As Google Chrome retains an iron grip on market with its 2 billion users, it has that many reasons to protect the popular web browser.
And this time, Google has sent an alert in an official blog post, confirming serious security problems in its Chrome web browser, and urged all users to update.
In the update, Google has included four security fixes, with each of the four is marked “high” which means that they are critical updates:
- CVE-2021-30554: Use after free in WebGL.
- CVE-2021-30555: Use after free in Sharing.
- CVE-2021-30556: Use after free in WebAudio.
- CVE-2021-30557: Use after free in TabGroups.
Among the four, CVE-2021-30554 is a 'zero-day' exploit.
What this means, the vulnerability is known to hackers and actively being exploited.
The bug that is found in Chrome's WebGL, the JavaScript API for rendering. The so-called "Use after Free" bug, allows hackers to access memory even after it has been de-allocated to the app.
A remote attacker can create a specially crafted web page, to then trick victims into visiting it, and trigger the use-after-free error to execute arbitrary code on the target system.
The CVE-2021-30554 flaw is the 7th known zero-day exploit for the Chrome browser this 2021.
“Google is aware that an exploit for CVE-2021-30554 exists in the wild,” is all Chrome technical program manager Srinivas Sista has said.
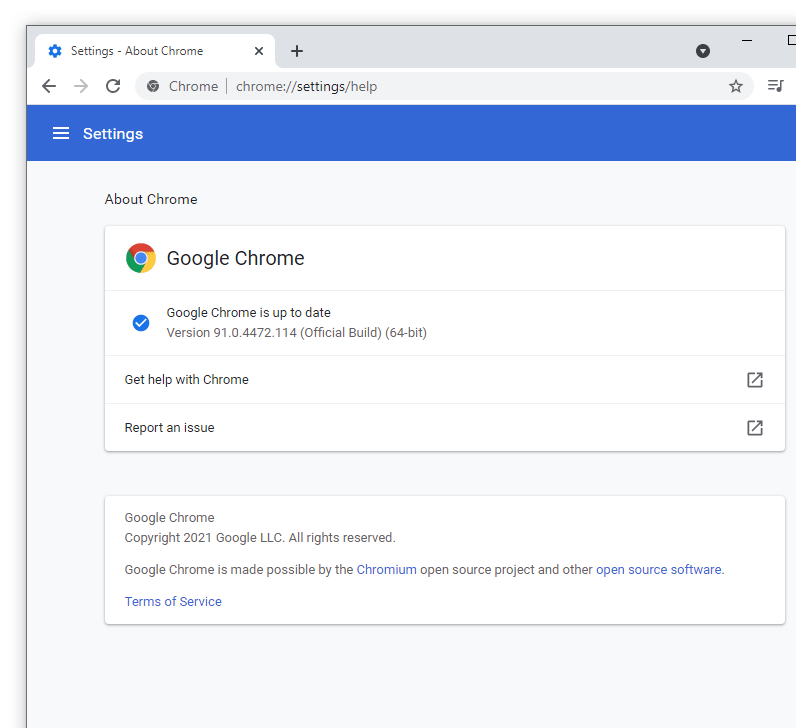
The updates have been pushed through Chrome's Stable channel at version 91.0.4472.114 for Windows, Mac and Linux.