Researchers from Check Point said that targeted attacks have used TeamViewer to steal financial information.
The campaign is specifically designed to target government officials and embassy representatives in Nepal, Guyana, Kenya, Italy, Liberia, Bermuda and Lebanon.
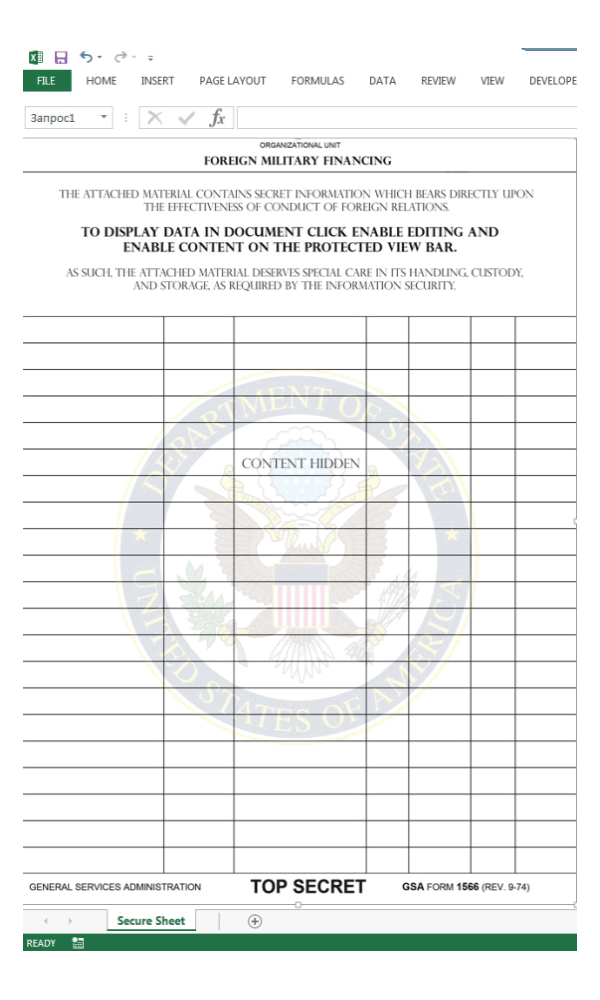
What the hackers did, was sending phishing emails that claims to come from a legitimate source, with a "Top Secret" document from the United States.
To make the emails look legitimate, they contain the subject line like "Military Financing Program" and the .xlsm document attached to the message has been crafted with a logo from the U.S. Department of State.
Upon downloading and opening the attachment, victims were prompted to enable macors, which is a common method used by hackers to gain access to victims' computer.
Allowing this would extract a legitimate AutoHotkeyU32.exe file, and a a malicious TeamViewer DLL.
The executable program is used to send a POST request to the attacker's command-and-control server, as well as download AHK scripts able to take a screenshot of the target PC and steal computer information which is then sent to the attacker's command-and-control server.
And as for TeamViewer, it's a legitimate software often used in the enterprise to retain remote access to PCs and to share desktops. However, with its abilities , the software has also been commonly used by both cyberattackers and scammers at large to gain fraudulent access to systems.
Here are the modified functionalities, according to Check Point's finding:
- Hiding the interface of TeamViewer, so victims would not know it is running.
- Saving the current TeamViewer session credentials to a text file.
- Allowing the transfer and execution of additional .
.exeor.dllfiles.
As a result, the victims' computers can be compromised, with the hackers capable of stealing sensitive information, covert surveillance, or compromising online accounts.
But because targets include those in the finance sector, the attacks suggest that the threat actors are more finance related rather than potentially politically motivated.
This kind of attack is common, but has the vector of attack has changed throughout the years. In addition, the malicious TeamViewer DLL has also been adapted, as it switches from stealing basic information to the more modern command-and-control server infrastructure.
The researchers say that there is evidence of the threat actor behind the campaign as being Russian, due to the link of an avatar connected to a Russian underground forum user known as EvaPiks.
"By investigating the entire infection chain and attack infrastructure, we were able to track previous operations that share many characteristics with this attack’s inner workings. We also came across an online avatar of a Russian speaking hacker, who seems to be in charge of the tools developed and used in this attack," said Check Point on its report..
Check Point believes that the threat actor and/or the developer of the tools used in the campaign points to underground carding with motives like exchanging stolen financial information, such as credit card data.