There is a saying that says Apple’s computers are largely immune to malware.
While that is incorrect, it's true that Macs and malware aren't all that common if compared to Windows. But still, malware can be anywhere, in all operating systems, old and new.
And this time, security researchers at Malwarebytes and Red Canary have found an “activity cluster” that has infected Mac computers across more than 150 countries as of February 17, with higher concentrations reported in the U.S., UK, Canada, France and Germany.
Calling it the 'Silver Sparrow', the malware mysteriously hid itself inside nearly 30,000 Apple computers.
Iinitially, the author of the malware is unknown, and its payload is yet to be discovered.
But what is certain is that, the researchers found a self-destruction mechanism that can remove traces of infection.
At this time, the malware comes as a surprise because it is capable of targeting Apple computers with the M1 chips.
Apple only introduced the chips back in November 2020.
Less than a year old, only a few vulnerabilities have been discovered.
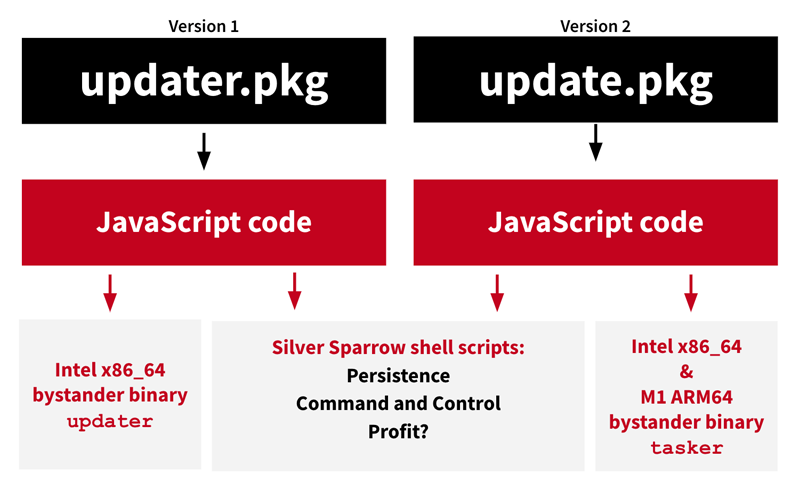
According to Red Canary in a blog post, this Silver Sprrow malware can also target older Macs that are powered by Intel processors.
This is because Silver Sparrow comes in two versions: one with a binary in Mach-object format compiled for Intel x86_64 processors, and another one has the Mach-O binary for the M1.
“Our investigation almost immediately revealed that this malware, whatever it was, did not exhibit the behaviors that we’ve come to expect from the usual adware that so often targets macOS systems,” noted Tony Lambert, an Intelligence Analyst at the Red Canary security firm.
Working with other security researchers from VMware Carbon Black, Lambert soon realized that Silver Sparrow is at this time, a novel strain of malware.
“The novelty of this downloader arises primarily from the way it uses JavaScript for execution—something we hadn’t previously encountered in other macOS malware,” shared Lambert.
“Though we haven’t observed Silver Sparrow delivering additional malicious payloads yet, its forward-looking M1 chip compatibility, global reach, relatively high infection rate, and operational maturity suggest Silver Sparrow is a reasonably serious threat, uniquely positioned to deliver a potentially impactful payload at a moment’s notice,” added Lambert.
What makes Silver Sparrow particularly unique when it was discovered, is its lack of functions.
First, despite having infected nearly 30,000 Apple's computers, the malware has no payload. This puzzled the researchers, simply because they have no idea about the intention of the malware and how is it going to infect the devices.
The malware has a malicious binary that is mysterious because it uses the macOS Installer JavaScript API to execute commands. This makes it difficult for the researchers to analyze installation package contents or the way that package uses the JavaScript commands.
But because the malware lacks the final payload, the researchers agreed that the malware may spring to action anytime.
Second, what makes Silver Sparrow also unique, is that it comes equipped with its own self-destruct mechanism.
While this is nothing new in a malware, the mechanism is more often reserved for high-stealth operations.
Given all of this, Silver Sparrow is uniquely positioned to deliver a potentially impactful payload at a moment’s notice, so we wanted to share everything we know with the broader infosec community sooner rather than later.
— Red Canary (@redcanary) February 19, 2021
Researchers have warned that Apple's transition from Intel to its own silicon M1 chip may make it easy for hackers to develop and introduce malware.
Fortunately in this case, after the finding, Apple quickly revoked the binaries.
What this means, it should theoretically keep the malware from ever installing itself again.
At this time, Silver Sparrow is the second known malware targeting Apple computers with the M1 processors. The first was bundled with the GoSearch22 extension, and was found less than week earlier.