
The bug was found and patched a long time ago by Google. But a lot of developers failed to update their apps, putting potentially billions at risk.
From Google Chrome, Facebook, Instagram, WhatsApp, Snapchat, Booking, Microsoft Edge, and more. According to the researchers at Check Point Research, at least 8% of all Android apps available on the official Google Play Store are vulnerable to the security flaw.
The bug in question resided in the popular Google Play Core library.
The Play Core library is a crucial element in enabling developers to push their own in-app updates and new feature modules to live apps.
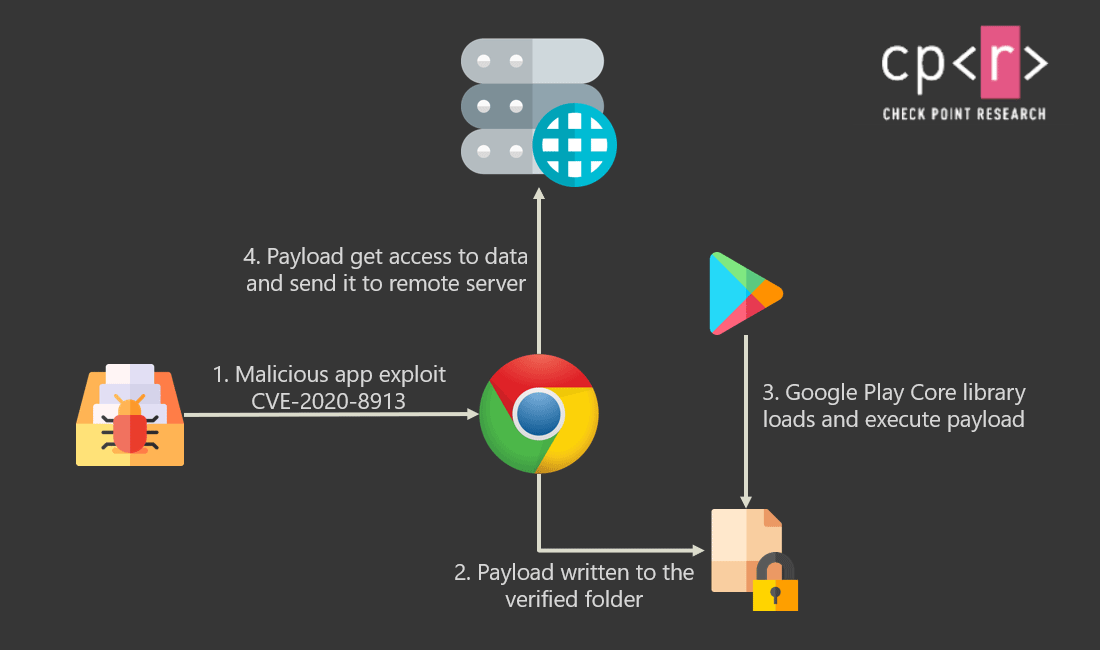
And the vulnerability, CVE-2020-8913, allowed arbitrary code execution issue in the SplitCompat.install endpoint in Play Core Library prior to version 1.7.2. The flaw enables a malicious actor to create an Android Package Kit (APK) targeting a specific app that lets them execute code as the targeted app, and access its data on the user device.
The flaw, which ranks 8.8 out of 10 on the CVSS v3 scale, is severe, because of the private data hackers can obtain, including login credentials, financial details, private messages or photos.
The flaw also allows malicious actors to inject code to apps to not only obtain sensitive information, but to also spy and gain access to corporate resources, steal two-factor authentication (2FA) codes, send messages on the victim's behalf, and much more.
"The possibilities are limited only by our creativity," Check Point Reearch said.
To demonstrate, Check Point used a proof-of-concept malicious app to steal an authentication cookie from an old version of Chrome. With possession of the cookie, the attacker is able to gain unauthorized access to a victim's Dropbox account.
This flaw “is extremely easy to exploit,” added the researchers.
“All you need to do is to create a ‘hello world’ application that calls the exported intent in the vulnerable app to push a file into the verified files folder with the file-traversal path. Then sit back and watch the magic happen.”
This is possible because the vulnerability stemmed from a directory traversal flaw that allowed untrusted sources to copy files to a folder that was supposed to be reserved only for trusted code received from Google Play. The vulnerability undermined a core protection built into the Android that prevents one app from accessing data or code belonging to any other app.
The bug was detailed back on August 2020 by security firm Oversecured.
While the bug has been patched, the researchers at Check Point warned that the patch still needs to be pushed out by developers for several applications. Failure has led to apps being vulnerable to the bug.
The bug wasn't completely eliminated when Google patched on 6 April 2020, because the bug is a client-side vulnerability - as opposed to a server-side vulnerability which can be patched completely and immediately once a patch is applied.
Because the bug is local, the ones that can push the update, are the developers of the apps themselves.
Developers of apps must first download the updated library, and then incorporate it into their app code.
Making things worse for users, is Android's fragmented ecosystem.
While Google can push certain security updates directly to users, and developers can push the updates through updating their apps, manufacturers of Android devices including Huawei, Samsung and Xiaomi ship their devices with different levels of security in different regions. This again is leaving users exposed to attacks.
In a blog post, Aviran Hazum, Check Point’s manager of mobile research, said that:
"We’re estimating that hundreds of millions of Android users are at security risk. Although Google implemented a patch, many apps are still using outdated Play Core libraries."
“The vulnerability CVE-2020-8913 is highly dangerous. If a malicious application exploits this vulnerability, it can gain code execution inside popular applications, obtaining the same access as the vulnerable application. For example, the vulnerability could allow a threat actor to steal two-factor authentication codes or inject code into banking applications to grab credentials."
"Or a threat actor could inject code into social media applications to spy on victims or inject code into all IM apps to grab all messages. The attack possibilities here are only limited by a threat actor’s imagination."
At the moment of its findings, besides existent in some of the most popular apps on the market, the flaw also remains in Bumble, Grindr, PowerDirector, Xrecorder and Yango Pro. This however, is only a small, randomly selected sampling of high-profile apps studied by Check Point.
Four apps in the original sampling, like Booking, Cisco Teams, Moovit and Viber, have since confirmed they have corrected the issue.