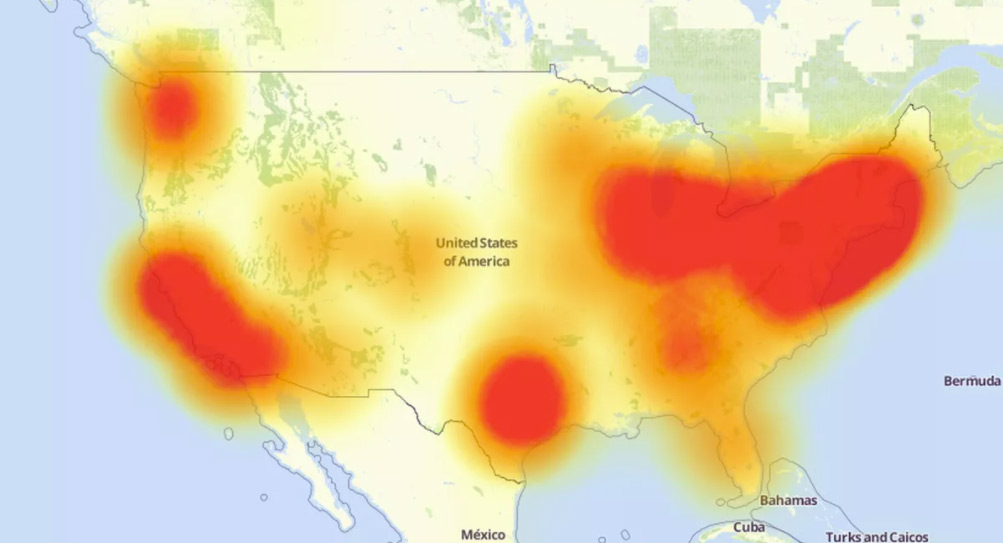
A large-scaled of Distributed Denial of Service (DDoS) attack to DynDNS has took down a large portion of the internet.
Using DDoS, hackers have attacked its central server by choking it more requests than it can handle. DynDNS provides DNS for many popular websites like Twitter, Spotify, SoundCloud, Reddit and others. And when it was hit by DDoS, people that tried accessing those sites saw a message saying that they weren't available.
DynDNS is responsible for turning an internet protocol (IP) address into a readable website. What the hackers did, according to DynDNS, was using connected devices (routers, smart hubs, thermostats, smart locks, etc.) in the Internet of Things (IoT) to attack Dyn, resulting in servers that couldn't pass along requests due to massive increases in activity.
When DynDNS went down, it took down every site that uses its managed DNS service. The first attack started at 11.10 UTC, which then peaked at 1.2Tbps.
The cause was the Mirai malware. It turned networked devices running Linux into bots. The Mirai botnet was first found in August 2016 by MalwareMustDie, a whitehat malware research group.
The source code for Mirai has been published in several hacker forums as open-source. Since the source code was published to the public, the techniques have been adapted in other malware projects.