
Google Play Store has millions of apps. With the many varieties available, there are good apps, and there are bad apps.
Cheetah Mobile is perhaps one of the most famous for its tools apps for Android. Based in China, the company has created many products which many are well-known. From Clean Master and Security Master, to CM Launcher, CM Browser, Batter Doctor and many more.
With billions of downloads under its belt, Cheetah Mobile have products that topped Google Play Store's chart.
However, reports said that the company is serving tons of sketchy advertisements, based on its malicious practice of collecting data on users' activities.
In research from Kochava, which was then delivered to BuzzFeed News, it was said that several apps from Cheetah Mobile, and one from Kika, are allegedly engaging in ad fraud. While Cheetah Mobile is best known for developing utility apps on Android, the company actually focuses on selling user data.
In fact, Cheetah Mobile doesn't hide this at all.
This can be seen with app permissions like Play Install Referrer API, network connection details, activity recognition, retrieving running apps, and many more which are not at all required for cleaning the cache of an Android device.
As Kochava explained, all of the above permissions are actually being used as part of its ad fraud scheme.
Providing free apps for the masses, it's obvious that Cheetah Mobile wants revenue.
In the mobile ad industry, developers generate money by placing ads on their apps. It works like this: apps displays ads that promote other apps. When users install an app from the shown ad, the referring app can get a bonus. But in Cheetah Mobile's case according to Kochava, it was demonstrated that the company has been tricking apps into thinking that they should be the recipient of bonuses for referrals when in reality, Cheetah Mobile's apps played no role in referring the user to download an application.
This fraudulent scheme makes Cheetah Mobile to get money from both Google and the developers who monetized their app via advertisements.
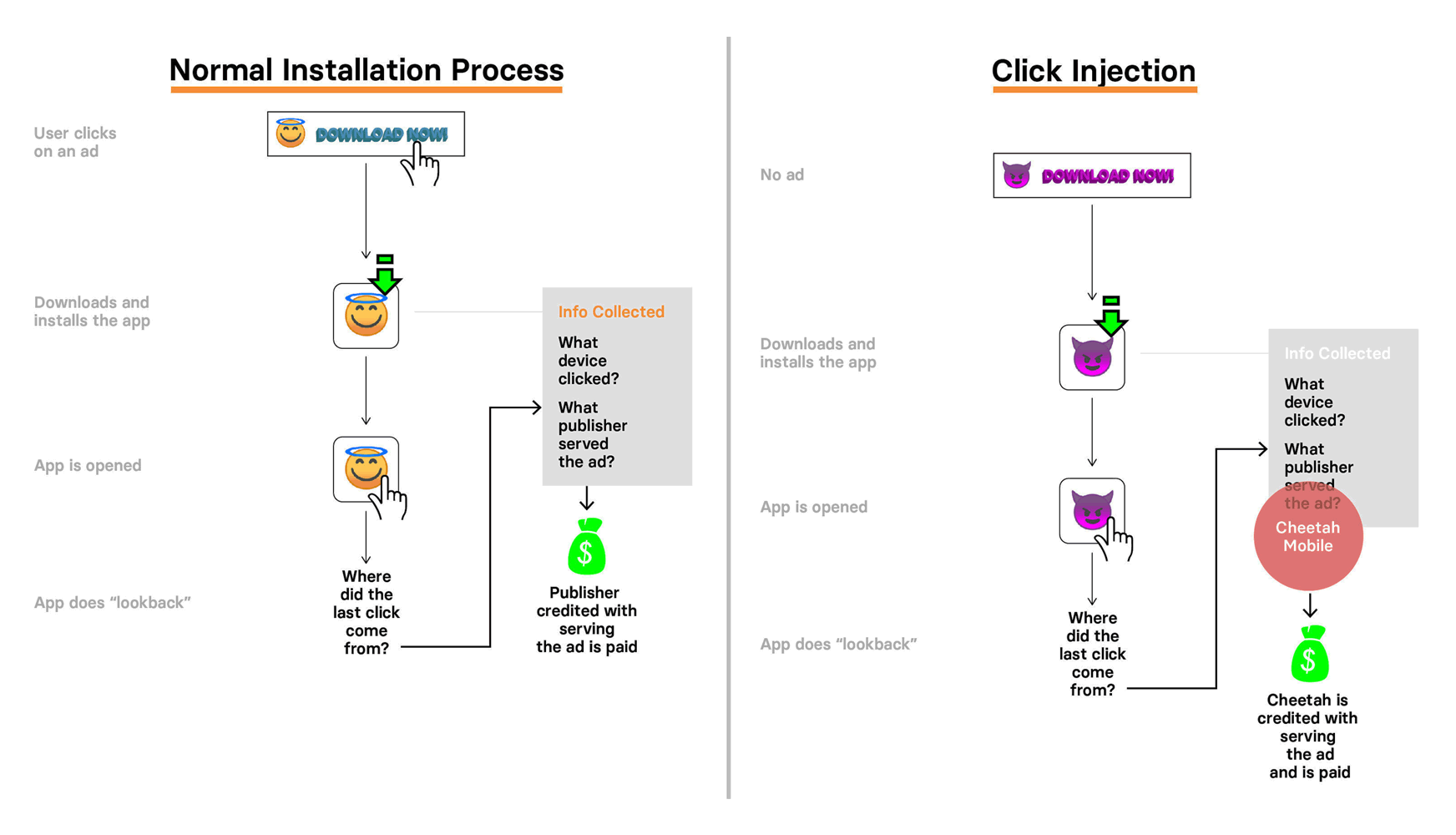
This type of fraud is known as 'click injection'.
With this method, apps on a user’s phone create fake clicks to fraudulently claim attribution. In other words, it's a more sophisticated form of click-spamming.
Here, apps that use this method publishes apps which use something called 'install broadcast'. Every Android app broadcasts status changes to the device, including to other apps. These status broadcasts are sent when apps are downloaded, installed, or uninstalled.
This feature is handy for creating a connection between different apps, by allowing apps to streamline login with a deep link to a recently installed password manager, for example, or giving users more direct options to transfer into a specific web browser, and so on.
Since any app can "listen in" to these broadcasts, fraudsters can detect when other apps are downloaded on a device, to then trigger clicks right before the install completes and receive the credit for the installs. This is where Kochava accused Cheetah Mobile.
As with any types of fraud, this click injection method can can appear like legitimate ad interactions to marketing analytics systems, making engagements faked with click injection very difficult to identify individually.
However, when looking at the ad campaigns as a whole, a pattern emerges. In this case, Cheetah Mobile's apps are connected to a series of websites on a network of front and shell companies in Cyprus, Malta, British Virgin Islands, Croatia, Bulgaria, and elsewhere.
Following the report, Google took action and removed many of those dubious apps. And for Cheetah Mobile, its stock went down about 30 percent as a result.
Cheetah Mobile said in a press release that it was investigating the allegations.