
Android is one of the most popular operating system for mobile devices. With its flexibility, it has garnered a lot of attention, fans and users. But those come with big caveat.
According to Japanese IT security company Trend Micro, adware apps have been plaguing Google Play Store, disguising themselves as games, TV apps, remote control apps, and others.
Together, these malicious apps have reportedly infected nine millions users.
First of all, Trend Micro reported 85 apps that have been detected to have AndroidOS_HidenAd, capable of displaying full-screen ads and monitoring a device’s screen unlocking functionality.
Trend Micro said that the apps can keep their malicious activities hidden while still running in affected mobile devices' background.
The 'Easy Universal TV Remote' app is one of them.
Claiming to allow users to use their smartphones to control their TV, was one of the most downloaded among the 85 adware apps, with a total of more than 5 million users using it.
To come into this conclusion, Trend Micro said that it has tested each of the fake apps related to the adware family, and discovered that though they come from different developers and have different APK cert public keys, they exhibit similar behaviors and share the same code.
"After the adware is downloaded and launched on a mobile device, a full-screen ad initially pops up," explained the IT security company.
When these apps are installed and users use it, they can launch intrusive ads. And when users close the first ad that appears, call to action buttons show such as "start," "open app," or "next," as well as a banner ad appear on the user’s mobile device’s screen.
And when the user taps on these action buttons, yet another full-screen ad pops up prompting users to give a five-star rating to the app on Google Play.
Tapping on another call-to-action button, the app informs users that it is loading or buffering.
And then comes the annoying part, as after a few seconds, the app somehow disappears from users' screen and hides its icon. But still, the app runs in the background.
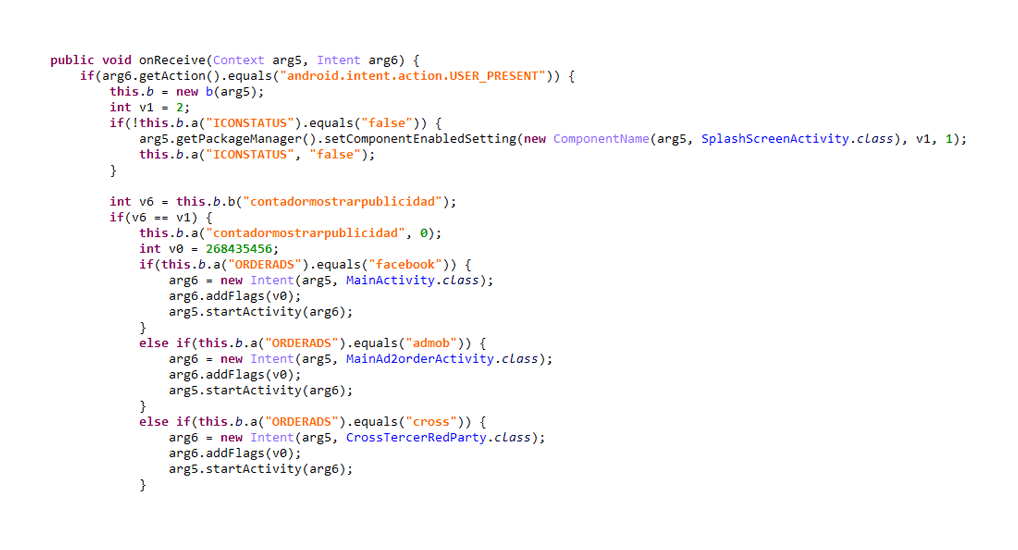
The adware is configured in such a way that though hidden, a full-screen ad pops up every 15 or 30 minutes on the user’s device. Some of these apps monitor user screen unlocking action and each time a user unlocks the device, it will then trigger a full-screen ad pop up.
Trend Micro noted that there were multiple complaints about the Android app in the comments section of the Google Play Store.
After notifying Google about these malicious apps, which were then verified, Google removed all 85 offending apps from the Play Store.
"The 85 fake apps, which have been downloaded a total of 9 million times around the world. After verifying our report, Google swiftly suspended the fake apps from the Play store," Trend Micro stated in its blog.
"While the fake apps can be removed manually via the phone’s app uninstall feature, it can be difficult to get there when full-screen ads show up every 15 or 30 minutes or each time a user unlocks the device’s screen."
"As more and more people become dependent on mobile devices, the need to keep mobile devices safe from a growing number of mobile threats — such as fake apps laced with adware — is all the more pertinent."
In another report, Trend Micro also found a bunch of spyware apps on Google Play from where users from 196 countries had downloaded them over 100,000 times.
The malware in the seemingly harmless apps is capable of stealing user location, SMS conversation, call logs and even clipboard items.
It is also capable of showing phishing pages for Google and Facebook mobile login pages.
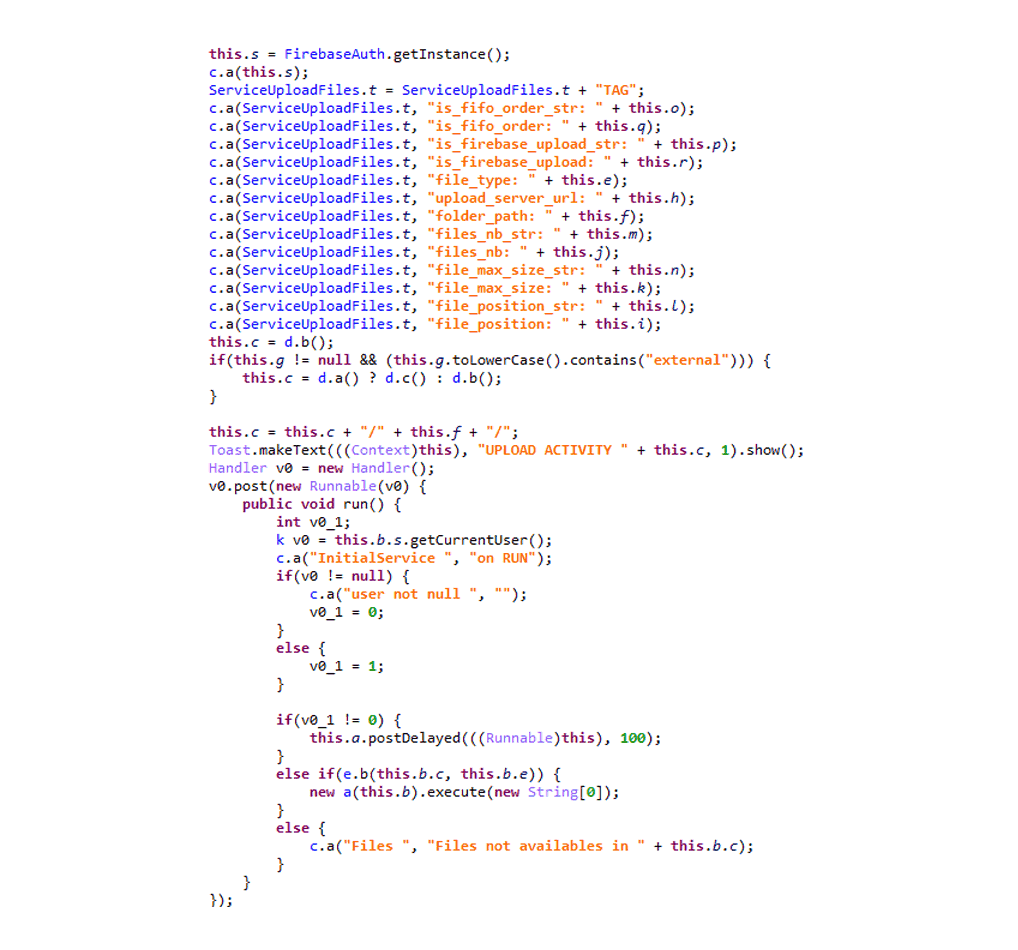
The apps use Firebase Cloud Messaging (FCM) to send information to its server. And even worse, the malware can also steal and upload files it found on the device.
ANDROIDOS_MOBSTSPY) which disguised itself as legitimate Android applications to gather information from users. The applications were available for download on Google Play in 2018, with some recorded to have already been downloaded over 100,000 times by users from all over the world."When first installed and opened, the malicious app's malware will scan the infected device's network availability. If present, the app reads and parses an XML configure file from its server.
It will then collect information from the infected device, including its registered country, package name, device manufacturer etc., and send the gathered information to its server, registering the device.
Once that is done, the malware will wait to perform specific commands sent from its server through FCM.
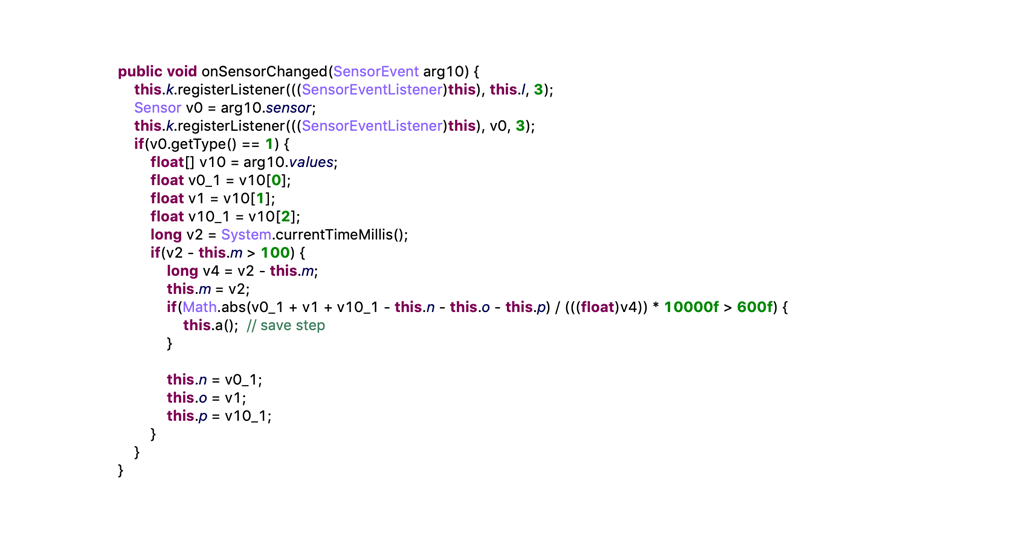
On another report, also from Trend Micro, stated that it found two malicious apps on Google Play Store that detect motion.
The developers of these malicious Android apps use this trick to sense when the infected device is not in the move. If the infected device is not moving, there is no sensor data. This means there is a chance the the app is running in a sandbox, where it is likely to be if it were being analyzed by an anti-malware solution.
Here, when the infected device is not on the move, the malicious code inside the apps remain on standby to prevent itself from being detected.
"The malware developer is assuming that the sandbox for scanning malware is an emulator with no motion sensors, and as such will not create that type of data. If that is the case, the developer can determine if the app is running in a sandbox environment by simply checking for sensor data," explained Trend Micro researcher Kevin Sun.
Researchers at Trend Micro found these two malicious apps that displayed this behavior, and found that they were also installing banking malware called Anubis. This particular malware has been historically associated with delivering a banking trojan to Turkish Android users, according to Sophos.
Sophos found the apps acted as downloaders that appear safe when entering the Play store, but eventually download malicious apps.
To do their job, the apps relied on Telegram and Twitter web requests to establish trust with the affected device, and connect to a command and control server, and ultimately install the Anubis banking trojan on the infected device. This process happens if the user approves a fake system update.
Instead of using fake screen overlays to steal users' credentials, Anubis has a keylogger function, and can also take screenshots to capture sensitive information.
The two new apps found by Trend Micro were disguised as a currency exchange tool, called 'Currency Converter', and a battery saver app, 'BatterySaverMobi'.
After Trend Micro's report, Google has also removed them from the Play store. However, the apps have been download thousands of times, and had attracted favorable reviews from scores of Android users.
Related: 14 Apps With 'Golduck Malware' Discovered In Apple's App Store