
There are a lot of malware in the wild, with some worse or smarter than the other.
To explain malware and the method they use to evade and run under a virtual environment, security firm Check Point Research has unveiled a malware evasion encyclopedia to give interested individuals the insights into malware, how to counter and defeat them.
With the emergence of new malicious threats, it is becoming necessary for researchers to analyse those threats in some kind of virtualized environment, such as virtual machine (VM) in VMware and VirtualBox, in order to determine their mode of operation.
And this malware evasion encyclopedia also discusses various countermeasures that researchers can use to defeat them.
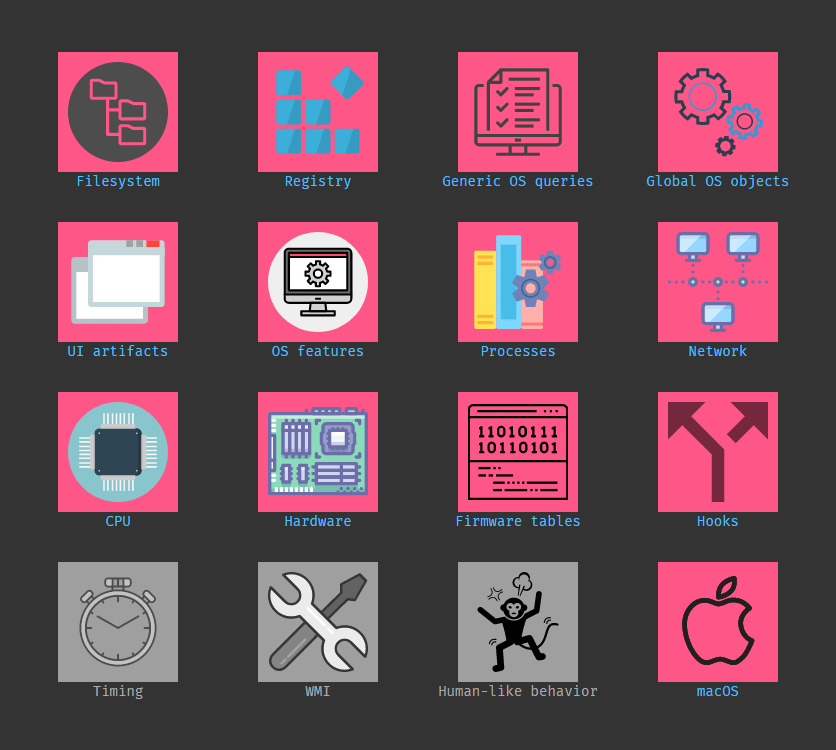
Encyclopedia has different categories of information that a malware will use to detect if it is running under a virtual machine.
The initial sections in the encyclopedia's listed techniques are:
- Filesystem.
- Registry.
- Generic OS queries.
- Global OS objects.
- UI artifacts.
- OS features.
- Processes.
- Network.
- CPU.
- Hardware.
- Firmware tables.
- Hooks.
- Timing.
- WMI.
- Human-like behavior.
- macOS.
Virtual environments usually differ from common host systems in terms of registry keys, non-common files, system objects and other features.
A malware can determine if it is being run in a virtualized environment by sniffing out such artifacts. If the malware detects the use of a VM, it can either not execute itself or will delete itself to prevent analysis.
In Check Point's encyclopedia, the researchers list under each section, the code snippets to illustrate how malware determines if it is running under a virtual environment and also provide suggested countermeasures to defeat these checks.
For example, in the 'Processes' section, the researchers shows how malware checks for certain processes used by VMs. At the 'Firmware Tables', the researchers explain how malware looks for certain strings in the BIOS. And at the 'Generic OS queries' section, the researchers show how malware gather commonly used user names.
While sharing this information may allow malware creators to learn some new techniques and create a more robust malware, Check Point researchers think that the value of the information to the security community far outweighs any benefit to malware developers.
"It is our belief the value of sharing with the community is far greater than the risk of malware authors using this," Check Point Research said.
The company has also created a GitHub page to allow other researchers contribute to the encyclopedia.