Gmail is a free email service from Google, and one of the most popular in the world.
Having used by billions of users who rely on Google products and Android, it has had a dangerous bug that could have allowed hackers abuse the email service. If exploited, hackers could send bogus emails right from users' Gmail account, as if they sent them themselves.
Discovered by security researcher Allison Hussain, the so-called spoofing attacks allow cybercriminals to make contact with potential victims from trusted email address or provide a convenient way to cover their tracks.
The bug was reported when users were struggling to use Gmail‘s services due to a rare outage that affected its G Suite products.
Hussain personally disclosed the bug to Google in early April. But because she didn't hear anything back from the company, she sent a notice to say that she intended to publish her findings to the public.
Seven hours after she publicly published her findings, Google finally fixed the critical bug.
The process took 137 days after Hussain first reported it.
Email has been around for a long time, and is still popular due to the fact that it's ubiquitous and it is relied by many online services for registration and logging in.
For almost that long, email has been one of the best way to communicate, especially among businesses and professionals.
Due to its massive usage, email has received numerous improvements to make it more convenient and safe. Like for example, the update which introduces SPF (Sender Policy Framework) and DMARC (Domain-based Message Authentication, Reporting and Conformance).
These two were introduced to make it harder for hackers to send spoofed emails, as the sender's email should first pass checks from the domain's mail server before the message can be sent.
Gmail has supported both SPF and DMARC for some time, but this bug discovered by Hussain, could have allowed hackers bypass those security checks.
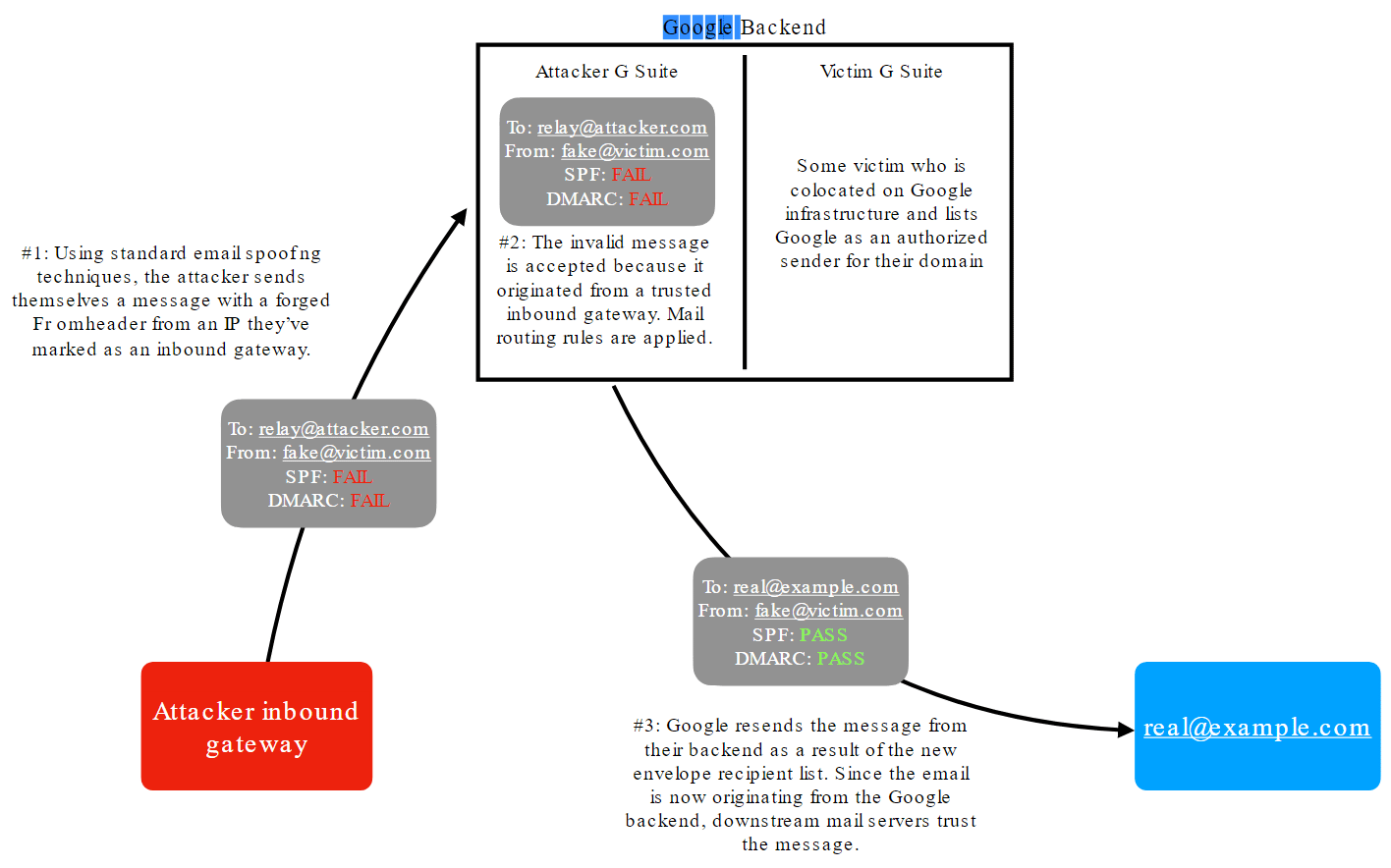
In the blog post, Hussain said that while poking around on the G Suite administrator console, she noticed that she should could create global mail routing rules for inbound mail on her domain using the 'Default routing' option under the 'Settings for Gmail'.
"These rules allowed me to, among other things, apply custom headers, modify the subject line, or change the who the email should be sent to before it is processed by the rest of Google’s infrastructure," she said.
Using the 'Change envelope recipient', she could specify an arbitrary recipient and cause Google’s backend to resend the email to someone else.
Gmail was worryingly accepted the value without performing any validation.
In other words, Hussain created email processing rules that took inbound forged messages and effectively turned them into legitimate messages that Gmail would send on to “victims.”
"This behavior immediately set off alarm bells in my head as I thought back to SPF and DMARC because this buggy feature would let me redirect incoming emails, including spoofed emails, to someone else using Google’s backend so that it no longer appears to be spoofed according to SPF and DMARC if the victim also designates Google as an approved sender!"
To prove what she meant, Hussain sent a test email from a Google.com email address to a mailbox she knew was also hosted by Google.
This was a very serious bug that could’ve been easily exploited by attackers or spammers to send sophisticated and targeted hack attempts.
Google should’ve paid more attention to bug report like this, and address the issue before it was disclosed. Fortunately, Google fixed the critical bug, despite being hours late.