People can store many things on their computers, some of which can be sensitive and personal.
While in use, computers can store users' passwords for their online accounts, store session cookies, as well as many other sensitive information. Modern browsers like Google Chrome and Mozilla Firefox can do this for user convenience, and this is why 'Jupyter' is exceptionally dangerous.
Jupyter is a Windows trojan, capable of stealing all said data, as well as hardware and software information and other valuable data from the two popular browsers and also from Windows itself.
The malware that was dubbed by the Israeli security firm Morphisec that first discovered it, is said to have been active since at least May.
It's finally traced after managing to escape detections of most antivirus software for about half a year this 2020.
"Morphisec has monitored a steady stream of forensic data to trace multiple versions of Jupyter starting in May 2020," said Morphisec in a blog post.
"While many of the C2s [malware command-and-control servers] are no longer active, they consistently mapped to Russia when we were able to identify them."
As an information stealer, Jupyter (a name that comes from the largest planet in the Solar System, misspelled as used as the background in the malware's administrative panel) has the ability to download and run additional software.
It can also create backdoors through which its authors who are presumed to be Russian hackers, can remotely seize control of victims' Windows machine.
Jupyter managed to avoid detection for many months, partly because it runs its operation mostly in its victims' computer memory.
Because of this, the trojan leaves little to no trace on its victims' hard drive.
And since it runs inside the memory, a simple restart would eliminate the trojan's activity. The authors know this, and this is why the trojan is designed to adds itself to victims' Startup folder so it can reinstall itself after every single reboot.

Jupyter can install itself in victims' Windows computer, after arriving in the form of an email attachment.
Morphisec discovered the malware while "assisting a higher-education customer in the U.S. with their incident response."
The attachment itself is disguised in a zipped file, often using Microsoft Word icons and file names that look like they need to be urgently opened, pertaining to important documents, travel details or a pay rise.
When opened, it will trigger a series of events using Windows PowerShell script, and install legitimate tools in an effort to hide the real purpose of the installation. It will then download additional files, and run them from a temporary folder in the background.
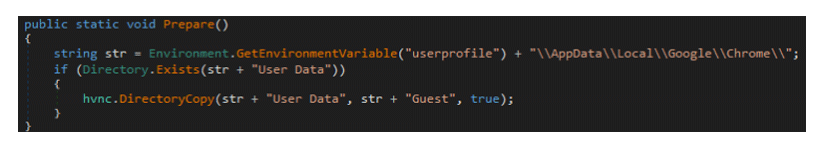
These files are installers, which will install as least two different information stealers: first, a malware that collects information about its victims' computer, and the second is to steal login credentials, login session cookies, autocomplete and digital certificates from both Chrome and Firefox.
With this kind of information, hackers can log in into victims' online session, be it Google, Facebook or others, and make it seem that they were accessing it through their victims' own machine.
What makes it even more dangerous is that, according to Morphisec's report on the trojan, the authors behind Jupyter are constantly changing the malware's code to be more efficient.
This makes it difficult for antivirus solutions to work effectively.
When Morphisec discovered this trojan, many of its command servers are already inactive. However, its administrative panel at http://45.146.165.222/j/login remains accessible.
This suggests that the Jupyter campaigns may still continue.
For users of Chrome and Firefox on Windows, they are advised to never store their login credentials inside the browsers, and to always log out from an online session after they finished using them.
As precautions, clearing cookies and browsing history should help, and of course, users should also scan every single email attachment with antivirus software before opening them.