Any digital information can be put on the internet. This allows lots of advantages.
But one big disadvantage is security and privacy. This is once something is put on the internet, it can be accessed from anywhere. What's required to access it, is the correct credentials to have access to the data, and/or the appropriate method of approach.
And this time, tech giant Microsoft has become a victim of yet another attack by Lapsus$.
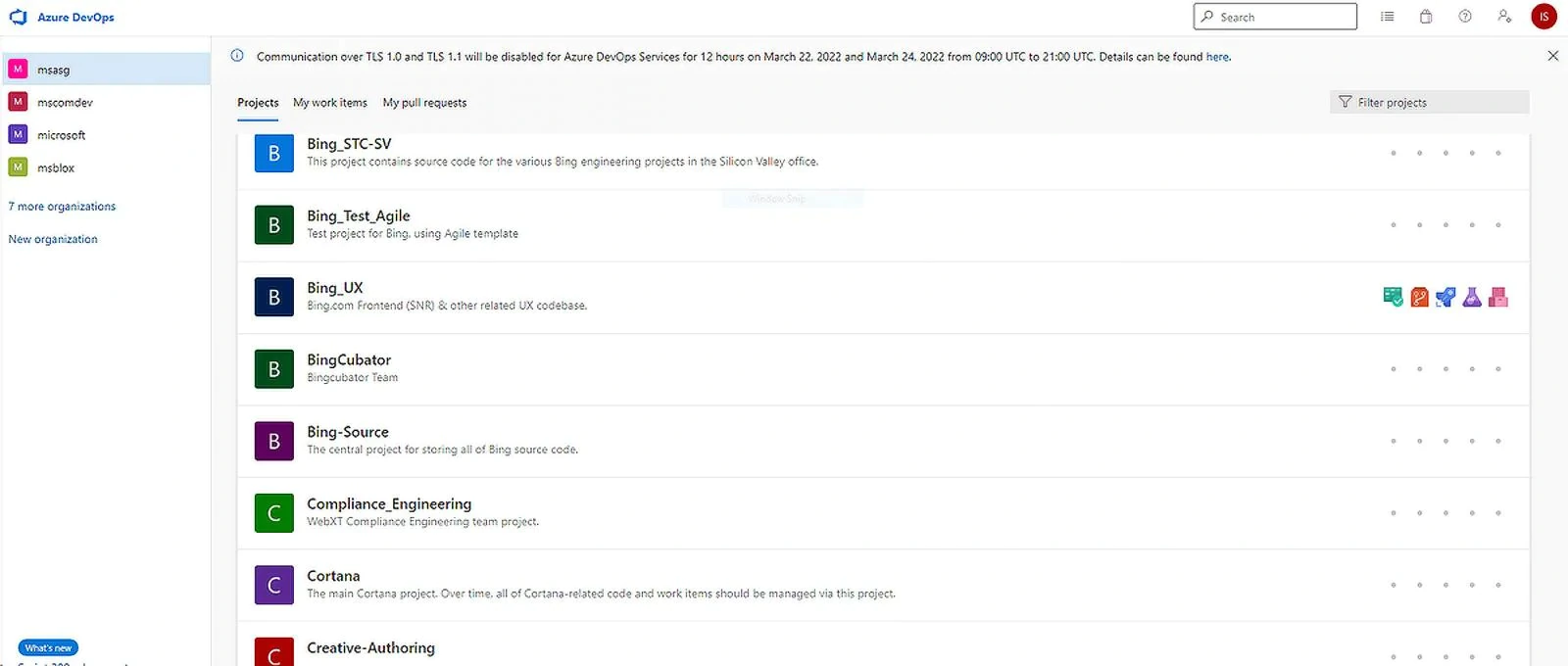
The notorious hacking group that has previously stole data from Nvidia, Samsung, and Ubisoft, has gained access to Microsoft's internal systems, and copied a number of sensitive data from Microsoft's Azure DevOps server.
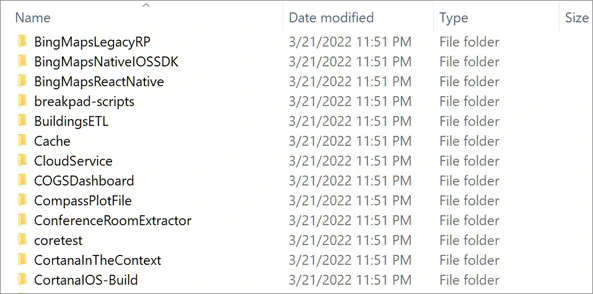
They include internal emails and documentations, as well as a whopping 37GB worth of source codes for around 250 Microsoft projects, including Bing, Cortana and Bing Maps.
And to prove that it managed to steal from Microsoft, the hacking group posted a screenshot of what it claimed contains partial source code for the Microsoft software.
The hacking group has also released 9GB worth of the data in 7zip to the internet for anyone to download.
"We are aware of the claims and are investigating," said Microsoft in its initial response.
Later, the company confirmed the breach, and said that the hackers managed to hack its system by hacking one its employees' accounts.
When Lapsus$ compromised the Microsoft employee, this allowed the threat actors to access and steal portions of the company's source code.
Fortunately, Lapsus$ only had limited access to Microsoft's source code repositories.
What's more, no user data was stolen.
"No customer code or data was involved in the observed activities. Our investigation has found a single account had been compromised, granting limited access. Our cybersecurity response teams quickly engaged to remediate the compromised account and prevent further activity," explained Microsoft in a blog post.
"Microsoft does not rely on the secrecy of code as a security measure and viewing source code does not lead to elevation of risk. The tactics DEV-0537 used in this intrusion reflect the tactics and techniques discussed in this blog."
"Our team was already investigating the compromised account based on threat intelligence when the actor publicly disclosed their intrusion. This public disclosure escalated our action allowing our team to intervene and interrupt the actor mid-operation, limiting broader impact."
Microsoft that tracks Lapsus$ as 'DEV-0537', said that the hacking group's primary focus is obtaining compromised credentials for initial access to corporate networks.
One they get their hands on the credentials, they can use them to log in into a company's public-facing devices and systems, including VPNs, Virtual Desktop infrastructure, or identity management services.
And once they managed to do that, the threat actors will then use their higher privilege to target development and collaboration platforms.
This is where they can get access to data on SharePoint, Confluence, JIRA, Slack, and Microsoft Teams, where more data are then stolen.
The hacking group also uses these credentials to gain access to source code repositories on GitLab, GitHub, and Azure DevOps.
After gathering all the necessary data, the hackers will then exfiltrate it over VPN connections to hide their locations.
Lapsus$ is a relatively young hacking group.
But despite being a newcomer, the group has successfully breached some of the largest tech companies in the world. It first made its name after hacking into Brazil’s Health Ministry, and stole COVID-19 vaccination data.
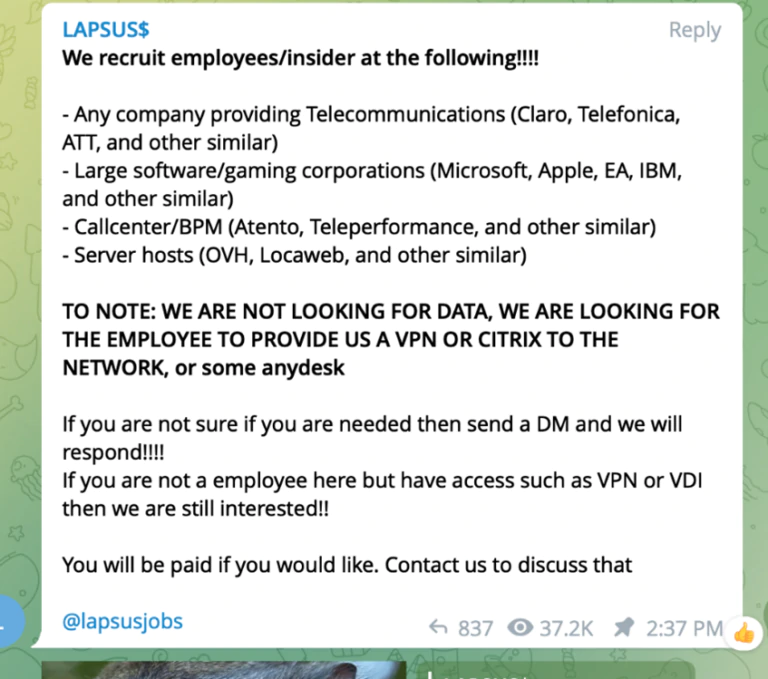
And this time, Lapsus$ is reportedly on a recruiting mission to get employees to give them access to sensitive information.
"We recruit employees/insider at the following!!!!" the hackers wrote on March 10, to then list a number of companies it would like to infiltrate, which included Apple and IBM.
"TO NOTE: WE ARE NOT LOOKING FOR DATA, WE ARE LOOKING FOR THE EMPLOYEE TO PROVIDE US A VPN OR CITRIX TO THE NETWORK, or some anydesk," the group wrote in a Telegram message.
The Lapsus$ hackers do this because they aren't concerned with hiding their activities.
After all, their hacking methods, according to Microsoft, have included methods like phone-based social engineering, and SIM-swapping. The hackers had also payed/bribed employees and vendors at targeted organizations so they can be given the access to credentials.
The hackers are expert in their social engineering skills.
"The actors behind DEV-0537 focused their social engineering efforts to gather knowledge about their target’s business operations. Such information includes intimate knowledge about employees, team structures, help desks, crisis response workflows, and supply chain relationships. Examples of these social engineering tactics include spamming a target user with multifactor authentication (MFA) prompts and calling the organization’s help desk to reset a target’s credentials," said Microsoft.
And what makes this Lapsus$ different than most of its peers is that, it doesn't only speak on hacking forums.
Instead, the group has established a social media presence, and post things on its Telegram channel.