With companies around the world affected by the 'COVID-19' coronavirus pandemic, many rely on cloud services to shift traditional ways of working to remote working.
As a result, corporate data is spread across multiple applications - on-premises and in the cloud - and accessible by users from anywhere using any device. While this is an advantage, attack surfaces expand while network perimeters disappearing. And this means novel attack scenarios and techniques are introduced.
These happen because the trend of people working remotely is forcing hackers to alter their methods of attacks.
And Microsoft here through its Threat Protection, detailed how one sophisticated hacking group was able to hack their way into a network through cracked cloud password, in order to gain full control.
The hackers managed to do that in less than a week.
In a blog post, the team at Microsoft's Threat Protection Intelligence said that:

In particular, the team identified the group it calls HOLMIUM to be behind the sophisticated attacks.
Also referred to as APT33, StoneDrill, and Elfin, the hacking group is known as one of the most proficient in using cloud-based attack vectors - including organized crime and tracking nation-state backed hackers.
This group is widely linked to Iran, and has been performing espionage and destructive attacks targeting aerospace, defense, chemical, mining, and petrochemical companies for years.
Microsoft's researchers said HOLMIUM uses various ways to gain access to its targets, including spear-phishing emails and attempts to use lists of well-known passwords to break into targets' accounts. This technique is better known as 'password spraying'.
However, more recent attacks that the team has observed, have involved methods that use penetration testing tool called Ruler, in tandem with compromised Microsoft Exchange credentials.
The researchers said the hacking group has been running cloud-based attacks with Ruler since 2018, with another wave of such attacks in the first half of 2019.
These attacks typically started with 'intensive' password spraying against exposed Active Directory Federation Services infrastructure; organizations that weren't using multi-factor authentication had a higher risk of having their accounts compromised, Microsoft noted.
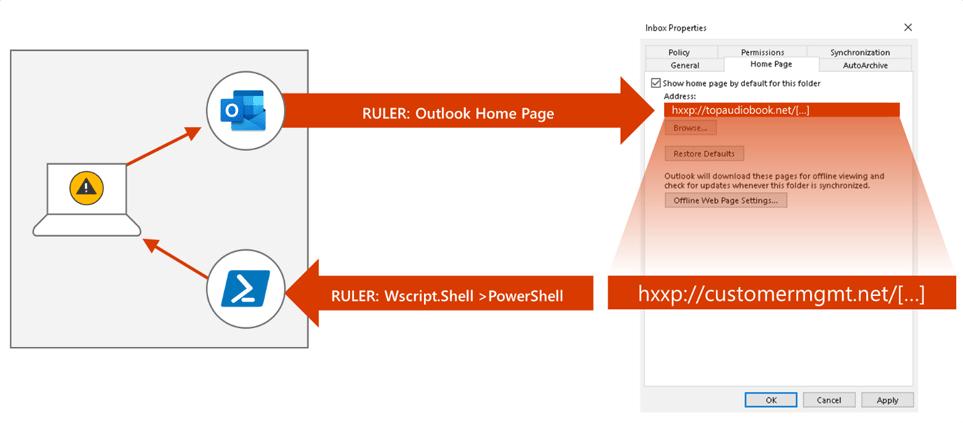
After the hackers managed to compromised some Office 365 accounts, they can then launched the next step of their attacks using Ruler, which gives them the ability to control their victims' PCs.
This way, they can use the compromised PC to expand their attack and do more damage.
This involved finding more user accounts and PCs to attack on the network.
The whole process typically took less than a week from initial access via the cloud to obtaining "unhampered access and full domain compromise", Microsoft said. This access then allowed the attackers to stay on the network their compromised for long periods of time, sometimes for months on end.
"Once the group has taken control of the endpoint (in addition to the cloud identity), the next phase was hours of exploration of the victim's network", Microsoft said.
When attacked, many targets reacted too late.
For example when the malicious activities started manifesting on endpoints via PowerShell commands and subsequent lateral movement behavior, the researchers warned.
"HOLMIUM exemplifies the sophistication of today’s cyberattacks, which leverage techniques spanning organizational cloud services and on-prem devices. Organizations must equip themselves with security tools that enable them to see the attack sprawl and respond to these attacks holistically and automatically. Protecting organizations from sophisticated attacks like HOLMIUM is the backbone of MTP."