
Transport Layer Security or TLS, is the successor of Secure Sockets Layer (SSL), meant to encrypt web communication when information travels over networks.
From regular web browsing to using email, instant messaging, and voice over IP (VoIP), they all use TLS to secure their communication between their servers and users.
The TLS protocols aim to provide the needed privacy for data integrity.
TLS supports many different methods for exchanging its keys, encrypting data, and authenticating message integrity. As a result, secure configuration of TLS involves many configurable parameters.
As years pass, many attempted to revise security threats TLS has. Developers of web browsers have also repeatedly tweaked their products to defend against known potential security issues TLS is giving them.
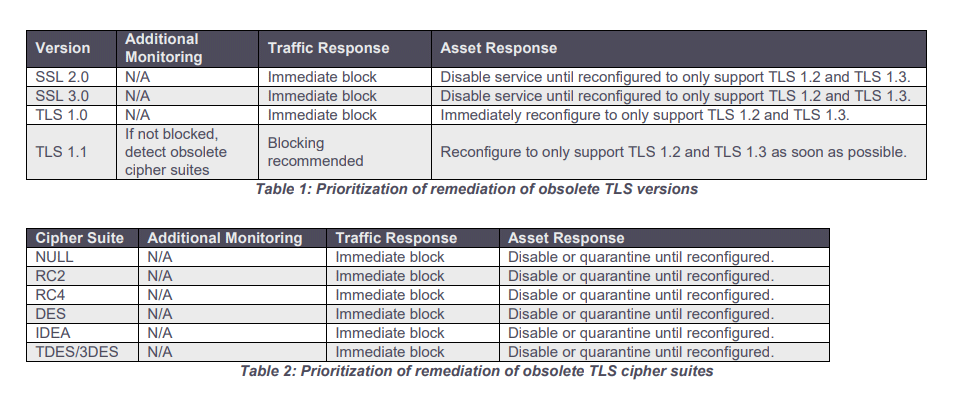
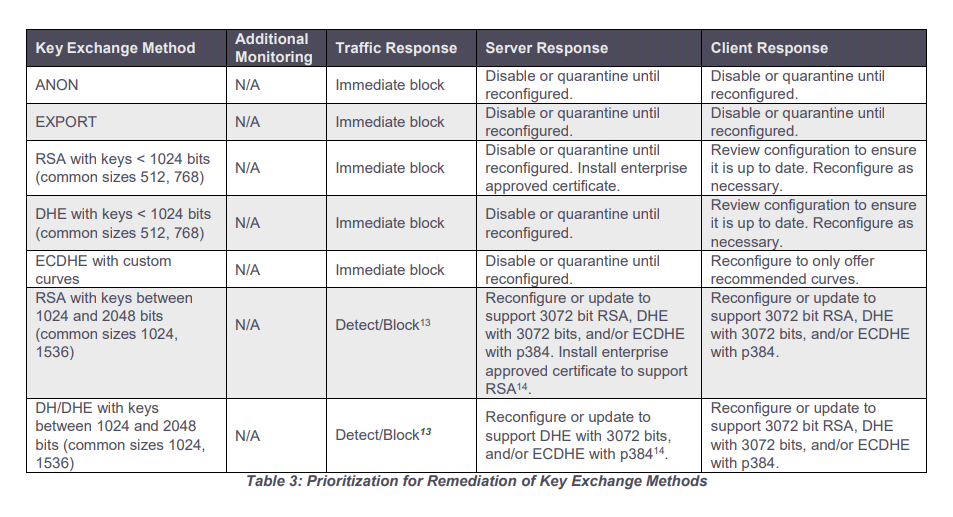
Because some TLS versions are outdated, the U.S. National Security Agency (NSA) has shared some guidance on how to detect and replace the outdated TLS protocol versions with their up-to-date and secure variants.
The intelligence agency also highlights the dangers behind using outdated TLS protocols, including the huge risks of sensitive data exposure and decryption of network traffic in man-in-the-middle attacks.
On its web page, the NSA wrote that:
NSA's guidance here, is meant to eliminate the "false sense of security" provided by the obsolete TLS, by helping block their insecure versions, cipher suites, and key exchange methods to properly encrypt network traffic.
Updating TLS configurations should provide government and enterprise organizations a stronger encryption and authentication, which can in turn help them build a better defense against malicious actors' attack campaigns and protecting sensitive information.
NSA's guidance is targeted at National Security System (NSS), Department of Defense (DoD), and Defense Industrial Base (DIB) cybersecurity leaders, as well as network security analysts and system administrators.
While the tools the NSA shares are designed to help government networks enhance their security, the guidance should also apply to all "network owners and operators," considering that the risks of using deprecated TLS protocols' weak encryption affect all networks.
Everyone should never use outdated TLS with no exception, if they want to decrease their risk exposure and harden their systems against attacks using these attack vectors.
"Obsolete configurations provide adversaries access to sensitive operational traffic using a variety of techniques, such as passive decryption and modification of traffic through man-in-the-middle attacks," the NSA said.
"Attackers can exploit outdated transport layer security (TLS) protocol configurations to gain access to sensitive data with very few skills required."