Putting a website on the web involves tedious process. To make the process manageable, webmasters can rely on a web hosting control panel.
One of the most popular, is cPanel. The web hosting control panel facilitates the management of a web hosting server through a user-friendly graphical interface and automation tools that are meant to simplify the whole process, even for the least knowledgeable of users.
Trusted by more than 70 million domains, a major flaw was found on this popular control panel.
Security researchers from Digital Defense found that the cPanel software suite allows attackers to bypass two-factor authentication (2FA) for accounts.
What this means, once hackers managed to get through the authentication, they will gain access to practically everything.
Compromising a website's cPanel control panel, would allow hackers to access the underlying server settings and more. This is critical, as once compromised, hackers can get full control over a victim's site.
On the announcement, the team at Digital Defense said that:
The bug here is a zero-day, meaning that the bug was an unknown exploit before the team found it.
What makes it worrying is that, the brute-forcing attacks, which in general can take hours or days or even longer to execute, in this particular case, only requires a few minutes.
But before the attack can be launched successfully, hackers need to have the first valid login credentials for the targeted account, which can be obtained through phishing.
This findings to some website owners, may not mean anything, considering that the hackers must first know their login credentials.
However, two-factor authentication solutions were invented to protect against the use of phished credentials. With cPanel having this bug, it means that the 2FA is not as secure as people thought it would be, thus needed to be treated with utmost urgency.
When the team at Digital Defense has privately reported the bug, which is tracked as SEC-575, to cPanel, the team at cPanel quickly released a patch to squash the bug.
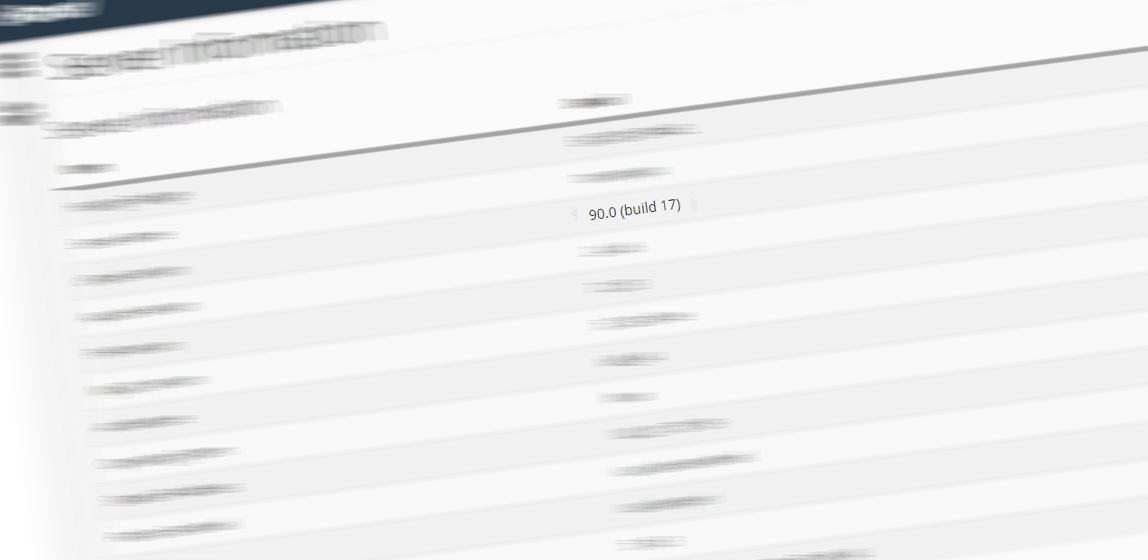
Website owners who use 2FA on their cPanel login can see if their web hosting provider has updated the control panel with the patch, by checking the control panel's version number. This can be seen after first logging in into cPanel, and going to 'Server Information'.
According to cPanel's full disclosure, the 2FA bypass issue has been patched in cPanel & WHM software version 11.92.0.2, 11.90.0.17, and 11.86.0.32.
On its changelog, cPanel wrote that besides SEC-575, the team has also fixed URL parameter injection vulnerabilities in multiple interfaces (SEC-567), and fixed the self-XSS vulnerability in WHM Transfer Tool interface (SEC-577).