The Tor network consists of volunteers of thousands of relays that work together to conceal Tor users' location and usage from anyone else.
Due to Tor in preserving users' anonymity, Tor users can share just about any sorts of information less discreetly, and have less to worry about identity exposure. This fact makes Tor an alluring target for hackers who wish to obtain sensitive information.
And SystemBC is a RAT (remote administration tool) that can do this.
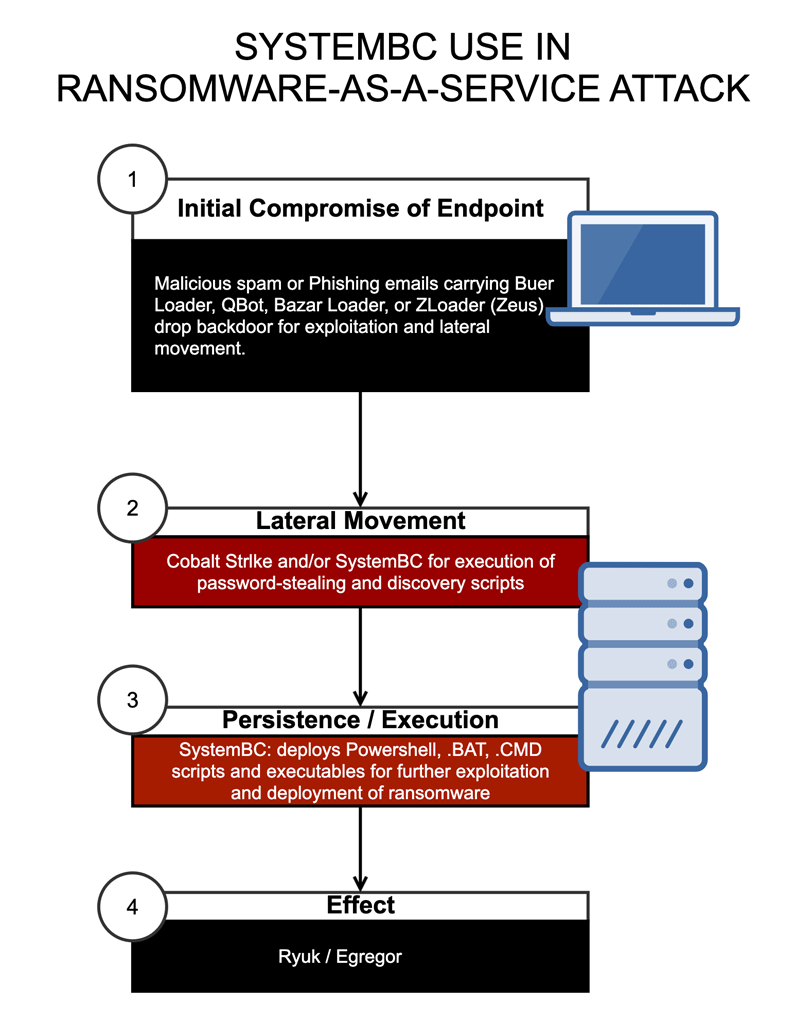
Reported as an off-the-shelf Tor backdoor, researchers at Sophos Labs have been tracking this ransomware tool that has been circulating on underground hacking forums.
SystemBC was first spotted in 2019, acting as both a network proxy for concealed communications. But it has then also become a RAT capable of executing Windows commands as well as delivering and executing scripts, malicious executable and dynamic link libraries.
So here, SystemBC has evolved to become a Tor proxy and remote control tool that serves as a backdoor that provides attackers with persistent connection to victims' systems.
On their investigation, the researchers at Sophos MTR's Rapid Response found that SystemBC was used in some Ryuk and Egregor ransomware attacks, and was often used alongside other post-exploitation tools such as Cobalt Strike.
In some cases, SystemBC RAT was also deployed to servers after attackers had gained access to administrative credentials in order to gain even deeper access to compromised targeted network.
When deployed, the tool copies itself into a randomly-named directory and file name within the ProgramData directory and schedules itself as a service, but this step is skipped if Emsisoft antivirus software (a2guard.exe) is installed on the victim's system.
If not, SystemBC will continue to then establish a connection to a command and control server using a beacon connection to a remote server based at one of two hard-coded domains, and a lightweight Tor client.
When trying to open persistent connection, the malware will first send one of the hardcoded domains, to then send an initial block of data. If successful, it will maintain an open socket, allowing continuous connection.
In a blog post explaining SystemBC, senior threat researcher Sean Gallagher and threat researcher Sivagnanam Gn at Sophos said that:
SystemBC is another instance of a ransomware-as-a-service (RaaS), a business model that has become increasingly popular among hardcore hackers.
This kind of approach has also become increasingly popular among cybercriminals due to the fact that it allows hackers to target multiple victims and working on them simultaneously.
Like Software-as-a-Service (SaaS), RaaS business model allows the developers of the malware to sell or lease their malware variants to affiliates who then use them to perform an attack. The RaaS business model makes malware attack campaigns possible even for non-computer-savvy persons.
And SystemBC here, is often deployed as an off-the-shelf tool.
According to the researchers, SystemBC can be purchased in underground forums.
Read: The Unfortunate World Where It Is Cheap And Easy To Become A Hacker