When people are becoming more aware of threats of cyber attacks, they've been ramping up their techniques and security in hopes to defend themselves better, leaving hackers much less option to carry out their malicious deeds.
However, both software and hardware are never a 100 percent perfect. There are flaws, and there will always be flaws on them.
Hackers are relentlessly seeking for new ways to improvise their techniques in order to keep up with people's concern about security. They are continuously altering their tactics accordingly to make attacks more potent and responsive than the previous.
One of the strategy is called the "silent attack".
This improvisation in hacking technique could bypass antivirus and firewall without being detected. This is because the breed of malware has no malware programming coded inside it. The hacking technique is called "the fileless cyber attacks".
In short, hackers can attack without using conventional executable files.
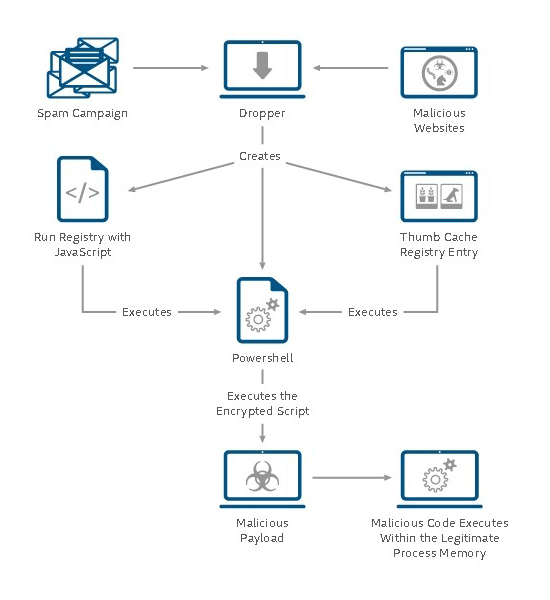
A malicious hacker could therefore gain access to victim's computer with relative ease. By invading weak software and infiltrating the source code, the hacker can embed the code that would then destroy, acquire or delete data without leaving a trace.
The hacker could, for example, control operating system tools such as Windows Management Instrumental or PowerShell.
Silent Attack, Silent Risk
Most malwares involve some writing to the hard disk, in order for them to be executed. Their origin could be traced back to an infected attachment, external media device (USB, peripheral, mobile phone etc.), browser drive-by, side-channel etc..
But fileless malware makes no footprint, and this is worrisome. This potentially makes it more destructive than ransomware.
It works and exists exclusively as a computer memory-based artifact, so it's defined as an Advanced Volatile Threat (AVT). No footprint because it doesn't write any part of its activity to the computer's hard drive.
Related: Polymorphic Malware, And How They Continually Change To Avoid Detection
This type of malware aims to never have to write its contents into hard drives. Its purpose resides in volatile system areas such as the system registry, in-memory processes and service areas.
For this reason, fileless malware can be very resistant to antivirus or firewall, or even anti-computer forensics strategies that incorporate file-based whitelisting, signature detection, hardware verification, pattern-analysis, time-stamping, etc..
Even if it leaves evidence whatsoever, it's pretty much undetectable and very small, making digital forensic investigators difficult in finding identify illegitimate activity.
The attackers behind the attack have various intentions including access to intellectual property, personally identifiable information (PII), or any information relevant to strategic intelligence. Basically, all it involves the hackers in gaining important and personal data.
Hackers In Trading Persistence For Stealth
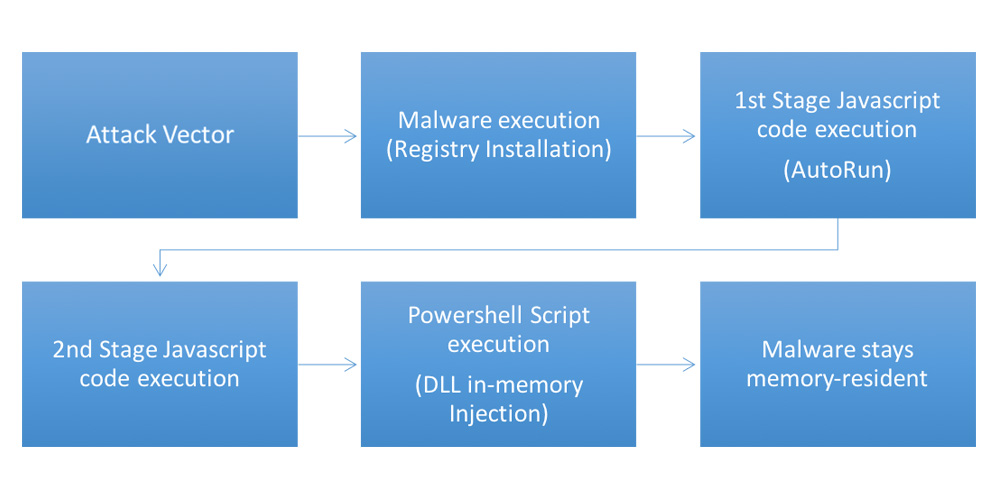
Malicious hackers usually aim for :
- Stealth: with this, they can avoid being detected by security products as long as possible.
- Privilege access: They can exploit a vulnerability to get administrator access to the victim's system.
- Information gathering: The main goal for hackers is to extract as much information they could from the victim.
- Persistence: Keeping the malware inside the system, undetected for as long as possible.
But for fileless malware, hackers are trading persistence for stealth as malware of this type is designed to work from the point of inception until process termination. What this means, its longevity on the system exists only until the system is rebooted.
Since fileless malware can only work as long as the victim's computer is on, and turning off will kill it, threat actors plant registry entries to aid in ongoing attacks by setting scripts to run even after a system has been restarted.
Hackers in keeping the malware infection concealed while it triggers the intended actions is key here.
In order to protect yourself from this type of malware, you need to:
- Keep apps and OS updated at all times: Security updates are crucial for your security./li>
- Block the pages hosting the exploit kit: Block malicious websites so the exploit kit can never reach the applications on your computer.
- Block the payload delivery: The exploit will try to connect to malicious servers, stopping it from doing so will negate the infection before it happens.
- Block the connections: This will prevent the attackers to retrieve data from your PC.
- Use end-to-end encryption and two-factor authentication: This will makes things more difficult for hackers to get real access to data.
- Manage administrators: Have "laws and regulations" to limit users to just what each level of the individual requires.