The more popular a platform becomes, the more it interests hackers. And Google is no stranger to that.
The company published details about a sophisticated hacking operation that the company has detected in early 2020, which targeted owners of both Android and Windows devices. According to Google, the attacks were carried out through to exploit servers.
In what's called the "watering hole attacks", hackers guessed or observed where users are the most active, and infect the place with malware by exploiting their vulnerabilities.
"One server targeted Windows users, the other targeted Android," explained Project Zero, one of Google's security teams, in the introductory part of the six-part blog posts.
Google said that both exploit servers used Google Chrome vulnerabilities to gain an initial foothold on victim devices. When that happens, the hackers can create an initial entry point in the user's browsers, allowing them to deploy an OS-level exploit to gain more control of the victim's devices.
The exploit chains included a combination of both zero-day, which refers to a software vulnerability that is previously unknown to the software makers, and n-day vulnerabilities, which refers to bugs that have been patched but are still being exploited in the wild.
Google said that the attacks exploited four "renderer" bugs in Google Chrome, one of which was still a zero-day at the time of its discovery.
There were then two sandbox escape exploits that the hackers abused using three zero-day vulnerabilities in Windows.
And lastly, there was the "privilege escalation kit" composed of publicly known n-day exploits that the hackers used to attack users using older versions of Android.
The four zero-days exploits discovered in these chains have been fixed by the appropriate vendors:
- CVE-2020-6418: Chrome Vulnerability in TurboFan (fixed February 2020).
- CVE-2020-0938: Font Vulnerability on Windows (fixed April 2020).
- CVE-2020-1020: Font Vulnerability on Windows (fixed April 2020).
- CVE-2020-1027: Windows CSRSS Vulnerability (fixed April 2020).
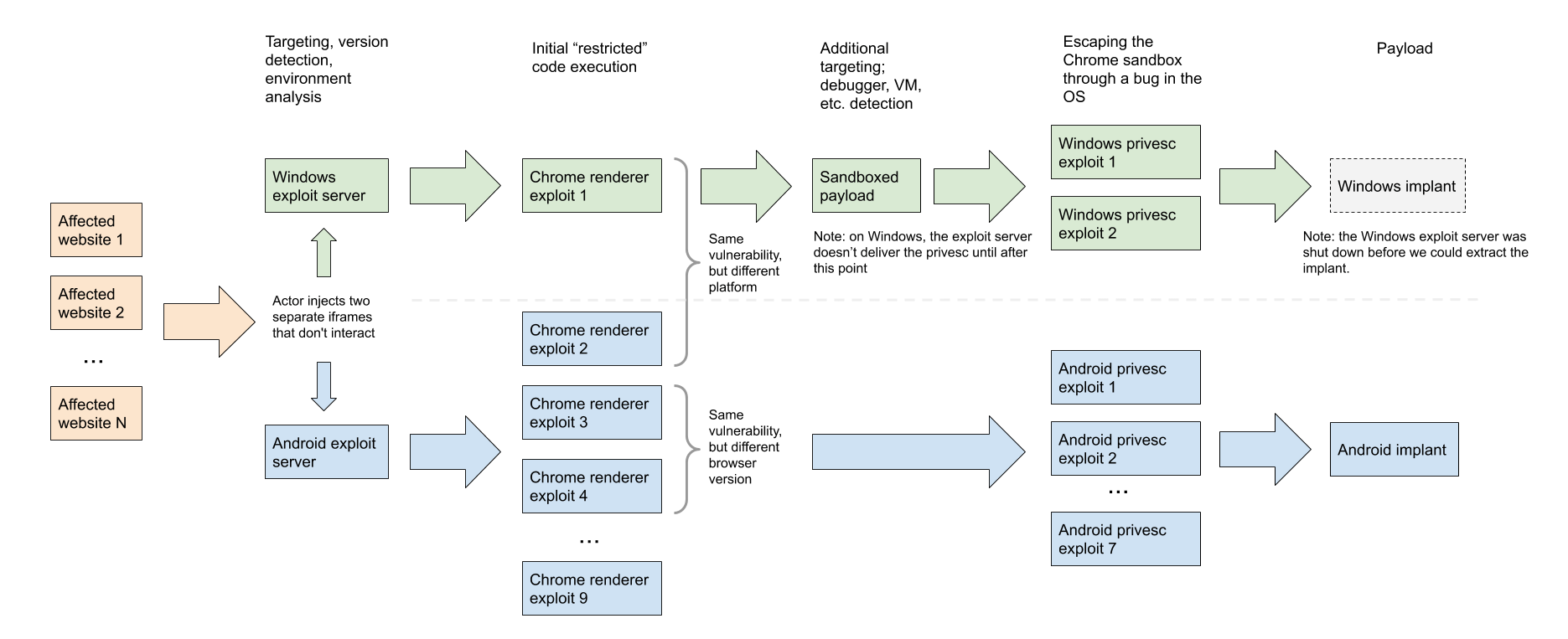
Google described the exploit chains as "designed for efficiency & flexibility through their modularity."
"We believe that teams of experts have designed and developed these exploit chains," but Google stopped short of providing any other details about the attackers or the type of victims they targeted."
Google said that its team didn't find any evidence of Android zero-day exploits hosted on the exploit servers. Its security researchers believe that the threat actor most likely had access to Android zero-days as well, but most likely weren't hosting them on the servers when its researchers discovered it.
Following the introductory blog post, Google has also published reports detailing a Chrome Infinity Bug used in the attacks, the Chrome Exploit chains, the Android Exploit chains, Android Post-Exploitation steps, and lastly, the Windows exploit methods.
The provided details should allow other security vendors to identify attacks on their customers and track down victims and other similar attacks carried out by the same threat actor.