
People use their smartphones for both work and personal life, as well as many things in between. This is a fact that cannot be denied.
With smartphones becoming increasingly powerful, and as more of the society demands their usage for easing many things in life, tech manufacturers should ensure that user data is safe no matter what, and that personal data that resides inside a phone, won't be accessible by unauthorized parties.
While most attempts to secure data comes through the means of securing connection and doing encryption, little do tech companies improve the very first thing that prevent a phone breach.
And that is improving the security of the lock screen.
Phones can use a lock screen to prevent anyone other than the user with physical access to a phone to peak inside it.
Android is the most widely-used operating system for mobile phones, and on Google Pixel devices, the lock screen had a serious issue.
According to cybersecurity researcher David Schütz in a blog post, a fully patched Google Pixel 6 and Pixel 5 smartphones allowed anyone with physical access to the device to unlock it.
Schütz said that managed to bypass the lock screen using an extremely simple procedure.
Schütz said he discovered the flaw by accident when his Pixel 6 ran out of battery, and that he entered his PIN wrong three times.
His phone then asked him to use recover the locked SIM card using the PUK (Personal Unblocking Key) code.
PUK is often used to reset a lost or forgotten PIN number. The PUK code can be obtained from wireless provider, or through the wallet-sized card the original SIM card came from. By entering the PUK, users can unlock the SIM card, and is then allowed to enter a new PIN number. Wrongfully entering PUK ten times would result in a total lock of the SIM
Schütz entered the correct PUK, but when he did that on his Pixel 6, and much to his surprise, the lock screen disappeared.
His phone stopped asking for the lock screen password, and instead only requested a fingerprint scan.
Android devices always request a lock screen password or pattern after reboot for security reasons, so going straight to fingerprint unlock wasn't normal.
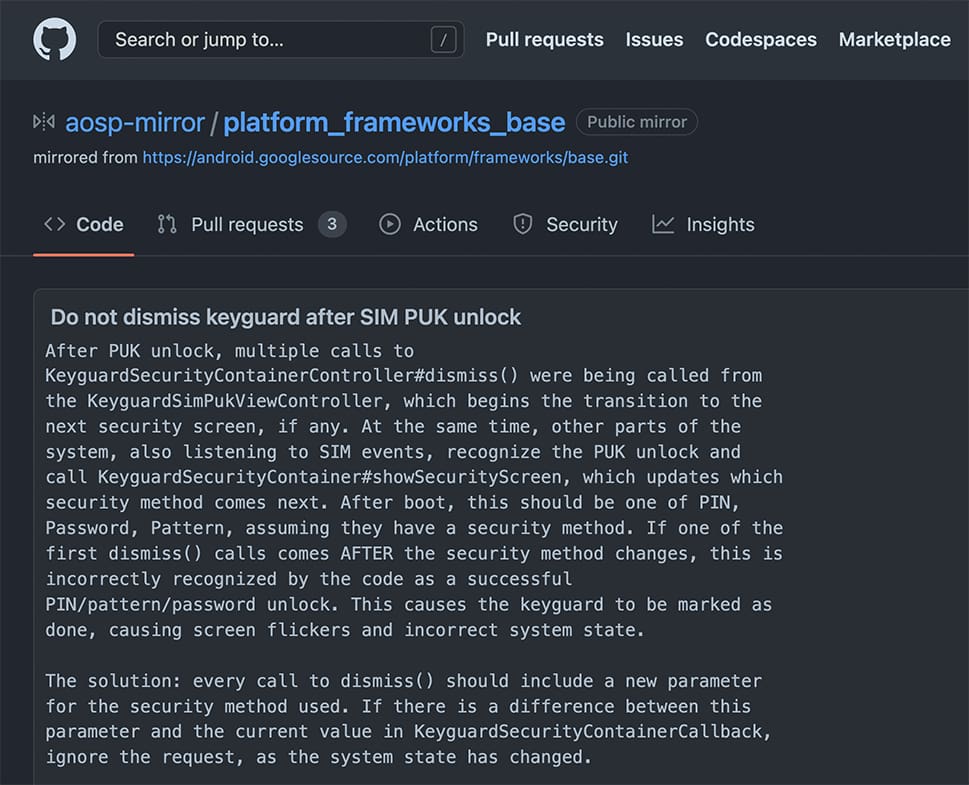
What happened here is that, the issue was caused by the lock screen being wrongfully dismissed after a SIM PUK unlock due to a conflict in the dismiss calls impacting the stack of security screens that run under the dialog.
When Schütz entered the correct PUK number, a "dismiss" function was called twice, once by a background component that monitors the SIM state, and once by the PUK component.
This caused not only the PUK security screen to be dismissed, but also the next security screen in the stack, which is the lock screen, followed by whatever screen was next queued in the stack.
If the phone doesn't have a lock screen, the phone would be unlocked directly.
The exploit was an extremely easy process that took him only a few minutes.
As a researcher, Schütz was curious, and continued experimenting.
He then tried reproducing the flaw without rebooting the device and starting from an unlocked state. Schütz found that it was possible to bypass the fingerprint prompt, too, going straight to the home screen.
The impact of this security vulnerability is quite broad, affecting all devices running Android versions 10, 11, 12, and 13.
Physical access to a device is a strong prerequisite. However, the flaw still carries severe implications for people with abusive spouses, those under law enforcement investigations, owners of stolen devices, etc.
The attacker can simply use their own SIM card on the target device, disable biometric authentication (if locked), enter the wrong PIN three times, provide the PUK number, and access the victim's device without restrictions.
This issue has been around for at least six months.
Schütz reported the flaw to Google in June 2022, and although the tech giant acknowledged the reception and assigned a CVE ID of CVE-2022-20465, they didn’t release a fix until November 7, 2022.
Google patched the issue by including a new parameter for the security method used in every “dismiss” call so that the calls dismiss specific types of lock screens and not just the next one in the stack.
Schütz was awarded $70,000 for his finding, despite the fact that the issue was a duplicate.