Another day, another bad day for Google, as another kind of malware has been found on its Play Store.
According to a report disclosed by cybersecurity firm Symantec, and also disclosed by MalwareBytes, the Android malware that was first spotted in May 2019, is capable of reinstalling itself even after being manually removed.
The malware is persistent, even when users performed factory resets on their devices.
In the course of the last six months, the malware is said to have infected more than 45,000 Android devices.
“In the past month alone, there was an average of 131 devices infected each day, and an average of 2,400 devices persistently infected throughout the month,” the company said.
According to MalwareBytes, the malware called Xhelper is a trojan dropper.
This trojan malware mostly infects users in India, the U.S. and Russia. It has since became the top ten most detected mobile malware, with Symantec observing "a surge in detections" of the malicious Android malware.
Symantec suspects the infection is possibly downloaded by users from unknown sources. And according to MalwareBytes, the researchers added that the malware can also spread via shady game websites that tricks unsuspecting users into downloading apps from untrusted third-party sources.
The malware in question runs in the background silently without giving a trace.
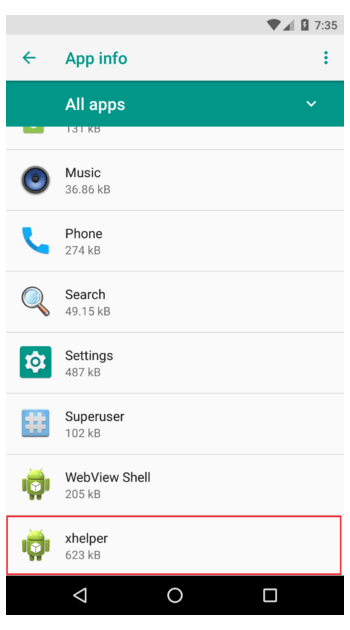
Xhelper takes this stealth behavior by not creating any app icon or shortcut icon. The only indicator about the malware can be seen digging deep into the infected phone's settings.
The first noticeable characteristic of Xhelper is the use of stolen package name that starts with com.muf. While it's usual for a malware to steal others' package names, but usually, the package names were used by popular legitimate apps. In Xhelper's case, the package name was stolen from a simple puzzle app that isn't at all popular.
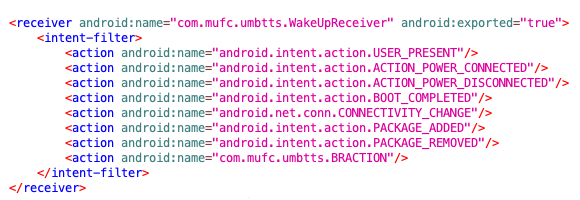
By not having its own app icon, the malware cannot be launched manually.
The trick, is by using external triggers - like when users of the phone connect or disconnect the infected device from a power supply, rebooting a device, or installing or uninstalling an app.
Fortunately, this malware doesn't pack damaging payloads. It doesn't do anything particularly sophisticated, other than bombarding its victims with intrusive pop-up ads and spam the device with notifications for free games.
However, this persistent and stealth malware can also download additional malicious apps, and this makes it more worrisome.
With its stealth capabilities, Xhelper which can download additional malware payloads could easily morph the malware from 'annoying' to 'troubling' security threat. And making things worse, the researcher warned that Xhelper is constantly evolving by expanding its functionalities to target new victims.
To safeguard devices from such attacks, it’s always recommended that users keep their devices and apps up-to-date. People are also urged to stick to the Google Play Store for downloading apps, and be extremely cautious of mobile websites they visit.
Users are also urged to pay close attention to the permissions requested by apps, install suitable mobile security app to protect their device and data, and make frequent backups of important data.