Google Docs is Google's answer to Microsoft Word. The word processor comes free, and included as part the web-based suite of apps offered by Google.
And here. the popular app had a serious bug that if exploited, could have allowed hackers steal screenshots of sensitive data on Google Docs documents.
The bug was discovered on July 9, 2020 by security researcher Sreeram KL.
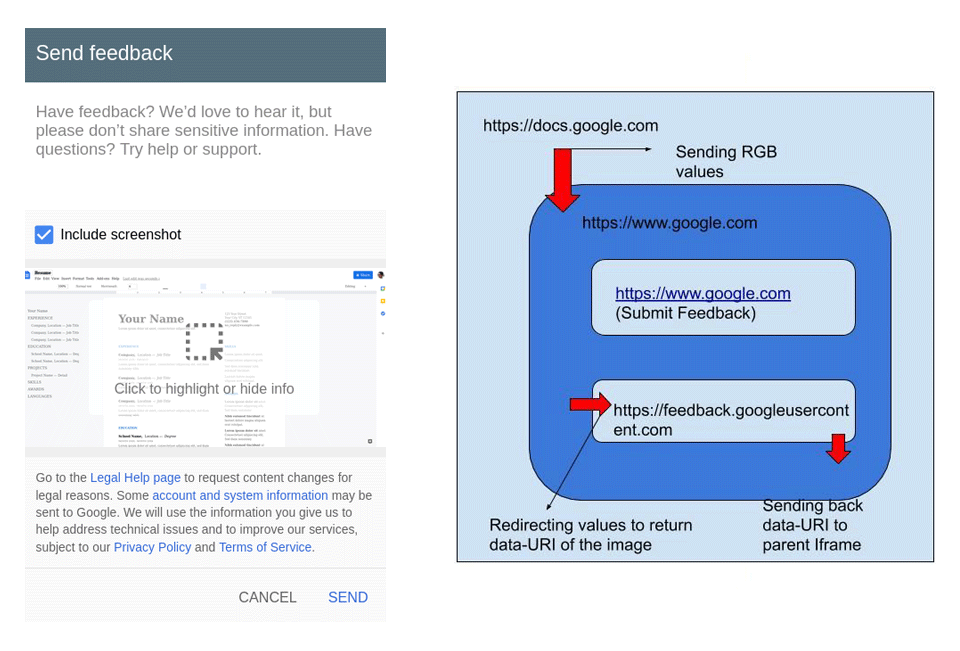
The bug happened to be found on the 'Send feedback' and on the 'Help Docs improve' option.
The features allow users submit feedback, or to highlight specific issues they are experiencing by including screenshots. This in turn should help Google engineers fix issues or implement new functionality that users have suggested.
However, when users agree to send a screenshot with their complaints, the image wasn't taken by Google Docs, but rather by Google.com search engine.
This was on purpose, because it simply saved Google a lot of hassle when duplicating its screenshot function across its various suite of apps, including Google Sheets, Google Slides, Google Drawings, Google Forms, Google Sites, Google Keep and more.
Google created one screenshot feature to handle requests from all of these various Google apps.
In a more detailed explanation, instead of having to duplicate the same functionality across its services, the feedback feature was deployed using Google Search and integrated to other domains via an iframe element that loaded the popup's content from feedback.googleusercontent.com via PostMessage.
Sreeram KL pointed out that Google used this cross-origin communication approach because the origin of the iframe (google.com) is different from one used by Google Docs (docs.google.com).
But here, the flaw was present, which made the system vulnerable to hack.
So here is what could have happened:
When a screenshot of the Google Docs window is included in the feedback, Google rendered the image by transmitting RGB values of every pixel to google.com, which in turn redirects those RGB values to the feedback’s domain, which constructs the image and sends it back in Base64 encoded format.
According to Sreeram KL, this allowed hackers to modify the iframe to an arbitrary, external website, and in turn, steal and hijack Google Docs screenshots which were meant to be uploaded to Google's servers.
The bug was caused by a weakness in the URL structure, which made it possible for hackers to anticipate the incoming screenshots.
Long story short, the flaw mostly stems from a lack of X-Frame-Options header in the Google Docs domain, which made it possible to change the target origin of the message and exploit the cross-origin communication between the page and the frame contained in it.
“After watching the video, I learned a new trick that I didn’t knew before. That is, you can change the location of an iframe which is present in cross origin domain (If it lacks X-Frame-Header). For example, if abc.com have efg.com as iframe and abc.com didn’t have X-Frame header, I could change the efg.com to evil.com cross origin using, frames.location.” wrote the expert in a blog post.
Fortunately, the hack was only possible when users hit the 'Send feedback' button within their document.
What's more, there wasn’t any way for hackers to target individual users. Instead, hackers would need to capture everything coming through the system, or trick specific users into clicking on a rogue website in order to trick them into hitting the 'Send feedback' button.
Although this was possible, the researcher states, the feat is extremely difficult to accomplish. The researchers suggested that it's very unlikely that the bug has been exploited in the wild.
Google has also patched a bug in its feedback tool used across its services.
For his discovery, Sreeram KL was awarded $3,133.70 as part of Google’s bug bounty program.
Google offers between $500 and $31,337 for the most severe attacks identified by researchers. So based on the monetary value he was awarded, Google clearly didn't see the bug as the most concerning. Most notably, this is because despite its severe security issue, it isn't something that hackers could do remotely.
But since millions of people use Google Docs for education, work, and personal notes, this kind of issue could still be pretty problematic.