
Computers run on software, and software can have flaws that are yet to be found. It's just a matter of time of who will discover the flaws first.
If hackers found them first, they can exploit the flaws and cause damage to targets. But if researchers found them first, they can help patch the issue so hackers can never exploit them. But what can happen if those flaws happened to be found on antivirus solutions, the very software meant to thwart cyberattacks in the first place?
This time, researchers have disclosed significant security weaknesses in popular software applications that could be abused by hackers.
As detailed by researchers from the University of Luxembourg and the University of London, hackers can circumventing the protected folder feature offered by antivirus programs to encrypt files, using a method called the 'Cut-and-Mouse" attack, and then disable their real-time protection by simulating mouse "click" events, using what's called the 'Ghost Control'.
Together, the twin attacks can deactivate antivirus protections, allowing malicious actors to take control of white-listed applications to perform nefarious operations on behalf of the malware to defeat antivirus defenses.
On their research, it is said that:
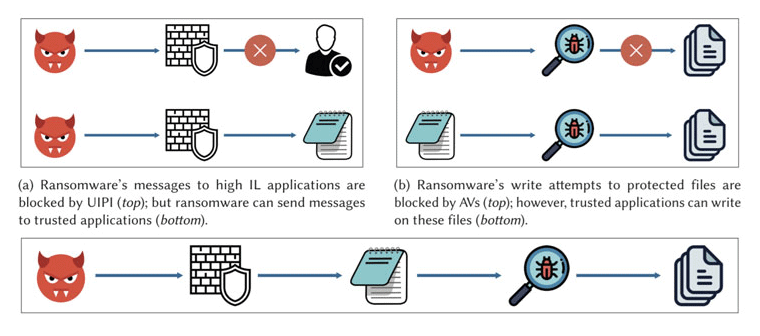
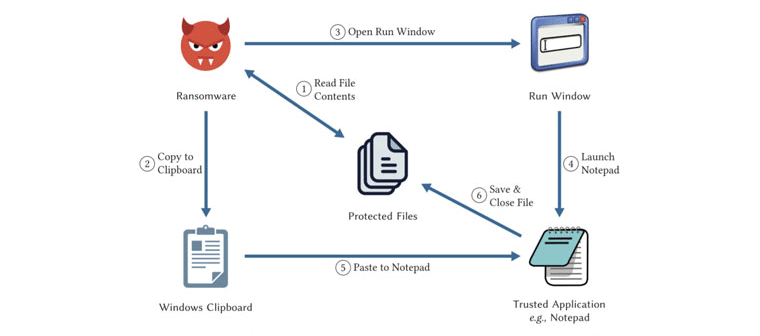
According to the researchers, malicious code could be used to control a trusted application, like the Notepad, in order to perform write operations. It's through this action that the hackers can encrypt victims' files. Hackers can also read the files and folders, to then encrypt them inside the victims' memory, and copies them to the system clipboard.
The files are then stored in protected folders, and can only be unlocked using an encryption key.
Making things worse, the ransomware can also launch Notepad or Paint to overwrite the folder contents with the clipboard data, meaning that the attack can be used to destroy files permanently.
The researchers tested the twin attacks on 29 different antivirus software, and found that 14 of them are vulnerable to Ghost Control attack while all 29 of them are found vulnerable to Cut-and-Mouse.
The researcher found this malware when they questioned themselves whether current defense mechanisms trusted all actions coming from a users' mouse input and trusted apps like Notepad by default. This is questioning whether malicious actions could pose themselves as harmless by piggybacking trusted apps and inputs, in a VIP-like approach.
The team suggested that apps like Notepad can be controlled as a puppet, and mouse clicks can be simulated.
It's only after a year that the researchers decided to share their findings to the public.
This is because Dr. Ziya Alper Genç, Prof. Gabriele Lenzini and Dr. Daniele Sgandurra have informed the potentially affected antivirus software providers, and offered their assistance to resolve the security issue if confirmed and still present, as reported by a post by the University of Luxembourg.
Out of the 14 vendors contacted, some of them have immediately released a fix to mitigate the vulnerability, while others acknowledged the issue and promised to be solve the issue as quickly as possible.
“Antivirus software providers always offer high levels of security, and they are essential element in the everyday struggle against criminals. But they are competing with criminals which have now more and more resources, power, and dedication. This is why the role of academic research in vulnerability discovery, if conducted ethically and with high standard of professional conduct, can support security companies to be one step ahead of the criminals”, said Lenzini.
“The University and the SnT have always prioritised the importance of interdisciplinary research,” informs Prof. Lenzini. “This latest discovery emphasises the success of this approach, as the vulnerability was discovered because of truly out-of-the-box thinking for the field of cybersecurity.”
“The business of security suffers a known curse: that if security works nothing bad happens. So, it is often easy to forget that security defenses must be always on. This is why is important that us researchers remain capable to take nothing for granted, because when security fails it may be too late.” said Dr. Genç.
“This research also makes it clear that approaching cybersecurity from a holistic perspective is valuable. In addition, our disclosure and engagement with the impacted companies demonstrates how scientists can tackle these topics with the highest ethical standards.”
Further reading: 'Every Major Anti-Malware Product' Could Be Exploited, Research Found