
Drupal is the Content Management System (CMS) that comes third in popularity after WordPress and Joomla.
With more than 1 million active developers in the community, the CMS is constantly updated to newer versions to patch bugs and other sorts of vulnerabilities. But that doesn't mean Drupal is free from any critical bug that can be easily exploited by hackers.
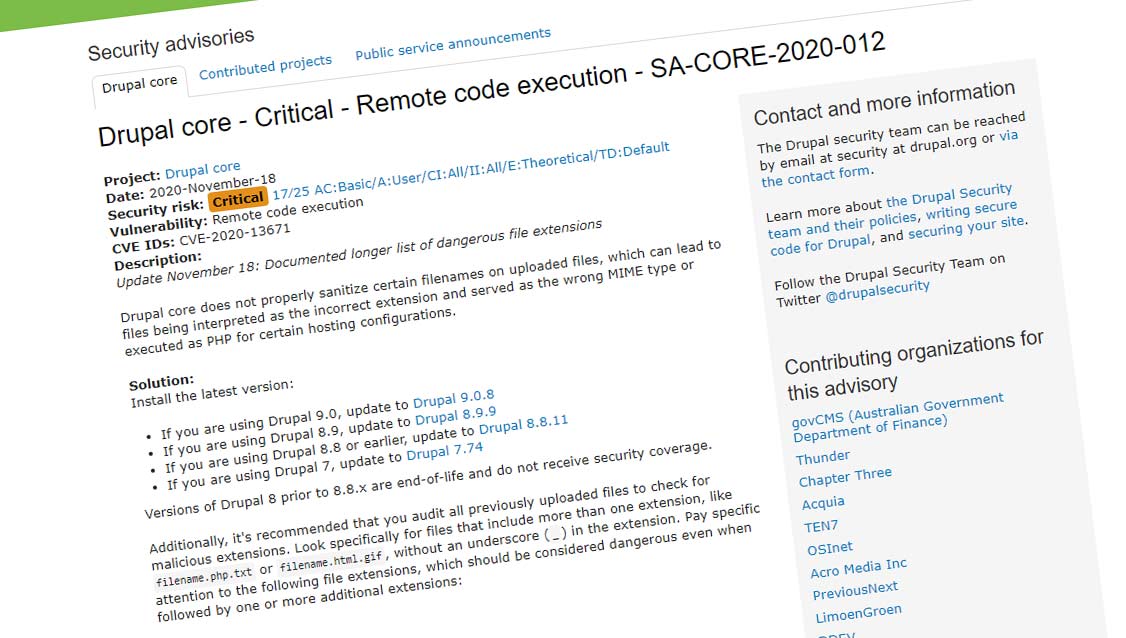
The team at Drupal has discovered a bug, and then patched a critical vulnerability that can grant hackers full control of vulnerable sites, by using the well-known "double extension" trick.
Tracked as CVE-2020-13671, the vulnerability is ridiculously simple to exploit, and can be easily overlooked by careless or inexperienced eyes.
Double extension is a method of tricking someone, or in this case, Drupal, into accepting a file.
It has been for a long time that people know that text files have that .txt extension, and image files can have .gif, .jpg, .png and some others. Many people think that it's safe to open those files because those extensions aren't executables, meaning that running them won't run a program that maybe malicious.
At the same time, people have also learned that files like .exe are executables, meaning that running the files will execute something, and that something can be malicious.
On the web, executable files can have extensions that include .phar, .php, .pl, .py, .cgi, .asp, .js, .html, .htm, and .phtml.
Here, the double extension trick to fool Drupal, is to rename a dangerous file into a seemingly harmless one, like file.txt.php.
When uploaded to a Drupal site, the file would be classified as a text file rather than a PHP file. However, Drupal would end up executing the malicious PHP code when trying the read the text file.
Normally, files with two extensions would be detected, and that should also be the case on Drupal.
But according to its security advisory, Drupal developers said that the vulnerability resides in the fact that the Drupal CMS does not sanitize "certain" file names, allowing some malicious files to slip through the crack.
This in turn "can lead to files being interpreted as the incorrect extension and served as the wrong MIME type or executed as PHP for certain hosting configurations."
Following the finding, Drupal released security updates to correct the file upload sanitization procedures, to all three major versions of Drupal that are active: Drupal 7, 8, and 9.
Drupal developers also urge site administrators to review recent uploads for files with two extensions, just in case that the bug has been discovered and exploited on the site by hackers before being patched.
"This list is not exhaustive, so evaluate security concerns for other unmunged extensions on a case-by-case basis," Drupal developers said.
What makes this bug surprising in Drupal is because the double extension trick is one of the oldest hacking trick in the book. Drupal that has been around on the web for years, powering many popular websites, and this simple hack seemed to have been overlooked for all that time.