
As the most famous and flexible mobile operating system, it seems that there is no end to Android security issues.
This time, researchers from app security startup Oversecured discovered a security vulnerability, where hackers could inject malicious modules into other apps that rely on Google Play Core Library to steal sensitive information from other apps on the same Android device.
Google’s Play Core Library allows developers to push in-app updates as well as new feature modules to their Android applications such as game levels and language packs, without the participation of the user, via the Google API.
It can also be used to reduce the size of the main .apk file by loading resources optimized for a particular device and settings.
And here, hackers could exploit the flaw in it to grant their malicious apps the access to harvest the private data stored by other apps.
Founder of Oversecured, Sergey Toshin, said that exploiting this security vulnerability was pretty easy.
In a blog post the researchers at Oversecured said that,
To show what he meant, Oversecured created a proof-of-concept application using only a few lines code.
The startup then tested it on Google Chrome for Android, which relied on the flawed library.
Toshin said that the proof-of-concept application was successful in stealing the passwords, browsing history, and login cookies of the victim.
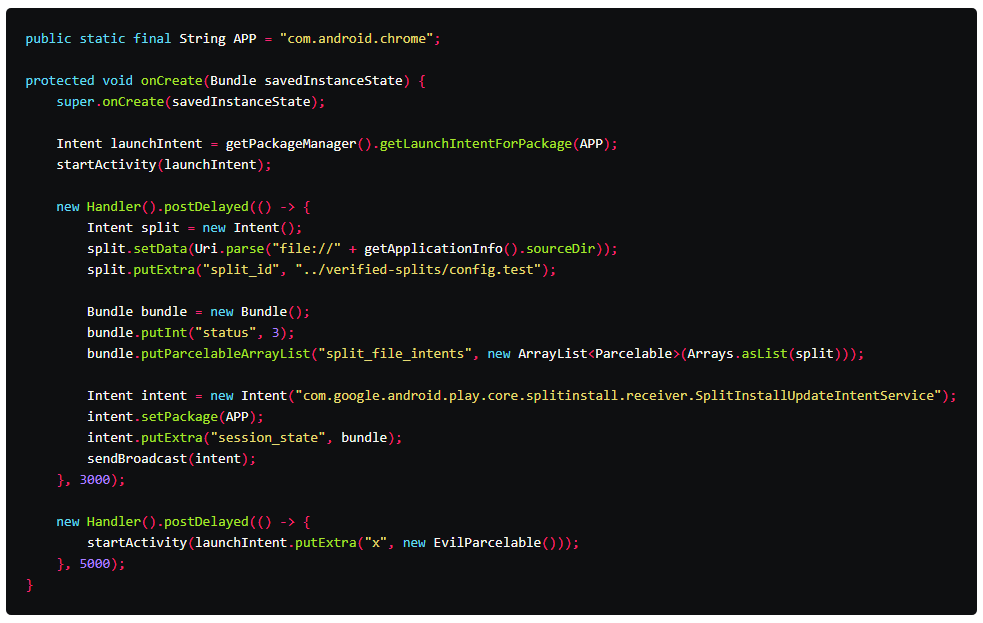
This bug that was found on Google’s Play Core Library versions prior to version 1.7.2, made it possible for apps to "inject modules" into other Android apps on the same device.
Toshin also said that the vulnerability impacted some of the most popular Android applications in the Google Play Store.
Due to the fact that the vulnerability is present on most Android devices, Toshin recommended developers to update their apps with the latest version of Google’s Play Core Library to avoid any security threats.
In March, Google confirmed this security bug and fixed the vulnerability. Furthermore, Google rated this bug 8.8 out of 10.0 for the severity of its threat.
Google appreciated the security researcher reporting this bug, and as a result, the company patched the Android bug back in March 2020.
Google suggests that all users update Google’s Play Core Library to version 1.7.2 or later.