
Microsoft Windows is an operating system that is the base for other software, programs and apps to run on to.
Due the fact that many things can happen during users' usage of the operating system, Windows can create backups of users' system and data files, and store them in what it calls the 'Shadow Volume' copy snapshots.
In case something goes wrong, users can recover from these copies.
Ransomware authors don't want this to happen.
For that reason, some ransomware will try to delete all Shadow Volume copies inside a victim's computer, before holding anything for ransom.
One of the methods they do, is using the following vssadmin.exe command:
vssadmin delete shadows /all /quiet
But this time, a security researcher managed to counter that, with a "vaccine."
Haha .. I did it .. Raccine - a simple Ransomware Vaccine
- uses debugger registration to intercept vssadmin.exe invocations
- collects process tree pids for kills
- PoC as weekend project
- my C code sucks, but it workshttps://t.co/vfN7gLmdpP pic.twitter.com/4gNb2RS7sT— Florian Roth (@cyb3rops) October 3, 2020
The so-called ransomware vaccine is created by security researcher Florian Roth. Calling it the 'Raccine', it is capable of monitoring any attempt of Shadow Volume copies deletion using the vssadmin.exe command.
"We see ransomware delete all shadow copies using vssadmin pretty often. What if we could just intercept that request and kill the invoking process? Let's try to create a simple vaccine," explains Raccine's GitHub page.
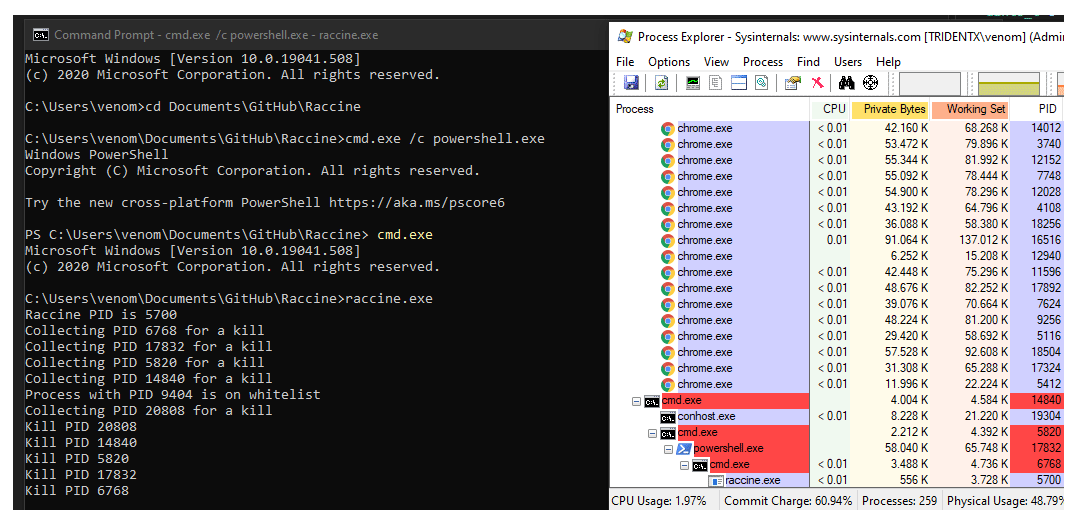
How this "vaccine" works, is by registering its raccine.exe executable as a debugger for vssadmin.exe using the Image File Execution Options Windows registry key.
Once the executable file is registered as a debugger on a Windows system, every time the vssadmin.exe file is executed, it will also launch the Raccine.
This will automatically check whether or not vssadmin is trying to delete any of the system's Shadow Volume copies.
If it detects that malicious attempt, it will automatically terminate that process.
Since the malicious attempt usually happens before a ransomware begins encrypting files, its failure to delete any Shadow Volume copy can halt its entire process, rendering the ransomware dormant.
While this Raccine vaccine can prevent encryption by a large amount of ransomware, some modern ransomware families and variants can still delete Shadow Volumes copies using other commands, like:
Get-WmiObject Win32_Shadowcopy | ForEach-Object {$_.Delete();}WMIC.exe shadowcopy delete /nointeractive
For ransomware that runs the above code, the initial version of Raccine won't block the ransomware, as they don't use the vssadmin.exe executable.
This is one of the reasons why Raccine is called the "simple ransomware vaccine."
It should also be noted that Raccine may terminate legitimate software that uses vssadmin.exe as part of their backup routines.
Furthermore, "you won't be able to run commands that use the blacklisted commands on a raccinated machine anymore until your apply the uninstall patch raccine-reg-patch-uninstall.reg," the GitHub page said.
"This could break various backup solutions that run that specific command during their work. It will not only block that request but kills all processes in that tree including the backup solution and its invoking process."
Roth said that he has plans on adding the ability to allow certain software to bypass Raccine in the future so that they won't be mistakenly terminated.