
Hackers use malware to disrupt, or to steal credential information from compromised systems.
Since user information has become a commodity, hackers see this as an opportunity to conduct some profiting business on their own. One of which, is by distributing a malware called the 'Raccoon Stealer'.
First discovered in 2019, Raccoon is a MaaS (Malware-as-a-Service) "infostealer", where others can use it for a fee.
As a business, the malware is a product that has an administrative panel, customized functionality, and even has its own technical support team and updates that include bug fixes and new features additions.
With various subscription model that is based on either the length of the subscription or the robustness of the features, this Raccoon malware is enjoying an increased popularity on hacking forums and being sold on the dark net.
That according to a report from researchers at CyberArk
Read: 'Raccoon' Is A Malware-As-A-Service That Steals User Information, Researchers Said
"While infostealers often target high value information, they generally aren’t sophisticated and are usually sold on hacking forums for anywhere from a few dollars to a couple of hundred dollars."
Cyberark security researchers are warning from the resurgence of the malware Raccoon, mainly because the malware can also steal banking information as well as cryptocurrency data by exploiting flaws on more than 35 browsers and 60 applications in total, including email clients.
They include:
Browsers
Google Chrome, Google Chrome (Chrome SxS), Chromium, Xpom, Comodo Dragon, Amigo, Orbitum, Bromium, Nichrome, RockMelt, 360Browser, Vivaldi, Opera, Sputnik, Kometa, Uran, QIP Surf, Epic Privacy, CocCoc, CentBrowser, 7Star, Elements, TorBro, Suhba, Safer Browser, Mustang, Superbird, Chedot, Torch, Internet Explorer, Microsoft Edge, Firefox, WaterFox, SeaMonkey and PaleMoon.
Email Clients
ThunderBird, Outlook and Foxmail.
Cryptocurrency Wallets
Electrum, Ethereum, Exodus, Jaxx, Monero and Bither.
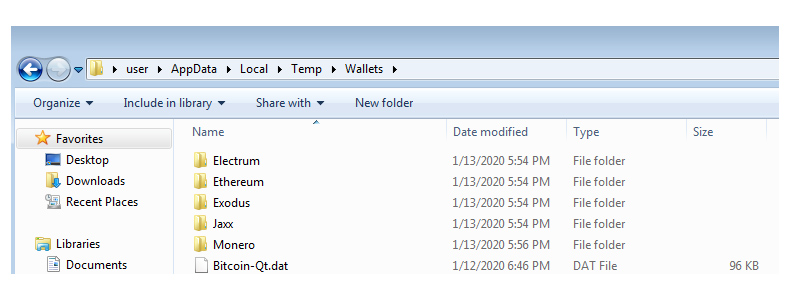
The malware works like this.
After hackers managed to infect victims by first making them fall to phishing campaign and exploit kits.
Once the malware is installed, it looks for files containing sensitive data that include and not limited to: cryptocurrency wallets, web browser cookies, browsing history, and autofill content. The malware then copies all of them to a temporary folder, to then extract and decrypt the data before sending it to its Command and Control server.
Making things worse, Raccoon also has the functionality to be used as a dropper, a feature that specializes in loading a second-stage malware payload onto a victim’s system.
What this means, it can download more malicious files and runs them.
"This kind of information stealer can cause a lot of damage to individuals and organizations. The attackers are looking for privileged credentials in order to achieve privilege escalation and lateral movement," said the researcher, adding that "what used to be reserved for more sophisticated attackers is now possible even for novice players who can buy stealers like Raccoon and use them to get their hands on an organization’s sensitive data."
CyberArk researchers said that Racoon is similar to other "as-a-service" offerings. As it is being developed and supported by a group, the malware continues to improve with each new version of the build is released.
Since the researchers started its analysis, Raccoon has included the ability to steal FTP server credentials from FileZilla, as well as login credentials from UC Browser.
In other words, as long as the malware remains active in development, there may not be an effective method of protection, except to be particularly wary with emails with attachments.