With the internet, the world becomes smaller. And with messaging apps, the world is becoming even smaller.
With billions of people use messaging apps to talk about anything, even for discussing topics that are most private or sensitive, messaging apps should ensure that they can protect user data and communication from prying eyes and ears.
But there can be bugs, and bugs are never a good thing.
A lot of messaging apps use what it's called the 'Web Real-Time Communication'.
Or better known as 'WebRTC', it's a free, open-source project providing web browsers and mobile apps with real-time communication (RTC) through simple application programming interfaces (APIs).
With it, apps can transfer audio and video communication through direct peer-to-peer communication, eliminating the need for users to install plugins or download native apps.
However, there are issues. That according to Natalie Silvanovich from Project Zero, who looked at apps with more than 10 million installs on Google Play that accept incoming calls.
According to the researcher, flaws in WebRTC and State Machines could have allowed a call to connect to a receiving device without alerting the receiving device's user in any way.
What this means, a bug can quietly open up an audio, and sometimes a video, and stream back the data to the calling device.
Simply put, flaws could have let eavesdroppers listen to users' communication.
"Theoretically, ensuring callee consent before audio or video transmission should be a fairly simple matter of waiting until the user accepts the call before adding any tracks to the peer connection," Silvanovich wrote in a Google Project Zero blog post.
"However, when I looked at real applications they enabled transmission in many different ways," she added. "Most of these led to vulnerabilities that allowed calls to be connected without interaction from the callee."
According to the researcher, the flaws were present on Android apps for Signal, Facebook Messenger, Google Duo and two other video-conferencing and chat apps, JioChat and Mocha.
The Signal flaw was fixed in the service's Android app in September 2019:
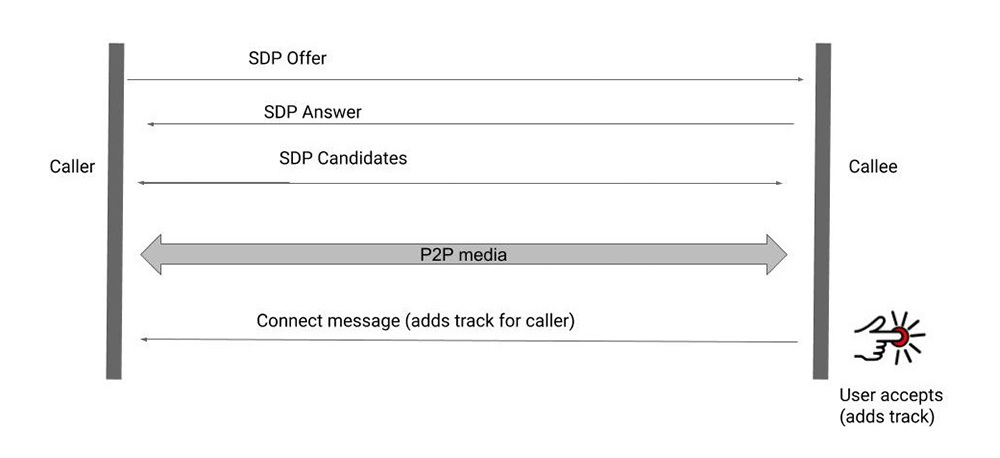
JioChat is widely used in India, and was patched in July 2020. Mocha that is popular in Vietnam, was patched in August 2020:
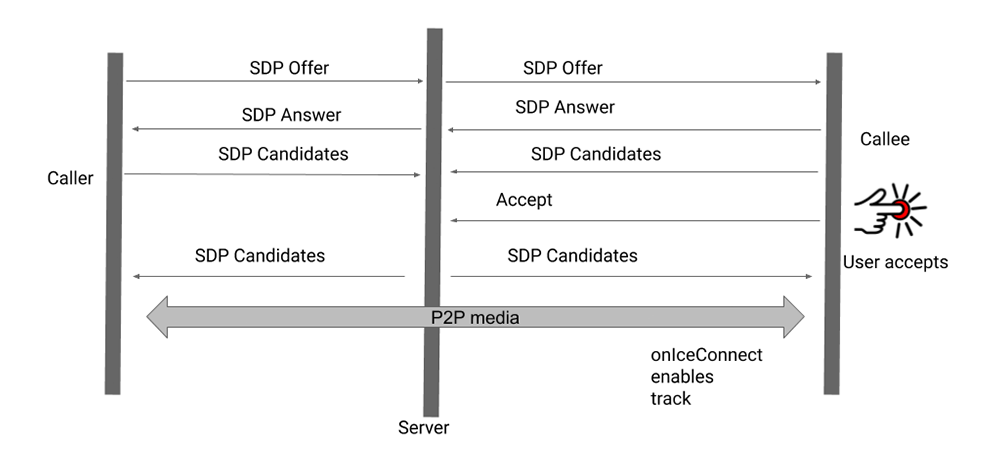
Facebook Messenger was patched in November 2020:
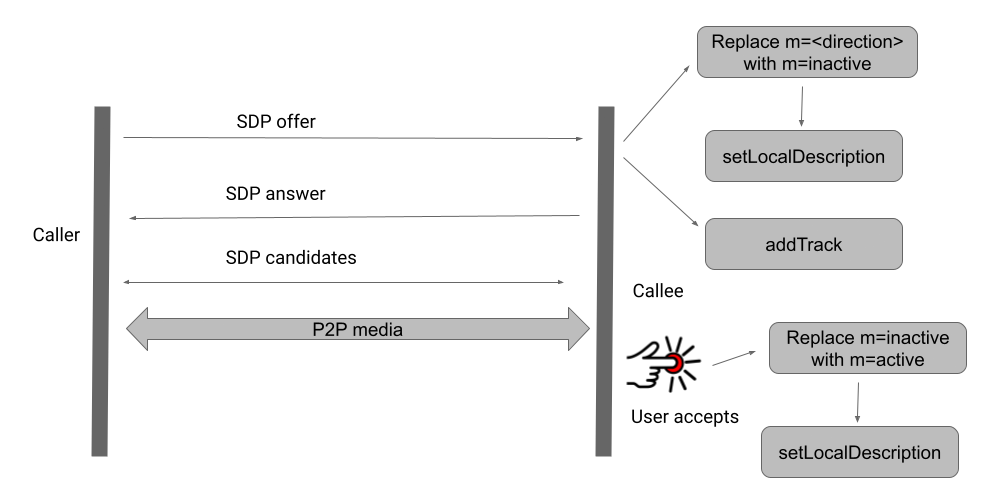
Google Duo in December 2020:
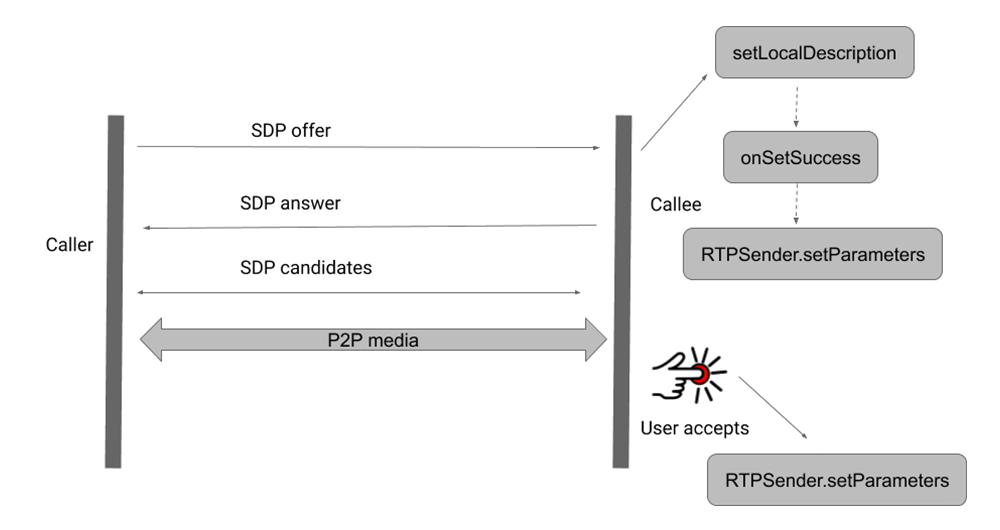
What happened here was when WebRTC connections are created by exchanging call set-up information in Session Description Protocol (SDP) between peers, in a process known as signaling.
Signaling which is not implemented by WebRTC, allows peers to exchange SDP in whatever secure communication message is available to them.
Throughout the process of calling, WebRTC maintains an internal state to know whether or not a call has been received or processed.
However, apps that use WebRTC usually have to maintain their own State Machine to manage the user state of the app, and this is done by the WebRTC integrator, which has both security and performance issues.
For example, some applications do not exchange any SDP until the callee user has interacted with the application to answer the call, meanwhile others set up the peer-to-peer connection, and start sending audio and video from caller to callee before the callee is even notified of the call," wrote Natalie Silvanovich from Project Zero in a blog post.
Silvanovich also tested Telegram and Viber, two other widely-used encrypted-messaging apps, and found no issues with calls being connected without the call receiver's knowledge.
It should be noted however, that Silvanovich "did not look at any group calling features of these applications," she wrote. "This is an area for future work that could reveal additional problems."
Silvanovich's research into these messenger apps follows on a similar flaw in Apple FaceTime on iOS and macOS that was discovered in January 2019.