
Every month, Google discloses all Android security vulnerabilities and their patches. This March is no exception.
The company patched more than 70 software vulnerabilities in its Android Security Bulletin in March. But what was different is that, Google finally fixed a severe security exploit for MediaTek chipsets that is said to have been in the wild for months, affecting millions of devices.
Called the CVE-2020-0069, it's a critical security exploit, specifically a rootkit affecting chipsets from the large Taiwanese chip design company. Although the March 2020 Android Security Bulletin patched the bug, the details of the exploit has been around on the web, more specifically, on the XDA-Developers forums, since April 2019.
Despite MediaTek patched the bug a month after it was discovered, the vulnerability is still exploitable on dozens of device models.
With hackers actively exploiting it, this is why MediaTek turned to Google to push the patch to its millions of users.
XDA-Developers is a popular forum for Android developers and hackers, focusing on modifying the operating system.
As explained on its web page, it started when XDA Senior Member diplomatic wanted to root Amazon Fire tablets.
These devices tend to be heavily locked down to prevent buyers from going out of Amazon's walled garden. This is why Amazon doesn't share any official method to unlock its tablet's bootloader, which is needed to disable verification of the boot partition.
Because there is no way to unlock the bootloader, which is needed to root any Android device, the XDA member needed to first find an exploit for Android to bypass the operating system's security model.
But when the XDA member succeeded in finding an exploit and shared it in his thread, he quickly realized that this exploit was far wider in scope than just Amazon’s Fire tablets.
After a bit of testing from other community members, it was confirmed that this exploit works on a large number of MediaTek chips.
The author states that the exploit works on “virtually all of MediaTek’s 64-bit chips.”
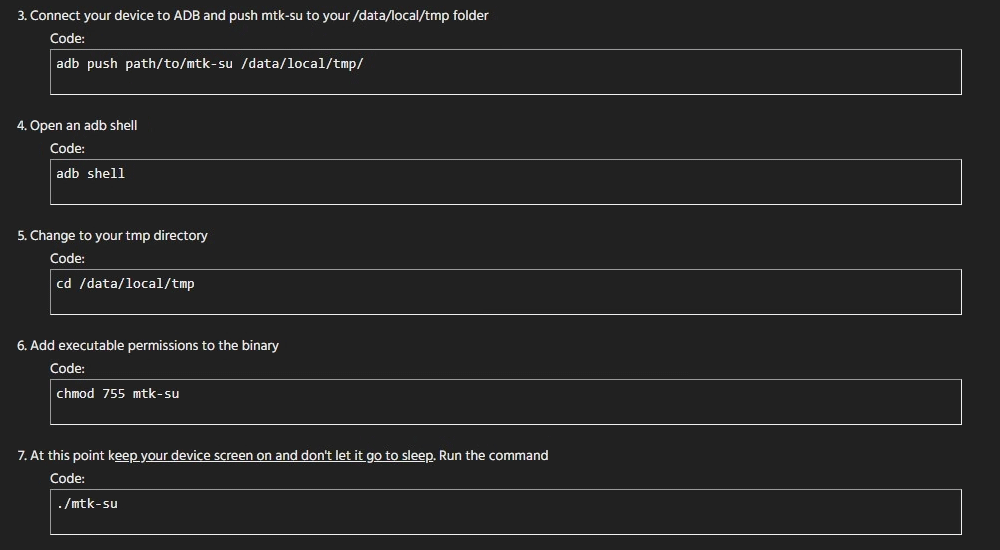
The flaw was present because MediaTek chips don't lock the bootloader. What this means, hackers can easily unlock it to get root access.
In order to exploit this flaw, hackers can simply copy a script to a target device and execute it within the shell. What makes it extremely dangerous is that, any app can do this.
Any app with permission to access storage, can copy the MediaTek-su script to their private directory and then execute it in shell to gain root access. When this happens, hackers are then free to do anything they want because the Android's security model isn't anymore working.
With no permission needed to access anything, hackers can read everything stored inside victims' phones, including files stored in the typically inaccessible private data directories of applications. With the app, hackers can also install any other apps in the background, including ransomware, cryptojacking malware or others, grant whatever permissions the hackers want for apps, and do even more damage from there.
In short, the victims' phone is like an open book ready to read or have its papers ripped off.
According to MediaTek, this vulnerability affects its chips with Linux Kernel versions 3.18, 4.4, 4.9, or 4.14 running Android versions 7 Nougat, 8 Oreo, and 9 Pie.
MediaTek couldn't force device makers to implement the patches, but Google could. This is because Google can force OEMs to push the update through license agreements and program terms. But what makes it concerning is that, Google knew about this bug, but took months before fixing it.