
People can go to great lengths to get what they want. And when it comes to cryptocurrencies, people can indeed get 'creative' in order to mine them.
A campaign discovered by security researchers at BlackBerry’s cybersecurity subsidiary Cylance, shows how cybercriminals can hide malware inside WAV audio files, using a method called steganography.
Steganography is the practice of concealing a file, message, image, or video within another file, message, image, or video. In this case, bad actors are obfuscating malicious code in plain sight.
According to the researchers in a Cylance web post:
The WAV files in question can be delivered to unsuspecting victims through targeted phishing emails.
While some of the WAV files do produce music, they are actually the vector to distribute malicious payloads to infect the host to mine the Monero cryptocurrency. Other payload includes a Metasploit code used to establish a reverse shell.
"Both payloads were discovered in the same environment, suggesting a two-pronged campaign to deploy malware for financial gain and establish remote access within the victim network." the researchers added.
The WAV file loaders can be grouped into three categories:
- Loaders that employ Least Significant Bit (LSB) steganography to decode and execute a PE file.
- Loaders that employ a rand()-based decoding algorithm to decode and execute a PE file.
- Loaders that employ rand()-based decoding algorithm to decode and execute shellcode.
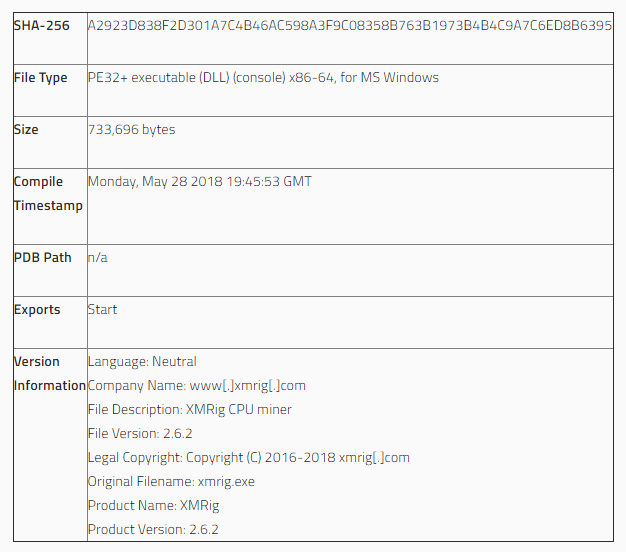
Each of the approach allows the attacker to execute code from an otherwise benign file format. These techniques demonstrate how executable content could theoretically be hidden within any file type, provided the attacker does not corrupt any of the structure or the processing of the container format.
"Adopting this strategy introduces an additional layer of obfuscation because the underlying code is only revealed in memory, making detection more challenging," the researchers said.
Steganography loader have been employed on WAV files before. Most notably, was through the threat group Turla (Urobos). This was the first instance of audio files being exploited to inject cryptocurrency mining malware.
Back in April 2019, Cylance has also published a report that describes how the OceanLotus Threat Group leveraged steganography to hide malicious backdoor payloads within image files.
These findings show how threat actors are adopting more and more sophisticated obfuscation techniques as their strategy continuously evolve to evade detection and exposure.
These should certainly heighten the need for people to improve their security infrastructure and watch out for such attacks.