
There are endless ways to exploit a system, and attackers have become ever more sophisticated.
Researchers from cybersecurity firm McAfee have discovered 'Anatova', a family of cryptocurrency-fuelled ransomware. While it seems to be harmless at first, but the malware packs a very powerful attack method, making it outright dangerous.
McAfee explained that Anatova hides itself in icon files - usually the same popular games or applications - to fool people into downloading the malware.
Once installed, it will request administrator rights and starts encrypting as many files as possible, as fast as it can. After that, Anatova will demand ransom from the victim, in the form of cryptocurrency DASH.
The company also found over 100 instances of the Anatova running in the U.S., with Belgium, Germany, and France also having a sizable number of infections.
In a blog post, Alexandre Mundo, a senior malware analyst at Mcafee's Advanced Threat Research team, wrote:
"We believe that Anatova can become a serious threat since the code is prepared for modular extension."
According to McAfee, the developers who created Anatova are, possibly skilled malware authors. This can be seen with how the malware's samples received by McAfee have unique keys and functions, uncommon on other ransomware families.
After stripping the malware off its resources, the size is only a mere 32 kilobytes. But still, this very small program has a powerful mechanism built inside it.
This is how it works:
The first action it does when it gets installed, is getting the module handle of the library kernel32.dll to get its 29 functions using GetProcAddress. After that , it will create a mutex (mutual exclusion object) that has a hardcoded name, but can change in every sample.
After that, it will seeks for the error ERROR_ALREADY_EXISTS or ERROR_ACCESS_DENIED.
As both errors mean that a previous instance of this mutex object exists. If this is the case, the malware will continue its work by cleaning the memory.
It will start by getting some functions from the library advapi32.dll, Crypt32.dll and Shell32.dll, check the first language installed on the infected system to prevent the victim from installing some of its blacklisted language to avoid encryption of the files, and loads two particular DLL files for possible future modular capabilities.
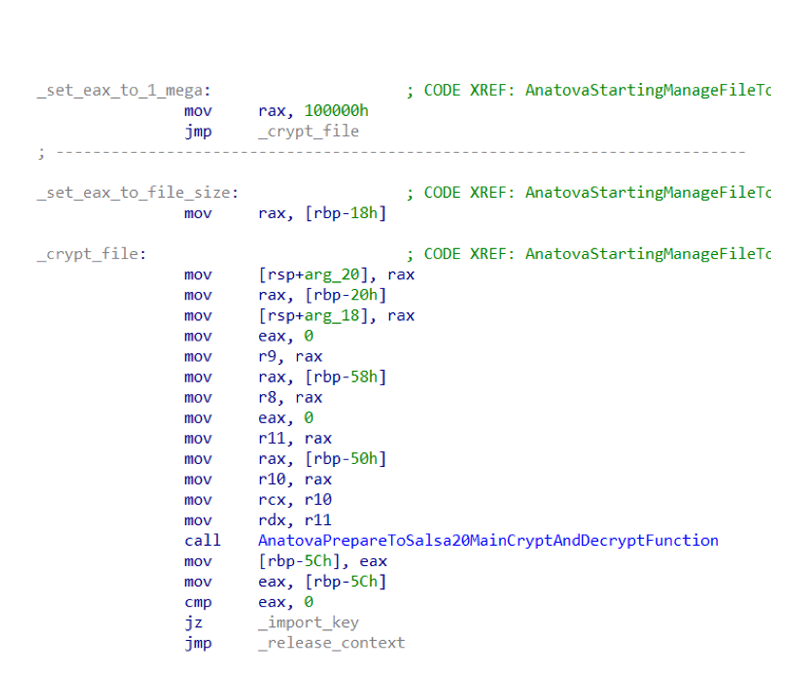
Then comes the encryption.
The malware sees all processes running in the infected system, opens some of them to then terminate them. Typically, this is an attempt to unlock those files so they can be encrypted. These files can include database files, documents files, game files and so forth.
The malware avoids folders like 'Windows', 'Program Files' or some others that are crucial for the operating system. This is usual as the authors want to avoid destroying the system, and only targets highly valued files. The malware also leaves some executables, libraries and system files that are critical to the operating system.
Then it creates RSA Pair of Keys that will encrypt all strings. But here, the malware ensures that all keys are unique, with each key only to be used per user per execution.
After collecting all the available data, it will see the possible files to be held ransom, to know their sizes.
Anatova only encrypt files that are 1 MB or smaller to avoid lost time with big files. This is because the malware is designed to work as fast as possible, to encrypt as many files as possible. This is why it avoids holding big files as ransom, and instead seeks for highly valued files that are smaller in size.
Anatova also makes sure that it does not encrypt files that are already encrypted.
If in any case the above steps and procedures are interrupted, or failed to run, the malware will exit.
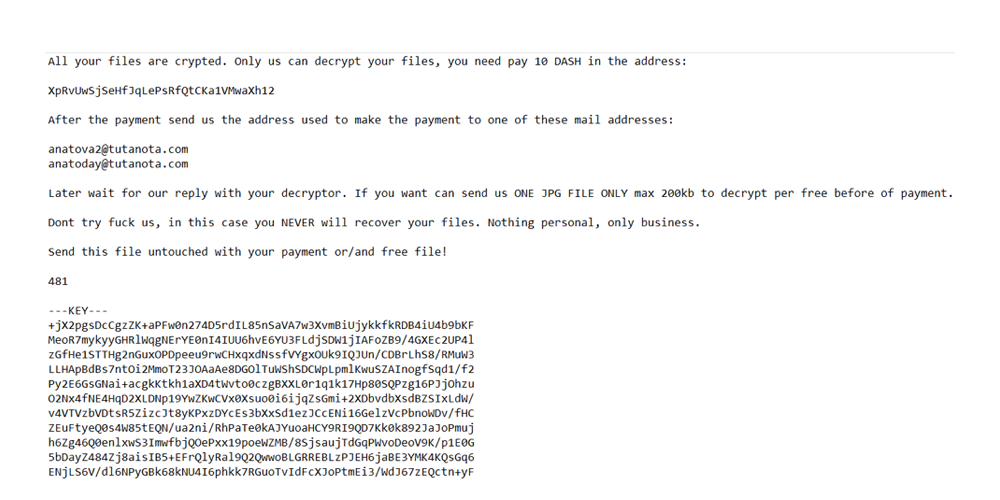
But if it can do what it is supposed to do, the malware will then create a ransom note to the victim, and put that note inside encrypted folders it hold ransom. Responding victims are only allowed to decrypt one JPG file of maximum size 200 KB free of charge, as proof that the author of the ransom note indeed have the decryption keys.
The samples McAfee found use the following MITRE ATT&CK techniques:
- Execution through API.
- Application processes discovery.
- Find files and folders to encrypt.
- Encrypt files.
- Enumerating all processes on the endpoint to kill some special ones.
- Create files.
- Elevation of privileges, requesting it to run.
- Create mutants.
The main goal of Anatova is to encrypt all files it possibly can, as quickly as possible, before requesting payment from the victim.
And what makes it tricky is that the malware has strong protection techniques against static analysis. Most of the strings are encrypted using Unicode and ASCII, have different keys for decryption them, embedded inside executable, and have 90 percent of their calls dynamic.
Since this is the first kind of its family, McAfee doesn't know all entry and couldn't find any version number inside the code. The firm calls it "version 1.0" of the malware.
"Anatova has the potential to become very dangerous with its modular architecture which means that new functionalities can easily be added," explained McAfee’s lead scientist Christiaan Beek. "The main reason [Anatova is] using DASH is that it has implemented a number of privacy enhancing protocols that make tracing transactions difficult."