
Software bugs need to be squashed, They need to be eliminated, deleted, obliterated, and annihilated. But still, more can live under the radar, until they are discovered.
Microsoft security researchers, who work with the Microsoft 365 Defender Research Team, discovered a serious vulnerability in the TikTok Android app that could enable 1-click account takeovers. All that is required, is enticing victims to click on one single malicious link.
"The vulnerability allowed the app’s deeplink verification to be bypassed. Attackers could force the app to load an arbitrary URL to the app’s WebView," Microsoft said on its report, adding that the bug is "allowing the URL to then access the WebView’s attached JavaScript bridges and grant functionality to attackers."
This bug can bypass user login by triggering a request to a controlled server in order to log cookie and request headers to grab the user's TikTok authentication token.
In other words, all it takes is one click to create a successful attack.
The bug is so severe, that the CVE-2022-28799 gets a high 8.8 rating, and is described at the National Institute of Standards and Technology (NIST) as allowing "an attacker to leverage an attached JavaScript interface for the takeover with one click."
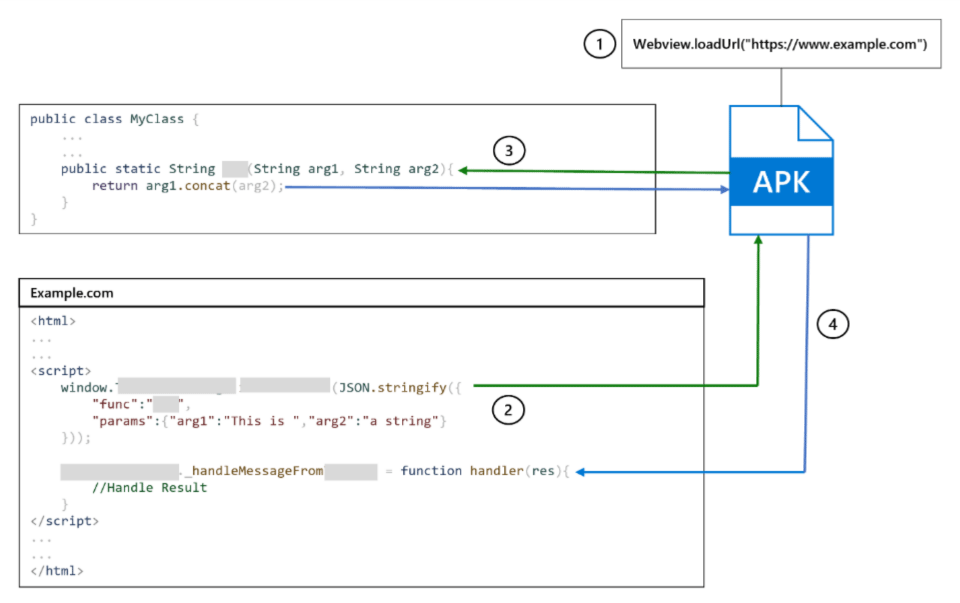
The bug can be exploited, when victims click on a maliciously crafted link.
Clicking on the malicious link would exploit the built-in JavaScript code, which would then allow the attackers to have access to modify victims' user information or profile settings.
Not only that, because the bug also allow the bad actors to turn private videos public, sent messages to friends or strangers, or even upload new videos to the victims account.
Because the bug allows attackers to have complete access, it also expose victims bare, because attackers could also collect victims’ account information, including passwords, emails, or other sensitive data.
TikTok on Android has two versions.
The first is for users in East and Southeast Asia, and the second is for the rest of the world. Microsoft that performed a vulnerability assessment, said that both versions were impacted, meaning the vulnerability hit a total of 1.5 billion installations.
This bug affects TikTok's Android app version 23.7.3 and lower.
As a proof of concept, the team at Microsoft crafted a link to a targeted TikTok user.
Once the user clicks on the link, the video uploading authentication tokens are sent back to the attacker and subsequently, the script modifies the user’s biography information to read “!! SECURITY BREACH !!”.
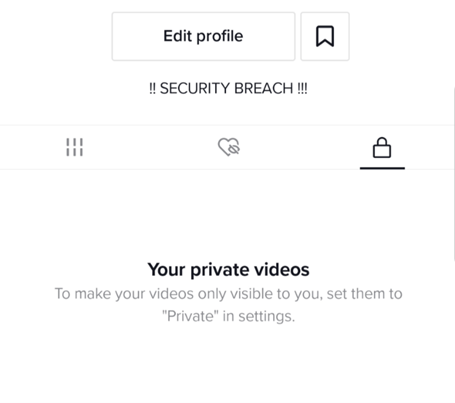
To exploit this bug required several issues to be chained together.
Fortunately, no cases have been found in the wild, according to Microsoft. What this means, no one is likely to have been affected by it.
Microsoft reported the issue through Coordinated Vulnerability Disclosure (CVD) via Microsoft Security Vulnerability Research (MSVR) in February of 2022.
The bug was then patched by TikTok a month after the disclosure.
Dimitrios Valsamaras from the Microsoft 365 Defender Research Team recommends users the following to defend against any similar security exploits:
- Avoid clicking links from untrusted sources.
- Always keep the device and the installed applications updated.
- Never install applications from untrusted sources.
- Immediately report any strange application behavior to the vendor, such as setting changes triggered without user interaction.