
Another day, another threat. As long as money can be made, hackers will be there.
Google is behind Android, and it has been working hard in improving its ecosystem. The company has taken increasingly sophisticated steps to keep malicious apps out of its Google Play Store. But still, malicious actors are often smarter, as this time, another round of takedowns happened after Google was made aware of some malicious activities.
In what involved around 200 apps and more than 10 million potential victims, it shows that the longtime problem on Google's Play Store remains far from solved.
Researchers from the mobile security firm Zimperium zLabs said that the massive campaign dubbed the 'GriftHorse' has been happening since at least November 2020, and that it has potentially cost victims hundreds of millions of dollars.
The techniques involve some common strategies, like premium SMS fraud.
But the researchers said that GriftHorse is significant, because the malicious actors were able to string together well-known approaches to make a very effective campaign.
"These malicious Android applications appear harmless when looking at the store description and requested permissions, but this false sense of confidence changes when users get charged month over month for the premium service they get subscribed to without their knowledge and consent," said researcher Aazim Yaswant in the Zimperium report.
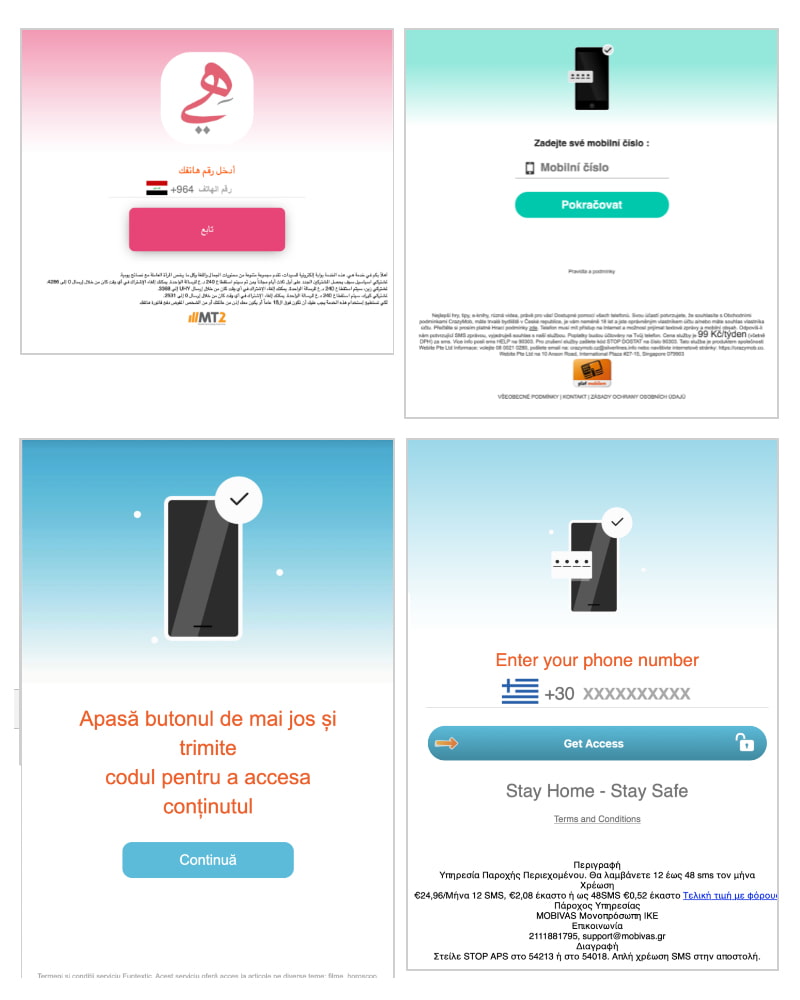
As is often the case, the malicious actors hide their campaign inside benign-looking apps across all categories, and market them to Google Play Store. After victims download and install the apps, the victims would then receive notifications, up to 5 notifications per hour, prompting them to "confirm" their phone number.
That, in order to claim a prize.
And users can supposedly claim that "prize," after the app loads a page through an in-app browser.
This technique is common, as hackers can hide their apps' malicious intentions out of the apps' codes. This way, the hackers can buy some times before Google discovers it, if it ever does.
If users continue and enter their numbers, the apps would quickly sign them to a monthly charge of about $42 through the premium SMS services feature.
While all the techniques have been used many times before, the malicious actors were able to pull them off into an effective campaign that targets users in more than 70 countries.
“This is impressive delivery in terms of scale,” says Richard Melick, Zimperium's director of product strategy for end-point security. “They pushed out the full gauntlet of techniques across all categories; these methods are refined and proven. And it's really a carpet-bombing effect when it comes to the quantity of apps. One might be successful, another might not be, and that's fine.”
Zimperium is a member of Google's App Defense Alliance, a coalition of third-party companies that help Google in keeping the Play Store safe from malware.
After the company disclosed the GriftHorse campaign, Google swiftly removed the hundreds of apps from the Play Store. Google also banned the corresponding app developers.
While this should make Google Play Store safer, for now, it should be noted that the apps are still available for download through third-party app stores.
What makes this campaign so effective, is not only because the malicious actors managed to tailor the multiple widely-used strategy into their campaign, but also because the fact that premium SMS fraud campaigns are not typically noticed until the victims' next bill.
"This means one of their first victims, if they have not shut off the scam, has lost more than €200 at the time of writing. The cumulative loss of the victims adds up to a massive profit for the cybercriminal group," the researcher explained.
Due to the facts, hackers won't stay back. Because they know how effective this campaign can be, the researchers emphasized that new variations will show up sooner than later.
"The numerical stats reveal that more than 10 million Android users fell victim to this campaign globally, suffering financial losses while the threat group grew wealthier and motivated with time."
“These attackers are organized and professional. They set this up as a business, and they're not just going to move on,” says Shridhar Mittal, Zimperium's CEO. “I'm certain this was not a one-time thing."