Not long after Cisco's Talos cyber intelligence unit released its early report on a large-scale hacking campaign that infected more than 500,000 routers and network storage devices in 54 countries, the U.S. government announced the takedown of an internet domain believed to have been used for the attack.
According to the Department of Justice, the botnet, which is a network of computers infected with malware, is under the control of Russian hacking group Fancy Bear, a Russian government-aligned hacking group also known as APT28, Sofacy, X-agent, Sednit, Sandworm, and Pawn Storm.
The hacking group has been in operation since at least 2007, and has been known to have committed a long list of attacks over the past years
The authorities believe that the group used a malware called "VPN Filter".
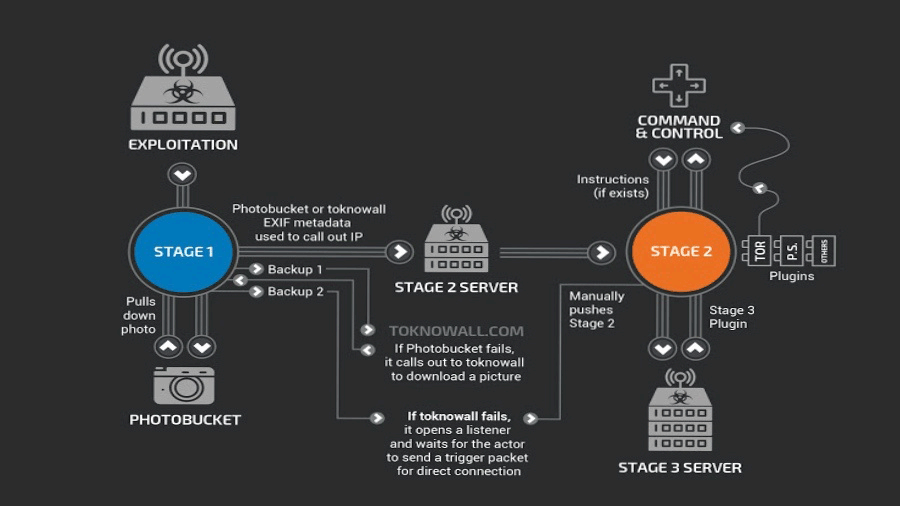
The malware is described as a multi-stage, modular platform that targets small and home offices (SOHO) routers and storage devices from Linksys, MikroTik, NETGEAR, and TP-Link, as well as network-access storage (NAS) devices.
Among other, Cisco's Talos researchers also found evidence that the VPNFilter source code share code with versions of BlackEnergy, a malware responsible for multiple large-scale attacks targeting devices in Ukraine that the U.S. has attributed to Russia.
VPNFilter has been designed to be capable in conducting secret surveillance on its targets and gather intelligence, interfere with internet communications, monitor industrial control (SCADA systems), such as those used in electric grids, factories and other infrastructures, as well as conduct destructive cyber attack operations.
And the seized domain is part of the VPNFilter's command-and-control infrastructure.
"This operation is the first step in the disruption of a botnet that provides the Sofacy actors with an array of capabilities that could be used for a variety of malicious purposes, including intelligence gathering, theft of valuable information, destructive or disruptive attacks, and the misattribution of such activities," said John Demers, the Assistant Attorney General for National Security.
The FBI advised users of SOHO and NAS devices that are infected with VPNFilter, to restart their devices to eliminate the non-persistent second stage malware.