
One of the ways for hackers to go in and out undetected, is by tweaking the security features of their victim's device security settings.
It's like saying a thief wanting to break into a house, but instead of avoiding the security camera, the thief tricks the camera to make it see elsewhere to allow the thief to lock pick freely.
On computer systems, this is called tampering to the security system, and Microsoft wants to end that.
Microsoft has officially announced the general availability of its Tamper Protection feature for all Windows Defender Antivirus services.
What it essentially does, is to thwart any attempts made by cybercriminals to break the real-time anti-malware defenses incorporated in Windows operating system.
This Tamper Protection safeguards users against "malicious and unauthorized changes to security features, ensuring that endpoint security doesn’t go down."
Using the administrator privilege, Windows users can access the setting as follows:
- Open Windows Security.
- Select 'Virus & threat protection' settings menu.
- Turn on the Tamper Protection under the 'Virus & threat protection settings' option.
The feature was originally launched in December 2018 for Windows Insiders users, where the community devoted to testing pre-release builds of the operating system before Microsoft makes them public.
Microsoft devices to roll out the feature to all users after acknowledging many Trojans and banking malware have targeted PC users by disabling the Windows Defender to gain elevated system privileges.
“With this protection in place, customers can mitigate malware and threats that attempt to disable security protection features,” Microsoft said.
When Tamper Protection is enabled, any tampering attempt should be detected on endpoints, which will raise an alarm in the Microsoft Defender Security Center.
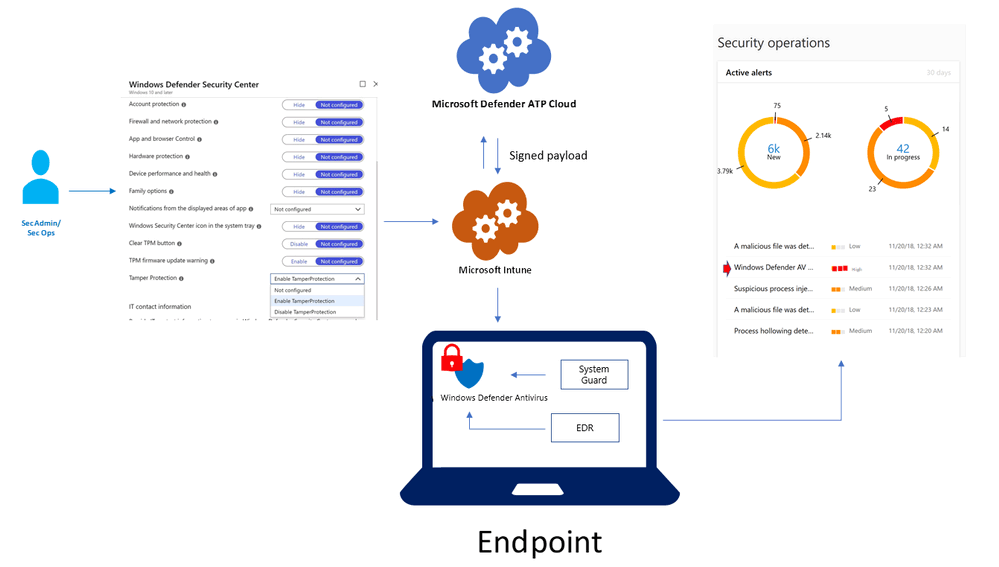
For enterprise Windows users, the Tamper Protection can also be deployed and managed centrally and securely through Microsoft Intune, in a way similar to how users manage other endpoint security settings.
From here, the feature can be enabled for the entire organization, or through device and user groups.
When an administrator enables the policy in Microsoft Intune, the tamper protection policy is digitally signed in the backend. And according to Microsoft, this happens before it’s sent to endpoints.
This way, the endpoint can verify the validity and intent, and establishing that it is indeed a signed package that only those with Microsoft Intune administrator rights can control. With the right level of reporting, security operations teams should have control to better detect any irregularities.
"We believe it’s critical for customers, across home users and commercial customers, to turn on tamper protection to ensure that essential security solutions are not circumvented."