
Software flaws are put into different categories based on their severity.
And 'Zerologon' flaw on Microsoft Windows operating system could easily top most of them, due to the fact that it allows attackers to infiltrate enterprises by gaining administrative privileges, giving them access to companies’ Active Directory Domain Controllers (DCs).
Zerologon is a privilege-escalation issue (CVE-2020-1472) with a Common Vulnerability Scoring System (CVSS) score of 10 out of 10. This makes it very critical in severity.
The flaw was fixed in Microsoft’s August 2020 security updates, which also patched the 20-year-old spooler bug. However, people are already creating public Proof-of-Concepts (PoC) exploits for the flaw on GitHub, meaning that hackers can use them to initiate hacking campaigns.
This is why the researchers at a Dutch security company Secura B.V. who first discovered the flaw, published technical details of the vulnerability in a whitepaper.
Related: Microsoft Patched A Windows Server Bug That Was Around Unnoticed For 17 Years
The Zerologon flaw happened to reside in the Netlogon Remote Protocol, available on Windows Domain Controllers, which is used by the operating system for various tasks related to user and machine authentication.
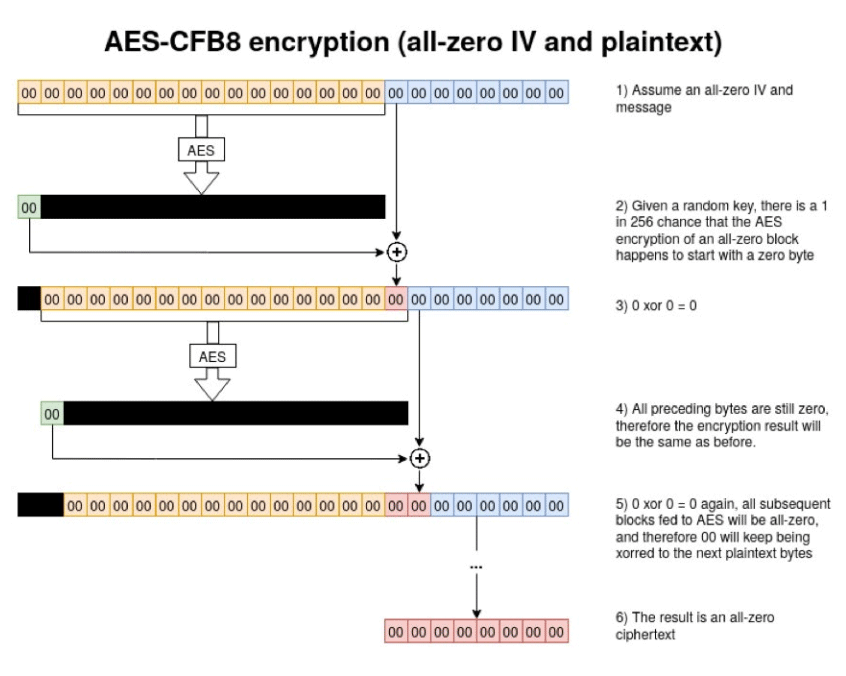
Specifically, the issue exists in the usage of AES-CFB8 encryption for Netlogon sessions.
The AES-CFB8 standard requires that each "byte" of plaintext to have a randomized initialization vector (IV), in order to block hackers from guessing passwords. However, Netlogon’s ComputeNetlogonCredential function sets the IV to a fixed 16 bits.
In other words, the IV is not randomized, meaning that hackers could decipher the text by taking advantage of the weak cryptographic algorithm used in Netlogon's authentication process.
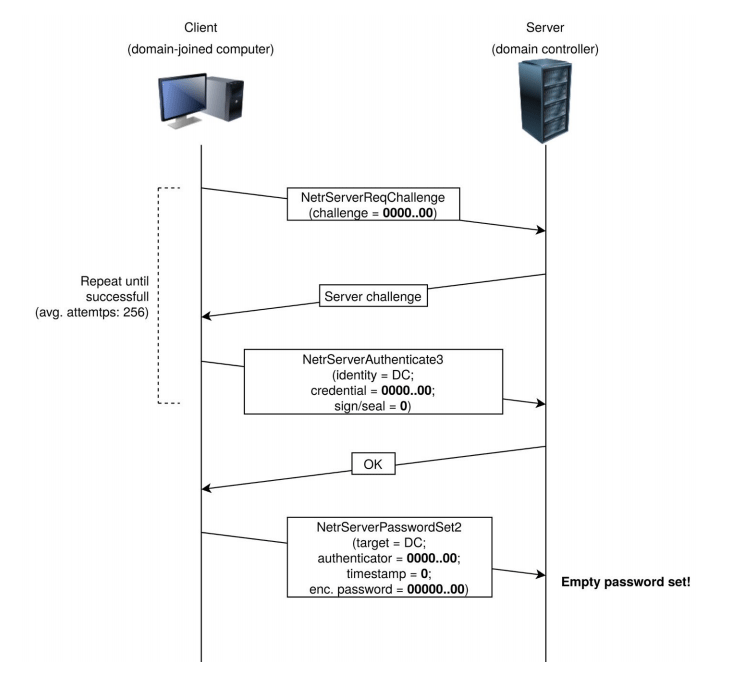
To exploit the flaw, hackers could try sending a number of Netlogon messages in which various fields are filled with a bunch of zeroes, so they can bypass the authentication measures, and access and change the computer password of the domain controller that is stored in the Active Directory (AD), the researchers said.
“Due to incorrect use of an AES mode of operation it is possible to spoof the identity of any computer account (including that of the [Domain Controller] itself) and set an empty password for that account in the domain,” Secura researchers said.
If the hack is a success, hackers can impersonate the identity of any machine connected to a network when attempting to authenticate to the Domain Controller. They can also disable security features in the Netlogon authentication process, or even change a machine's password on the Domain Controller's Active Directory
This can enable the hackers to initiate further attacks, including a complete takeover of a Windows domain, the researchers said.
Making things even worse, the entire process of the attack can be done in three seconds.
In addition, there are no limits to how hackers can use the Zerologon attack.
If most hacks happened after hackers managed to plant malicious software into a system in one way or another, Zerologon simplifies the process of hacking because hackers aren't required to do the tedious process of planting a malicious software.
"This attack has a huge impact," the Secura team said. "It basically allows any attacker on the local network (such as a malicious insider or someone who simply plugged in a device to an on-premise network port) to completely compromise the Windows domain."
Another way of saying it, according to the researchers in a blog post, the flaw allows hackers to become instant admins.
With PoC exploits have been made available on GitHub, Secura, other security researchers, as well as the U.S. government authorities are urging administrators to apply Microsoft’s August patches. These patches address the problem by enforcing Secure Netlogon Remote Protocol for all Windows servers and clients in the domain.
It should be noted though, that in order for exploit this Zerologon vulnerability, hackers must first launch the attack from a machine inside the same local-area network (LAN) as their target.
What this means, the attack is possible only when the hackers are already having a foothold inside the targeted network. If hackers are still logged outside the network, the hack is impossible.
Microsoft for its part is addressing the vulnerability in a phased rollout.
The initial rollout started with Windows updates being released on August 11, 2020. This is a temporary patch, which makes the Netlogon security features (the feature that Zerologon is disabling) a mandatory for all Netlogon authentications. This effectively breaks Zerologon attacks.
The second phase, is planned to be released on the first quarter of 2021, as an “enforcement phase.”
The patching is done in steps because it's not an easy task for Microsoft, as the company had to modify how billions of devices are connecting to corporate networks.
If rushing things, Microsoft can effectively disrupt the operations of a lot of companies.
To help companies, Secura has released a Python script that can tell administrators if their Domain Controller has been patched correctly.
Related: Microsoft Finally Fixed A Windows Bug, Two Years After It Was Discovered