
Stealing information has become a lot easier since more people use the internet. And hackers are becoming increasingly smarter as well.
Worok is a hacking group, and has been previously linked to numerous cyberattacks against telecommunications, banking, maritime, and energy companies, as well as military, government, and public sector entities. ESET security researchers who first spotted it, said that the group's target include those in the Middle East, Southeast Asia, and South Africa.
The group, which has been active since at least 2020, is known to have used a combination of custom and existing malicious tools.
And this time, the threat group has another trick under its sleeves.
And that is by using PNG files as part of their attacks.
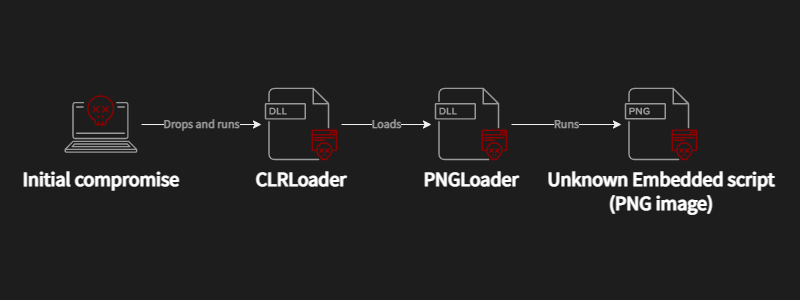
According to a report from researchers at Avast, who built upon the findings of ESET, it is said that the group hides malware inside PNG images, to infect victims' machines with information-stealing malware without raising alarms.
The researchers confirmed ESET's assumptions about the nature of the PNG format, and added new information on the type of malware payloads and the data exfiltration method.
Here, Avast believes that the hacking group uses DLL sideloading to execute the CLRLoader malware loader into victims' system's memory.
When the CLRLoader malware is finished loading, it then loads the second-stage DLL, which is the PNGLoader. This extracts bytes embedded in PNG files and uses them to assemble two executables.
This conclusion is based on evidence from compromised machines, where Avast's researchers found four DLLs containing the CLRLoader code.
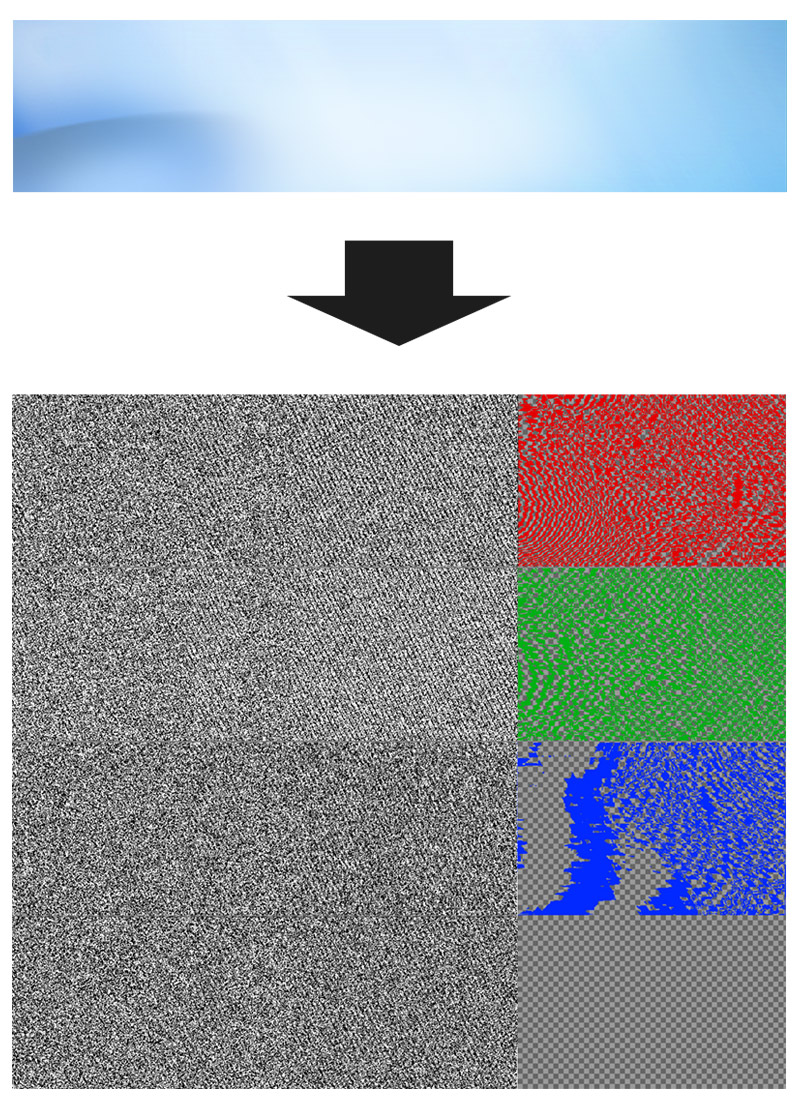
The method used to hide this sophistication, is called steganography.

It works by concealing code inside image files that appear normal when opened in an image viewer.
But in this case, Worok uses a well-crafted technique called "least significant bit (LSB) encoding," which embeds small chunks of the malicious code in the least important bits of the image's pixels.
Since steganography adds both encryption and compression, the result usually has an increased entropy of the image.
So it's no surprise that the image Worok spreads look like random noise.
"It is evident that the whole canvas of LSB bit-planes is not used," the researchers said.
Based on the payloads, the researchers found that the information-stealer malware abuses DropBox's file hosting service for command and control communication, file exfiltration, and more.
Upon closer inspection, the researchers found that the actual commands are stored in encrypted files on the threat actor's DropBox repository, and that the malware is able to access this repository periodically to retrieve pending actions.
After receiving commands, the malware can upload victims' data from the device to the DropBox repository, rename or delete data on the victim's system, create backdoor, and more.
These functions suggest that Worok is a cyberespionage group with a particular interest in stealthy data exfiltration, lateral movement, and espionage.
According to Avast, the tools sampled from Worok attacks aren't circulating in the wild.
What this means, the hackers at Work may have uniquely developed the tools for themselves.