBot', the malware is installed via text messages claiming to be from a legitimate delivery company such as DHL, Amazon, Asda, Argos and others.
Through the messages, it asks users to click on a link to track a package delivery.
When clicking on the link, victims will head to a website, where they need to install an application by downloading an APK file to follow the fake delivery.
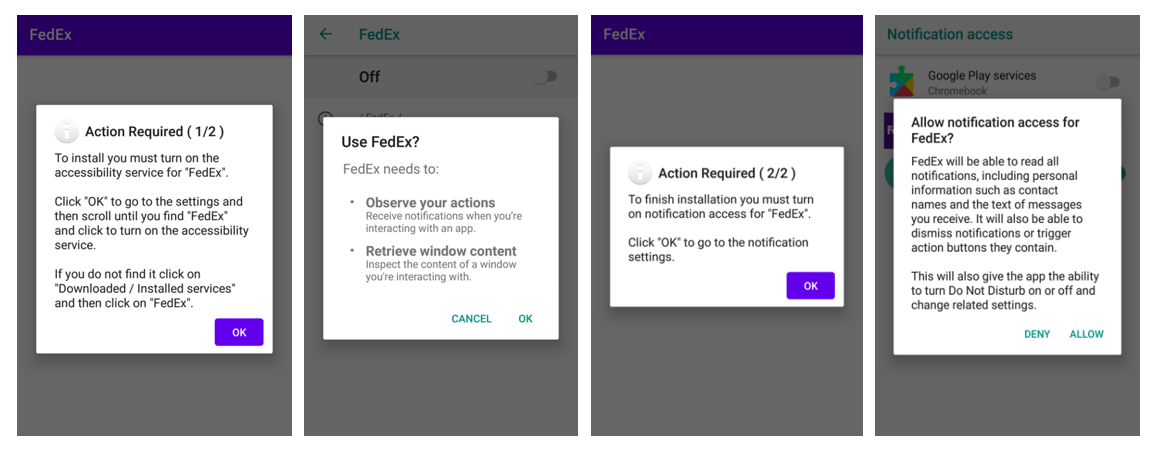
Knowing that Android disables installation of APK files from third-parties, the fake websites provide information on how to bypass these protections and allow FluBot to be installed.
Once installed, FluBot will quickly obtain all the permissions necessary to access and steal sensitive information including passwords, online bank details and other personal information, as well as the ability to spread itself to others.
It's through this worm-like mechanism of using contact information that allows FluBot to spread quickly.
The UK's National Cyber Security Centre (NCSC) has issued a security guidance on how to identify and remove this FluBot malware, while a number of network providers including Three and Vodafone have also issued warnings to their users over the text message attacks.
The NCSC urges users who receive the FluBot messages to forward them to the free spam-reporting service, before proceeding to delete the message.
The NCSC has also warned people who've already clicked the link and downloaded the application to not login to any additional online accounts to stop attackers harvesting more personal information.
After that, they need to perform a factory reset of the device as soon as possible, and then restore their device to their previous state before the FluBot malware was installed.
The NCSC also recommends that users should change the passwords of any accounts they've logged in to since downloading the app, as well as any other accounts that use the same password, in order to prevent attackers from having continued access.
To protect against this kind of malware and scams, NCSC said that users should:
- Backup their device to ensure that they don’t lose important information like photos and documents.
- Only install new apps from the official app stores. For example, most Android devices use Google’s Play Store. Some manufacturers, such as Huawei, provide their own app store.
- For Android devices, make sure that Google’s Play Protect service is enabled if the device supports it. Some Huawei devices provide a similar tool to scan devices for viruses.
It is also said that users must be wary of unexpected SMS messages, and take the time to verify that the requested permissions make sense when they want to install new apps.
According to reports, the malware only infects Android devices.
However, the NCSC advises Apple users to also pay close attention to text messages that ask them to click links about a delivery.
While the APKs won’t install on iOS devices, there is always the chance that the fake delivery websites could also be used to steal personal information.
FluBot has the capacity to continue to spread at a fairly rapid rate. Despite there are ways to easily remove the malware, as long as there are people willing to trust an unexpected SMS message and follow the threat actors’ provided instructions and prompts, campaigns such as these will be successful.