Threat actors and cybersecurity experts are always in a cat-and-mouse game. They will continue to best one another, in an never-ending war of supremacy.
Cybersecurity experts learn from the trends, and try to counter malware and threats by developing tools and systems, as well as ways to prevent infection to happen, or to thwart them completely before they can ever infect.
Malicious actors on the other hand, also have tricks under their sleeves, in which they learn from cybersecurity experts and people, and seeks ways to bypass their knowledge.
And this time, threat actors are increasingly shifting to "exotic" programming languages, in order to better circumvent conventional security protections, evade analysis, and hamper reverse engineering efforts.
That according to a report from BlackBerry.
As explained by Eric Milam, the company's Vice President of Threat Research:
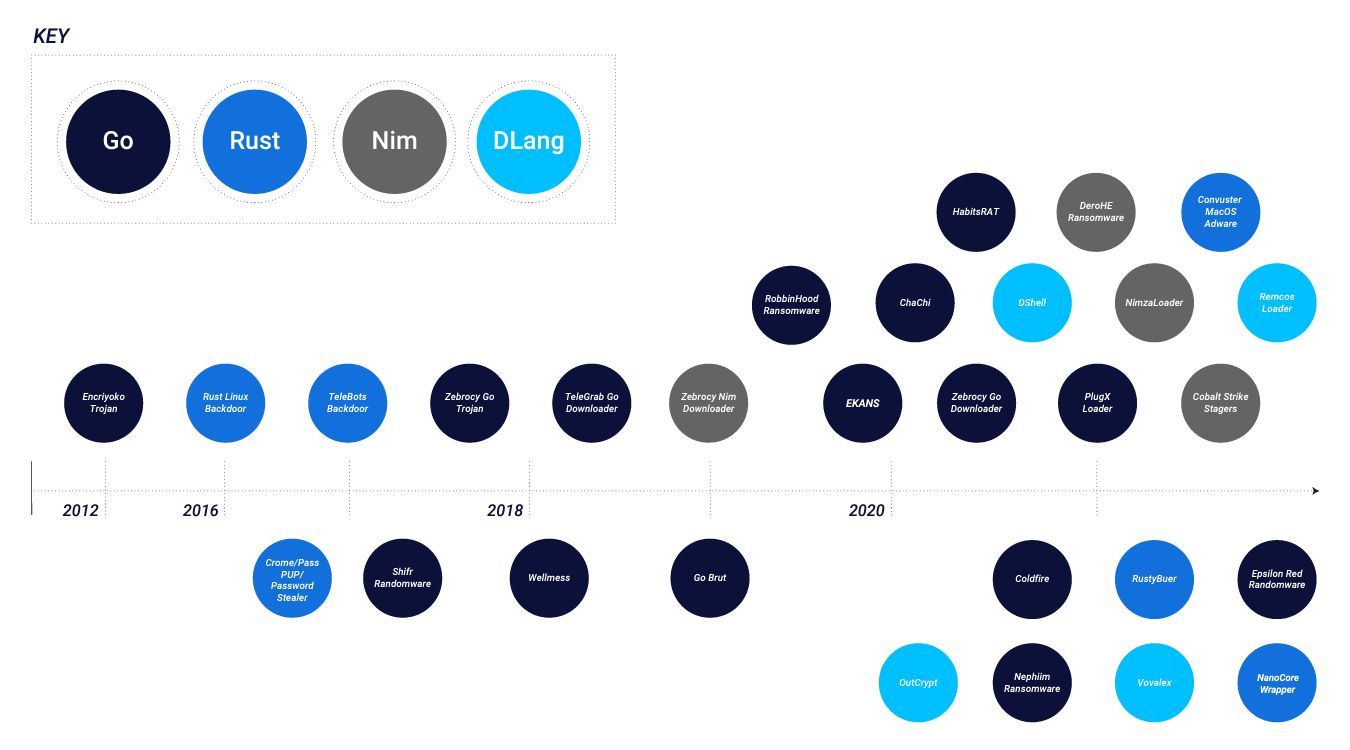
Some of the prominent examples of the "exotic" languages, and the malware written in them, include:
- DLang: DShell, Vovalex, OutCrypt, RemcosRAT.
- Go: ElectroRAT, EKANS (aka Snake), Zebrocy, WellMess, ChaChi.
- Nim: NimzaLoader, Zebrocy, DeroHE, Nim-based Cobalt Strike loaders.
- Rust: Convuster Adware, RustyBuer, TeleBots Downloader and Backdoor, NanoCore Dropper, PyOxidizer.
"These uncommon programming languages are no longer as rarely used as once thought. Threat actors have begun to adopt them to rewrite known malware families or create tools for new malware sets," the research said.
While binaries written in these languages can appear more complex, convoluted, and tedious when disassembled, the researchers said that by using these language, malicious actors can pivot by adding additional layers of obfuscation.
Since these "exotic" languages are relatively new, older malware that is written in traditional languages like C++ and C#, has been retooled and rewritten can evade detection by endpoint security systems.
"The user-friendly nature of some languages can also drastically improve both ease of development and the quality of life of the developer."
This is why new languages can often come with a higher degree of security consideration, and also with features, like memory-safe programming by design.
This is why the programs written using the same malicious techniques but in a new language may not be "detected at the same rate as those written in a more mature language," BlackBerry researchers concluded.
"The loaders, droppers and wrappers [...] are in many cases simply altering the first stage of the infection process rather than changing the core components of the campaign. This is the latest in threat actors moving the line just outside of the range of security software in a way that might not trigger on later stages of the original campaign."
It should be noted that malware developers are at their core software engineers. This fact is often overlooked by the developer community.
And this war, waged and commencing through screens, the internet and keyboards, may be invisible. It may make no devastating sound, but the damage it creates, can send waves of catastrophes that cripple many real-world instances.
"The everchanging threat landscape, along with the proliferation of malware written in what were once considered niche languages, means that security software vendors and developers must stay ahead of the curve or risk being overrun with new threats that they are unable to detect and mitigate."