
Android is an open ecosystem, allowing phone manufacturers to put their own apps before shipping their devices to customers.
Unlike Google's Pixel phones that promises stock Android user experience, Android phone manufacturers can customize their phones to meet specific needs, by adding themes, skins, functionalities or apps, on top of the stock Android.
And here, researchers found that not only manufacturers' apps are bloatware, but also filled with security flaws.
To be exact, 146 flaws were found inside pre-installed apps from Android phone manufacturers.
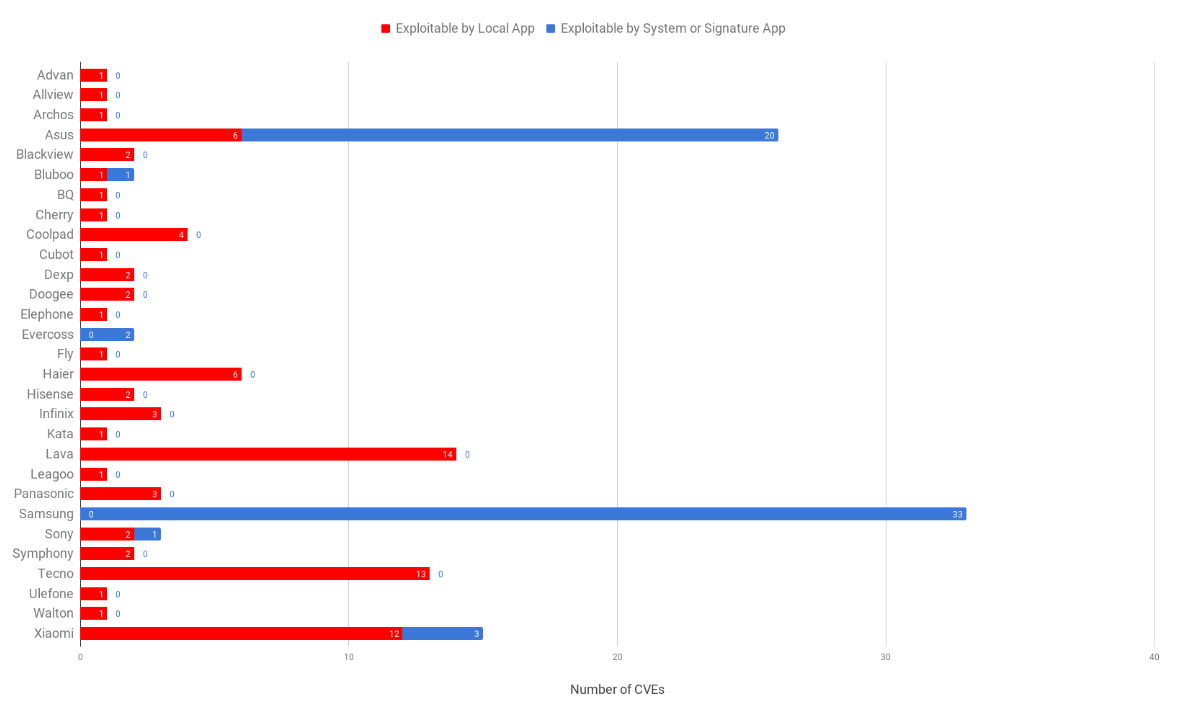
Discovered by researchers at Kryptowire, the flaws were found to be present across apps from 29 Android OEMs (Original Equipment Manufacturers).
Funded by the Department of Homeland Security, the researchers suggest that the security and privacy issues range from unauthorized app installs to the ability to modify system and wireless settings, and even record audio.
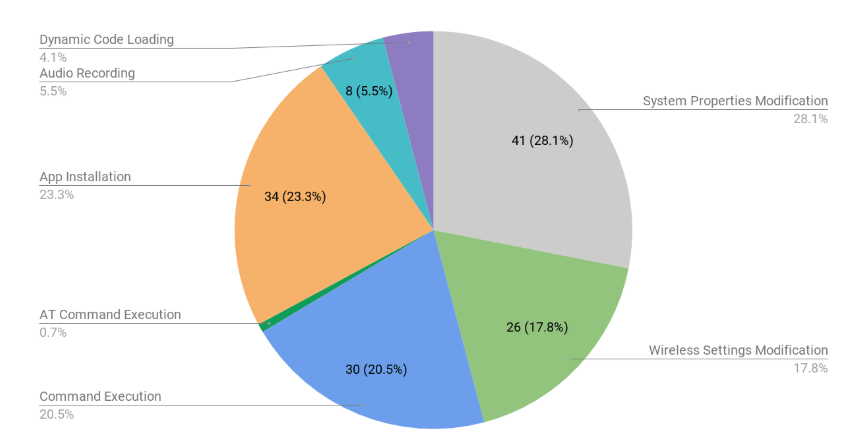
According to Kryptowire on its findings:
Underscoring the vast scope of the problem, the OEMs include well-known companies, like ASUS, Samsung, and Xiaomi.
After the discovery went public, Samsung quickly disputed the findings.
In a statement to Wired, the South Korean conglomerate giant stated that "we have promptly investigated the apps in question and have determined that appropriate protections are already in place.”
Google too has its own security procedure to prevent flawed apps to spread. Google has leveraged a system called Build Test Suite (BTS) to scan for potentially harmful pre-installed apps across custom Android builds for devices that ship with its services.
As the company explains in its 'Android Security 2018 Year in Review' report released earlier this March:
But still, despite the companies' security checks in place, the researchers suggest that questionable apps managed to continue slipping through the crack.
What makes the situation difficult to solve by users is because the apps are OEM apps. Because they pre-installed right from the factory, the apps cannot be uninstalled like third-party apps. And making things even worse, there is no saying when these apps will be patched or fixed.
Google, for its part, has been actively trying to weed out harmful apps from its Google Play Store.
Just recently, Google formed 'Defense Alliance' by partnering with ESET, Lookout, and Zimperium to identify shady third-party apps before they end up on users’ devices.