
GitHub has uncovered a form of malware that spreads via infected repositories on its system.
Following a tip from a security researcher on 9 March that goes with the name 'JJ', GitHub that started analyzing how this malware works, calls this malware a “virulent digital life”, due to how it lurks in source code repositories uploaded to its site.
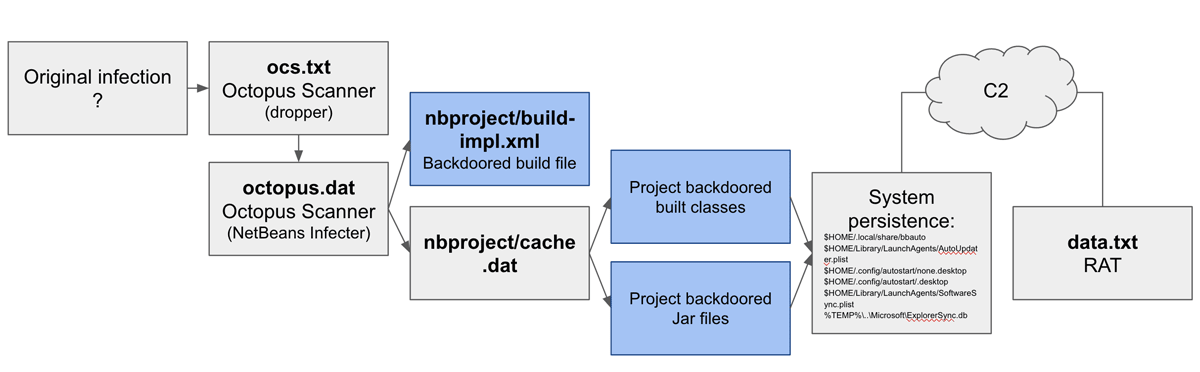
Dubbed the 'Octopus Scanner', the malware targets Apache NetBeans, which is an integrated development environment used to write Java software.
When a developer downloads a project from an infected repository and uses the project's source code to develop a working program, the build process activates the malware.
It scans the developers' computer to see if they have a NetBeans IDE installed. If they don’t, it will take no further action. But if they do, the malware will infect the built files with a dropper that delivers its final payload: a remote access trojan (RAT) that gives the perpetrators control over the user’s machine.
The malware is also capable of infecting JAR files — including dependencies.
In other words, the malware weaponizes infected repositories to target potential developers to unleash a supply chain attack.
According to GitHub staff security researcher Alvaro Muñoz in a company blog post:
GitHub described this malware as the first: “malware designed to enumerate and backdoor NetBeans projects, and which uses the build process and its resulting artifacts to spread itself.”
The malware makes use of GitHub's repositories hosting environment as a method to spread.
GitHub is an online service based on Git, a code versioning system developed by Linux creator Linus Torvalds. This way, GitHub allows developers to use uploaded projects for their own software development projects. Because Git lets developers take snapshots of files, this enables them to revert their changes later or create different branches of a project for different people to work on.
Leveraging Github's way of managing repositories, the Octopus Scanner is able to ‘push’ infected copies of repositories so that other developers can download (clone) the infected project and work on them too.
The malware also tries to block any new project builds to replace the infected one, in order to preserve itself on the infected system.
Making things worse, Octopus Scanner doesn’t just infect the built files only, as it can also infect a project’s source code, meaning that any other newly-infected projects mirrored to remote repositories would spread the malware even further on GitHub.
The team at GitHub Security Labs matched the malware that it found with software hashes on VirusTotal and found that it has a low detection rate. This is the reason why the malware is able to spread without easily being caught.
After scanning the platform's available repositories, the team found 26 repositories containing the malware.
GitHub is no stranger to malicious actors who want to use its repositories to deliberately distribute malware. Usually, GitHub can simply shut those repositories down, and/or and delete the accounts.
But the Octopus Scanner is different.
The malware is tricky because the developers owning the respositories may not know that they were infected. Because they have no idea about what's going on, as they are only running legitimate projects, the developers who have their repositories infected, are also victims.
Blocking those accounts or repositories could affect businesses, and GitHub couldn't shut them down.
GitHub also couldn’t merely delete the infected files in a compromised repository either, because the infected files could have already been used by legitimate software project.
And making things even worse, the malware primarily affects users that are developers. Since developers generally have access to additional projects, production environments, database passwords, and other critical assets, infecting their systems could allow the authors behind Octopus Scanner to get insight into valuable data.
According to GitHub’s research, this malware has been in circulation since at least 2018.